Menu
Beat ransomware by saving your files to the cloud
A story written by Alina Simone in yesterday's New York Times scared the bejeebers out of me. Simone describes how her mother’s files were held for ransom by crooks, likely from Russia or Eastern Europe. Her mother's last backup was in May, so she was willing to pay the $500 – in bitcoins -- the hackers demanded to decrypt her files. The bad guys gave her seven days to pay, after which the price to decrypt would go up to $1,000.
How ransomware works
As Simone explains, the CryptoWall 2.0 virus that hit her mother's computer sneaks onto your machine when you click an email attachment or visit an infected web page, among other avenues of infection. While it's easy to say you need to be more careful when using your computer, the malware purveyors are adept at tricking us into some action that triggers their nasty payloads.
Just as businesses now have to assume their networks have been infiltrated by the bad guys, us everyday computer users must adopt the mentality that we will someday be hit by a virus, despite our best efforts to avoid it. So what can we do? Think like a Boy Scout/Girl Scout, and be prepared -- by saving your files to a cloud storage service.
How ransomware works
As Simone explains, the CryptoWall 2.0 virus that hit her mother's computer sneaks onto your machine when you click an email attachment or visit an infected web page, among other avenues of infection. While it's easy to say you need to be more careful when using your computer, the malware purveyors are adept at tricking us into some action that triggers their nasty payloads.
Just as businesses now have to assume their networks have been infiltrated by the bad guys, us everyday computer users must adopt the mentality that we will someday be hit by a virus, despite our best efforts to avoid it. So what can we do? Think like a Boy Scout/Girl Scout, and be prepared -- by saving your files to a cloud storage service.
How to ransom-proof your files
Cloud storage services such as Google Drive, Microsoft's OneDrive (formerly SkyDrive), Dropbox, and Apple's iCloud offer up to 10GB of free storage, which is sufficient to accommodate most people's needs. When you install the services' desktop app, you see its folder in Windows Explorer (called File Explorer in Windows 8), just like your Documents, Pictures, Desktop, and other folders.
Note that you'll need to encrypt and/or password-protect sensitive files before you save them to the cloud service. Tom's Guide provides step-by-step instructions for doing so in Windows and Microsoft Office. Alternatively, you could use a cloud storage service that encrypts automatically, such as Carbonite, which costs from $60 a year and has no storage limit, or SpiderOak, which offers up to 2GB of free encrypted cloud storage, and $10 a month or $100 a year for up to 100GB of encrypted storage.
SpiderOak's "zero-knowledge" privacy environment ensures that not even the company's employees can access your encrypted data. That's a pretty iron-clad guarantee, but if you prefer not to let your most sensitive files out of your possession, save encrypted versions of those files on a CD or DVD you keep under lock and key in your home or office.
(I've written about SpiderOak multiple times in the past, most recently on July 14, 2014, in "The pros and cons of cloud computing" and on October 21, 2014, in "Quick, simple fixes for everyday tech glitches.")
My backup strategy would probably be considered overkill by most people, but it is the result of having two laptops go kerflooey in relatively quick succession. In both failures, I lost only a handful of relatively unimportant files because my frequent-flyer job required that I be able to access my files from multiple machines in numerous locations.
Over the years I have created cloud-storage accounts on Google Drive, OneDrive, iCloud, Dropbox, and Box. Lately I've been using OneDrive to store my personal files and Dropbox for my work-related files. Nearly everything gets saved directly to at least one cloud service and then "backed up" to my local drive.
On the day the CryptoWall crooks try to extort a payment from me to decrypt my hard drive, I'll file a complaint with the Internet Crime Complaint Center, which is a joint effort by the U.S. Federal Bureau of Investigation and the National White Collar Crime Center. Then I'll reformat the machine's hard drive, reinstall Windows and my apps, and tell the bad guys to stick their bitcoins where the sun doesn't shine!
The FBI and other law-enforcement agencies recommend against paying such ransoms, although many people -- including NYT's Simone and her mother -- ignore this advice.
One last note on backups: Computer professionals advise that you create an image backup of your machine, which allows you to restore it quickly with apps and files in place. Over the years I've found that I spend too much time creating image backups I never need. Sure, it's good to know you've got a full backup at the ready in case of disaster, but the fix-on-failure approach has proven to be most efficient for me.
-----------------------------------------------------------------------
Were you 'crammed'? If so, your cell service provider may owe you money
Cramming is the practice perpetrated by some nefarious app vendors of sneaking their wares onto your phone or tablet and then charging a monthly fee that appears on your cell-phone bill. It's not at all uncommon for people to miss the charge and pay their bill without being aware that they've been hoodwinked.
In late 2013, AT&T, Verizon, Sprint, and T-Mobile agreed to stop allowing third parties to place such unauthorized charges on their customers' bills, as All Things D's Ina Fried reported in a November 21, 2013, article. Re/code's Amy Schatz explains in a December 31, 2014, post how to apply for a refund from two of the four carriers as part of a $160 million settlement with federal and state government agencies.
Frankly, I don't know whether our family was paying for such unauthorized services on one of our three AT&T phones, but it took only a few minutes for me to apply for a refund via the U.S. Federal Trade Commission site. T-Mobile has created a site for its customers to use to apply for a refund. As Schatz reports, Sprint and Verizon customers aren't able to seek a refund at present. Sprint has been sued over the issue by the Consumer Financial Protection Bureau, and the Federal Communications Commission may levy a multi-million-dollar fine against the company. Verizon hasn't settled yet, nor has the company been sued.
----------------------------------------------------------------------
One of the most dangerous of human activities is... walking?
I once read that human bipedalism is one of the marvels of nature. With every step, we come perilously close to falling flat on our faces. Walking while engaged in one (or both) of two other very common human activities can be extremely dangerous to your health.
AJ Vicens reports in a December 29, 2014, article in Mother Jones magazine that injuries incurred from texting while walking are skyrocketing. A study conducted in 2012 by researchers at Stony Brook University found that texting walkers were 61 percent more likely than their non-texting counterparts to wander off course. Emergency-room visits resulting from accidents to people distracted while walking and using their cell phone increased nearly 500 percent between 2005 and 2010, according to Ohio State University researchers.
Toss a couple of adult beverages into the mix and you've got a disaster just waiting to happen. Another December 29, 2014, Mother Jones article written by Maddie Oatman warns that on a per-mile basis, a drunk walker is eight times more likely to get killed than a drunk driver. That's according to Steven Levitt in his 2011 book, SuperFreakonomics.
Numbers collected by the National Highway Traffic Safety Administration in 2012 found that in almost half of the accidents that year in which a pedestrian was killed by a car, either the driver or the walker, or both, had blood alcohol levels above the legal limit. In these fatal accidents, 34 percent of the walkers were impaired, compared to 14 percent of the drivers.
It's no surprise that New Year's Day and Halloween are the two days you're most likely to be killed by a car while walking. What may raise an eyebrow is the day the researchers claim you're least likely to be the victim of such an accident: April 20th, or the infamous 4-20.
----------------------------------------------------------------------------
Cloud storage services such as Google Drive, Microsoft's OneDrive (formerly SkyDrive), Dropbox, and Apple's iCloud offer up to 10GB of free storage, which is sufficient to accommodate most people's needs. When you install the services' desktop app, you see its folder in Windows Explorer (called File Explorer in Windows 8), just like your Documents, Pictures, Desktop, and other folders.
Note that you'll need to encrypt and/or password-protect sensitive files before you save them to the cloud service. Tom's Guide provides step-by-step instructions for doing so in Windows and Microsoft Office. Alternatively, you could use a cloud storage service that encrypts automatically, such as Carbonite, which costs from $60 a year and has no storage limit, or SpiderOak, which offers up to 2GB of free encrypted cloud storage, and $10 a month or $100 a year for up to 100GB of encrypted storage.
SpiderOak's "zero-knowledge" privacy environment ensures that not even the company's employees can access your encrypted data. That's a pretty iron-clad guarantee, but if you prefer not to let your most sensitive files out of your possession, save encrypted versions of those files on a CD or DVD you keep under lock and key in your home or office.
(I've written about SpiderOak multiple times in the past, most recently on July 14, 2014, in "The pros and cons of cloud computing" and on October 21, 2014, in "Quick, simple fixes for everyday tech glitches.")
My backup strategy would probably be considered overkill by most people, but it is the result of having two laptops go kerflooey in relatively quick succession. In both failures, I lost only a handful of relatively unimportant files because my frequent-flyer job required that I be able to access my files from multiple machines in numerous locations.
Over the years I have created cloud-storage accounts on Google Drive, OneDrive, iCloud, Dropbox, and Box. Lately I've been using OneDrive to store my personal files and Dropbox for my work-related files. Nearly everything gets saved directly to at least one cloud service and then "backed up" to my local drive.
On the day the CryptoWall crooks try to extort a payment from me to decrypt my hard drive, I'll file a complaint with the Internet Crime Complaint Center, which is a joint effort by the U.S. Federal Bureau of Investigation and the National White Collar Crime Center. Then I'll reformat the machine's hard drive, reinstall Windows and my apps, and tell the bad guys to stick their bitcoins where the sun doesn't shine!
The FBI and other law-enforcement agencies recommend against paying such ransoms, although many people -- including NYT's Simone and her mother -- ignore this advice.
One last note on backups: Computer professionals advise that you create an image backup of your machine, which allows you to restore it quickly with apps and files in place. Over the years I've found that I spend too much time creating image backups I never need. Sure, it's good to know you've got a full backup at the ready in case of disaster, but the fix-on-failure approach has proven to be most efficient for me.
-----------------------------------------------------------------------
Were you 'crammed'? If so, your cell service provider may owe you money
Cramming is the practice perpetrated by some nefarious app vendors of sneaking their wares onto your phone or tablet and then charging a monthly fee that appears on your cell-phone bill. It's not at all uncommon for people to miss the charge and pay their bill without being aware that they've been hoodwinked.
In late 2013, AT&T, Verizon, Sprint, and T-Mobile agreed to stop allowing third parties to place such unauthorized charges on their customers' bills, as All Things D's Ina Fried reported in a November 21, 2013, article. Re/code's Amy Schatz explains in a December 31, 2014, post how to apply for a refund from two of the four carriers as part of a $160 million settlement with federal and state government agencies.
Frankly, I don't know whether our family was paying for such unauthorized services on one of our three AT&T phones, but it took only a few minutes for me to apply for a refund via the U.S. Federal Trade Commission site. T-Mobile has created a site for its customers to use to apply for a refund. As Schatz reports, Sprint and Verizon customers aren't able to seek a refund at present. Sprint has been sued over the issue by the Consumer Financial Protection Bureau, and the Federal Communications Commission may levy a multi-million-dollar fine against the company. Verizon hasn't settled yet, nor has the company been sued.
----------------------------------------------------------------------
One of the most dangerous of human activities is... walking?
I once read that human bipedalism is one of the marvels of nature. With every step, we come perilously close to falling flat on our faces. Walking while engaged in one (or both) of two other very common human activities can be extremely dangerous to your health.
AJ Vicens reports in a December 29, 2014, article in Mother Jones magazine that injuries incurred from texting while walking are skyrocketing. A study conducted in 2012 by researchers at Stony Brook University found that texting walkers were 61 percent more likely than their non-texting counterparts to wander off course. Emergency-room visits resulting from accidents to people distracted while walking and using their cell phone increased nearly 500 percent between 2005 and 2010, according to Ohio State University researchers.
Toss a couple of adult beverages into the mix and you've got a disaster just waiting to happen. Another December 29, 2014, Mother Jones article written by Maddie Oatman warns that on a per-mile basis, a drunk walker is eight times more likely to get killed than a drunk driver. That's according to Steven Levitt in his 2011 book, SuperFreakonomics.
Numbers collected by the National Highway Traffic Safety Administration in 2012 found that in almost half of the accidents that year in which a pedestrian was killed by a car, either the driver or the walker, or both, had blood alcohol levels above the legal limit. In these fatal accidents, 34 percent of the walkers were impaired, compared to 14 percent of the drivers.
It's no surprise that New Year's Day and Halloween are the two days you're most likely to be killed by a car while walking. What may raise an eyebrow is the day the researchers claim you're least likely to be the victim of such an accident: April 20th, or the infamous 4-20.
----------------------------------------------------------------------------
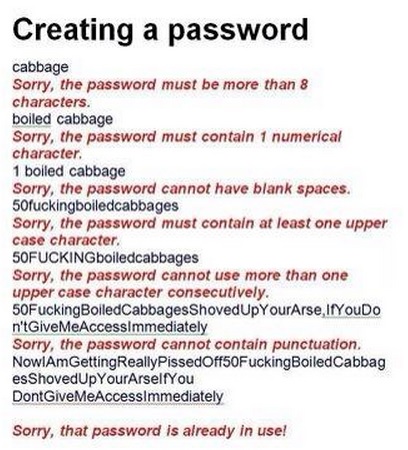
You have now entered password-creation hell
My antipathy for passwords is no secret, as evident by April 29, 2014's "I hate passwords," August 18, 2014's "Most data breaches are the result of weak or stolen credentials," and August 25, 2014's "Baby steps closer to authentication that doesn't rely on passwords."
Users' frustration with the rules organizations apply to the creation of passwords is summed up beautifully in this Twitter post by YouHadOneJob. (Caution: very adult language is expressed.)
In my experience, Apple's password policies are absolutely the most user-hostile. It often gets to the point where I simply request a password reset automatically when signing into an Apple service I haven't accessed in awhile rather than do battle with the company's convoluted, irrational password rules. I pray a reliable non-password authentication method arrives soon and ends our dependence on IT managers' sadistic password-creation rules.
My antipathy for passwords is no secret, as evident by April 29, 2014's "I hate passwords," August 18, 2014's "Most data breaches are the result of weak or stolen credentials," and August 25, 2014's "Baby steps closer to authentication that doesn't rely on passwords."
Users' frustration with the rules organizations apply to the creation of passwords is summed up beautifully in this Twitter post by YouHadOneJob. (Caution: very adult language is expressed.)
In my experience, Apple's password policies are absolutely the most user-hostile. It often gets to the point where I simply request a password reset automatically when signing into an Apple service I haven't accessed in awhile rather than do battle with the company's convoluted, irrational password rules. I pray a reliable non-password authentication method arrives soon and ends our dependence on IT managers' sadistic password-creation rules.
