Menu
How to secure your PC in 10 easy steps
Use encryption, keep your software up-to-date, disable images in e-mail, scan e-mail attachments for viruses, use a nonadministrator Windows account, scan for viruses manually, and use a secure-erase utility to destroy old data.
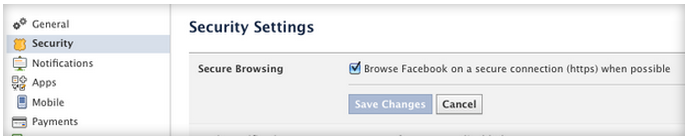
Choose Facebook's HTTPS option by clicking "Browse Facebook on a secure connection (https) when possible."
There's one thing you can do to avoid being the victim of identity theft: follow this 10-step PC security plan.
Encrypt your network connection
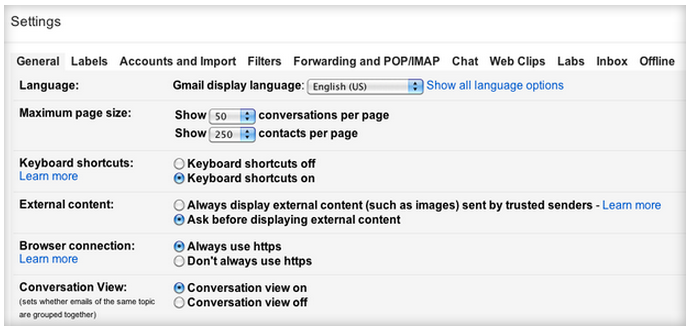
Most popular sites offer HTTPS connections at least some of the time. In Gmail, click the gear icon in the top-right corner and select "Always use https" under the General tab.
To select Facebook's HTTPS setting, click the down arrow in the top-right corner and choose Account settings. Select Security in the left pane and Edit in the Secure Browsing section of the main window. Check "Browse Facebook on a secure connection (https) when possible" and click Save Changes to activate the feature (the option is shown in the screen at the top of this post).
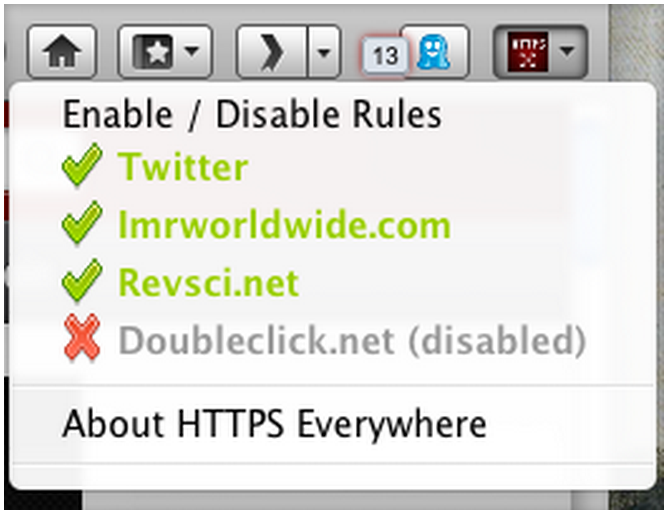
The Electronic Frontier Foundation's HTTPS Everywhere extension for Firefox doesn't encrypt every page you browse to, but it automatically requests an encrypted connection for those sites that support HTTPS and that have been added to the program's rules.
After you install HTTPS Everywhere, the extension's icon appears in the top-right corner of Firefox. Click it to view the encrypted and nonencrypted content served by the current page.
Encrypt your network connection
Most popular sites offer HTTPS connections at least some of the time. In Gmail, click the gear icon in the top-right corner and select "Always use https" under the General tab.
To select Facebook's HTTPS setting, click the down arrow in the top-right corner and choose Account settings. Select Security in the left pane and Edit in the Secure Browsing section of the main window. Check "Browse Facebook on a secure connection (https) when possible" and click Save Changes to activate the feature (the option is shown in the screen at the top of this post).
The Electronic Frontier Foundation's HTTPS Everywhere extension for Firefox doesn't encrypt every page you browse to, but it automatically requests an encrypted connection for those sites that support HTTPS and that have been added to the program's rules.
After you install HTTPS Everywhere, the extension's icon appears in the top-right corner of Firefox. Click it to view the encrypted and nonencrypted content served by the current page.
The Electronic Frontier Foundation's HTTPS Everywhere extension for Firefox shows the encrypted and nonencrypted content on the current page.
As the EFF's HTTPS Everywhere FAQ points out, HTTPS Everywhere doesn't work with every site and may conflict with some wireless networks, but the free add-on is a handy tool in your browser-security arsenal.
Encrypt sensitive files stored locally
The file-encryption features built into Windows and Mac OS leave much to be desired. Microsoft explains how to use Windows 7's encryption on its Help and How-to site.
The Apple Support site describes Mac OS X 10.6's FileVault encryption feature, and Macworld's Roman Loyola provides a primer on Mac OS Lion's FileVault 2.
These are far from your only encryption choices. In the past I have recommended the free TrueCrypt utility, but the program can be difficult to use. The Tech Support Alert site lists the best free encryption programs for Windows, many of which integrate with Windows Explorer.
Encrypt private information stored in the cloud
Is the data you store in the cloud safe? If you ask cloud-storage vendors, it is. But earlier this year The Economist took a critical look at the security of the popular Dropbox online-storage service. The article concludes that while the service may have overstated its security policies, it is safe enough for "casual" users.
In June 2009 I reviewed three free encrypted online storage services, and last April I compared Amazon's Cloud Drive and Box.net.
Use a free VPN service to protect public Wi-Fi connections
Even if you only occasionally sign in to Web accounts over a public Wi-Fi link, you can prevent lurking snoops by using a free VPN service to secure the connection. In a post from last February I wrote about the SecurityKISS VPN service that's easy to use and registration-free. The people commenting on that post recommended several other free VPN alternatives.
Prevent keystroke loggers, other data snoops
Computer criminals look for that path of least resistance, so they tend to attack the most vulnerable systems. To avoid being one of their victims, make sure your firewall and real-time antivirus software are working, and keep all your software up-to-date.
To ensure your Windows 7 PC's defenses are raised, run through the security checklist on the Microsoft Help and How-to site. The company's free Security Essentials program provides the real-time malware protection your system requires.
Last May I described three free services that automatically scan your system for outdated programs . My choice is Secunia's Personal Software Inspector, which provides an overall system score and a threat rating for each unpatched program on your PC.
Perform a manual virus scan with the free Malwarebytes Anti-Malware
Even with automatic software updates and regularly scheduled malware scans, viruses can sneak through your defenses. That's why it's a good idea to use Malwarebytes' free Anti-Malware program to scan your system manually. The utility was one of the security tools I covered in last September's post titled "How to prevent identity theft."
Disable images in e-mail
The people who send you e-mail may know when you open their messages and click links they contain. Programs such as Zendio, which I reviewed last month, pose a serious security threat, especially considering that the program also discloses your general location (via your IP address) when the message is opened.
To thwart e-mail snoops, disable images in your received messages. This prevents the HTML beacons used by the spies from being activated.
In October 2008 I described how to "View HTML mail from trusted senders, plain text from others." A month later I explained how to send and receive plain text mail in Outlook -- one of the tips in "Four essential tweaks keep Outlook safe and simple."
In Gmail, click the settings icon in the top-right corner, choose Mail settings, and select "Ask before displaying external content."
Encrypt sensitive files stored locally
The file-encryption features built into Windows and Mac OS leave much to be desired. Microsoft explains how to use Windows 7's encryption on its Help and How-to site.
The Apple Support site describes Mac OS X 10.6's FileVault encryption feature, and Macworld's Roman Loyola provides a primer on Mac OS Lion's FileVault 2.
These are far from your only encryption choices. In the past I have recommended the free TrueCrypt utility, but the program can be difficult to use. The Tech Support Alert site lists the best free encryption programs for Windows, many of which integrate with Windows Explorer.
Encrypt private information stored in the cloud
Is the data you store in the cloud safe? If you ask cloud-storage vendors, it is. But earlier this year The Economist took a critical look at the security of the popular Dropbox online-storage service. The article concludes that while the service may have overstated its security policies, it is safe enough for "casual" users.
In June 2009 I reviewed three free encrypted online storage services, and last April I compared Amazon's Cloud Drive and Box.net.
Use a free VPN service to protect public Wi-Fi connections
Even if you only occasionally sign in to Web accounts over a public Wi-Fi link, you can prevent lurking snoops by using a free VPN service to secure the connection. In a post from last February I wrote about the SecurityKISS VPN service that's easy to use and registration-free. The people commenting on that post recommended several other free VPN alternatives.
Prevent keystroke loggers, other data snoops
Computer criminals look for that path of least resistance, so they tend to attack the most vulnerable systems. To avoid being one of their victims, make sure your firewall and real-time antivirus software are working, and keep all your software up-to-date.
To ensure your Windows 7 PC's defenses are raised, run through the security checklist on the Microsoft Help and How-to site. The company's free Security Essentials program provides the real-time malware protection your system requires.
Last May I described three free services that automatically scan your system for outdated programs . My choice is Secunia's Personal Software Inspector, which provides an overall system score and a threat rating for each unpatched program on your PC.
Perform a manual virus scan with the free Malwarebytes Anti-Malware
Even with automatic software updates and regularly scheduled malware scans, viruses can sneak through your defenses. That's why it's a good idea to use Malwarebytes' free Anti-Malware program to scan your system manually. The utility was one of the security tools I covered in last September's post titled "How to prevent identity theft."
Disable images in e-mail
The people who send you e-mail may know when you open their messages and click links they contain. Programs such as Zendio, which I reviewed last month, pose a serious security threat, especially considering that the program also discloses your general location (via your IP address) when the message is opened.
To thwart e-mail snoops, disable images in your received messages. This prevents the HTML beacons used by the spies from being activated.
In October 2008 I described how to "View HTML mail from trusted senders, plain text from others." A month later I explained how to send and receive plain text mail in Outlook -- one of the tips in "Four essential tweaks keep Outlook safe and simple."
In Gmail, click the settings icon in the top-right corner, choose Mail settings, and select "Ask before displaying external content."
Block spying beacons embedded in the messages you receive by setting Gmail to ask before displaying external content.
Be wary of e-mail attachments
The recent increase in spear phishing has made it more difficult to trust that an e-mail was actually sent by the person whose name appears in the From: field. A post in April titled " E-mail security: Back on the front burner " described the safe way to open e-mail attachments: right-click downloaded files and choose the option to scan the file manually with whatever security program you use.
Use a standard (nonadministrator) account in Windows
Nine times out of ten you use your Windows PC without installing a new program, changing any settings, or performing some other action that requires an administrator account. Yet few people use a standard Windows account, which is one of the best ways to keep malware from infecting your system.
To create a standard account in Windows 7, press the Windows key, type user accounts, press Enter, click "Manage another account," and choose "Create new account." Give the account a name, select the "Standard user" option, and click Create Account. The account will appear on the Welcome screen the next time you start Windows.
The Microsoft Help and How-to site provides more information about the benefits of using a standard user account (in Vista and in Windows 7).
Destroy old data
The last time you donated an old computer or recycled a storage device, you probably didn't worry about someone stealing your identity by lifting sensitive data off the machine. It may not happen often, but it happens.
In a post from March 2009 I described " The right way to destroy an old hard drive ." As one commenter to that article pointed out, most people don't need to resort to drill presses, sledgehammers, or sandpaper on the drive platter.
A simpler and safer approach that's just as effective is to run a free secure-erase utility. The Tech Support Alert site describes several such products, including the program I mentioned in the 2009 article, Darik's Boot and Nuke (DBAN), which comes in a version that runs off floppy disks and USB flash drives and another that runs off a CD or a DVD.
The recent increase in spear phishing has made it more difficult to trust that an e-mail was actually sent by the person whose name appears in the From: field. A post in April titled " E-mail security: Back on the front burner " described the safe way to open e-mail attachments: right-click downloaded files and choose the option to scan the file manually with whatever security program you use.
Use a standard (nonadministrator) account in Windows
Nine times out of ten you use your Windows PC without installing a new program, changing any settings, or performing some other action that requires an administrator account. Yet few people use a standard Windows account, which is one of the best ways to keep malware from infecting your system.
To create a standard account in Windows 7, press the Windows key, type user accounts, press Enter, click "Manage another account," and choose "Create new account." Give the account a name, select the "Standard user" option, and click Create Account. The account will appear on the Welcome screen the next time you start Windows.
The Microsoft Help and How-to site provides more information about the benefits of using a standard user account (in Vista and in Windows 7).
Destroy old data
The last time you donated an old computer or recycled a storage device, you probably didn't worry about someone stealing your identity by lifting sensitive data off the machine. It may not happen often, but it happens.
In a post from March 2009 I described " The right way to destroy an old hard drive ." As one commenter to that article pointed out, most people don't need to resort to drill presses, sledgehammers, or sandpaper on the drive platter.
A simpler and safer approach that's just as effective is to run a free secure-erase utility. The Tech Support Alert site describes several such products, including the program I mentioned in the 2009 article, Darik's Boot and Nuke (DBAN), which comes in a version that runs off floppy disks and USB flash drives and another that runs off a CD or a DVD.