Menu
Five fantastic Web freebies
Plus: Internet privacy awareness is on the upswing, and a common-sense drug policy articulated by a state court.
There has never been a better time to be a cheapskate. The Internet is full of free programs and services, not to mention public-domain books, pictures, videos, and music available royalty-free. Here's a quick look at five of my favorite freebies.
(Fred Langa, one of the all-time great computer journalists, recently compiled a list of sites offering millions of free ebooks, movies, and music. In a July 14, 2014, post I wrote about free alternatives to the most popular software programs. A May 20, 2014, post described three free privacy add-ons for Firefox and Chrome, and a September 9, 2014, post looked at three other free browser security extensions.)
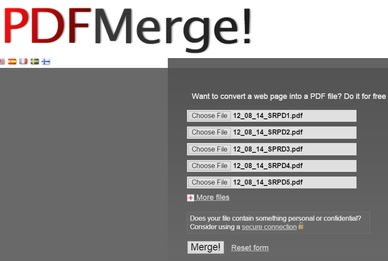
1. PDFMerge. I do a lot of work with PDF files. The free Foxit Reader program has most of the PDF features I need (see below for more on Foxit Reader), but one area the free version of that program falls short is merging PDF files. That's where PDFMerge shines.
This one-trick-pony of a site does what it does quickly, simply, and accurately. You browse to and select the PDF files you want to merge one by one. When they're all selected, click the Merge button. In seconds, a single PDF is downloaded that combines the files you selected.
The free version of the service limits files to 15 MB. (The site solicits donations from commercial users.) If the files you're merging contain sensitive or confidential information, use the service's secure connection.
2. Foxit Reader. As I mentioned above, this program meets most of my PDF needs without having to pay for Adobe Acrobat or another commercial PDF program. It has an Office-like interface and hooks to Office apps. You can create PDFs from scratch or by converting other types of files, including JPEG images and Word docs.
Foxit Reader lets you reformat and annotate your PDFs, add comments, and apply digital signatures and other security features. You can even embed files, images, audio, or video in the PDF.
3. Malwarebytes Anti-Malware. Of course you use an antivirus program. If you use Windows, make sure Security Essentials' real-time virus scanning is enabled. If you use a Macintosh, use a free Mac antivirus app such as one of the two I reviewed back in April 2012: Sophos Anti-Virus for Mac Home Edition or ClamXav. For your phone or tablet, use the free Lookout security software, which is one of the free security programs I described in April 10, 2014's "Protect your device from malicious ads."
No single antivirus program catches all the malware you're likely to encounter. If your computer or phone is acting up and you suspect it might be infected, run a manual malware scan with your real-time security app, and then run a second scan with Malwarebytes Anti-Malware, which is free for manual virus scans but not for real-time virus scanning.
After you download and install Malwarebytes, update its virus-definition database and then perform a full system scan. The process will likely take several hours, so you may want to let the scan run overnight. The chances are pretty good that one or both of the virus scanners will detect an infection, or at least some suspicious files, such as potentially unwanted programs, or PUPs. These are apps that aren't necessarily dangerous but that often tag along with other programs you download without you being aware of them.
On at least a half-dozen occasions in recent years I've done a dual scan on a persnickety PC that detected the problem and pointed the way to a fix.
4. Gizmo's Freeware (Tech Support Alert). Free software is only the start of the goodies tested and reviewed on this site, which is run by volunteers. This site is my first stop when I'm looking for a solution to a thorny computer problem.
Two of Gizmo's most popular resources are security related: the Security Wizard that steps you through every aspect of computer and Internet security; and the modestly named Probably the Best Security List in the World, Part I, which was most recently updated on August 24, 2014. In case you're wondering, there is indeed a Part II, as well as a Part III and a Part IV. (The site editors note that a complete revision of the Security List is underway.)
In addition to free software, Gizmo's volunteers tell you where to find free ebooks and audio books, free tech-support sites, and free download sites (Download.com is conspicuous in its absence.)
(Fred Langa, one of the all-time great computer journalists, recently compiled a list of sites offering millions of free ebooks, movies, and music. In a July 14, 2014, post I wrote about free alternatives to the most popular software programs. A May 20, 2014, post described three free privacy add-ons for Firefox and Chrome, and a September 9, 2014, post looked at three other free browser security extensions.)
1. PDFMerge. I do a lot of work with PDF files. The free Foxit Reader program has most of the PDF features I need (see below for more on Foxit Reader), but one area the free version of that program falls short is merging PDF files. That's where PDFMerge shines.
This one-trick-pony of a site does what it does quickly, simply, and accurately. You browse to and select the PDF files you want to merge one by one. When they're all selected, click the Merge button. In seconds, a single PDF is downloaded that combines the files you selected.
The free version of the service limits files to 15 MB. (The site solicits donations from commercial users.) If the files you're merging contain sensitive or confidential information, use the service's secure connection.
2. Foxit Reader. As I mentioned above, this program meets most of my PDF needs without having to pay for Adobe Acrobat or another commercial PDF program. It has an Office-like interface and hooks to Office apps. You can create PDFs from scratch or by converting other types of files, including JPEG images and Word docs.
Foxit Reader lets you reformat and annotate your PDFs, add comments, and apply digital signatures and other security features. You can even embed files, images, audio, or video in the PDF.
3. Malwarebytes Anti-Malware. Of course you use an antivirus program. If you use Windows, make sure Security Essentials' real-time virus scanning is enabled. If you use a Macintosh, use a free Mac antivirus app such as one of the two I reviewed back in April 2012: Sophos Anti-Virus for Mac Home Edition or ClamXav. For your phone or tablet, use the free Lookout security software, which is one of the free security programs I described in April 10, 2014's "Protect your device from malicious ads."
No single antivirus program catches all the malware you're likely to encounter. If your computer or phone is acting up and you suspect it might be infected, run a manual malware scan with your real-time security app, and then run a second scan with Malwarebytes Anti-Malware, which is free for manual virus scans but not for real-time virus scanning.
After you download and install Malwarebytes, update its virus-definition database and then perform a full system scan. The process will likely take several hours, so you may want to let the scan run overnight. The chances are pretty good that one or both of the virus scanners will detect an infection, or at least some suspicious files, such as potentially unwanted programs, or PUPs. These are apps that aren't necessarily dangerous but that often tag along with other programs you download without you being aware of them.
On at least a half-dozen occasions in recent years I've done a dual scan on a persnickety PC that detected the problem and pointed the way to a fix.
4. Gizmo's Freeware (Tech Support Alert). Free software is only the start of the goodies tested and reviewed on this site, which is run by volunteers. This site is my first stop when I'm looking for a solution to a thorny computer problem.
Two of Gizmo's most popular resources are security related: the Security Wizard that steps you through every aspect of computer and Internet security; and the modestly named Probably the Best Security List in the World, Part I, which was most recently updated on August 24, 2014. In case you're wondering, there is indeed a Part II, as well as a Part III and a Part IV. (The site editors note that a complete revision of the Security List is underway.)
In addition to free software, Gizmo's volunteers tell you where to find free ebooks and audio books, free tech-support sites, and free download sites (Download.com is conspicuous in its absence.)
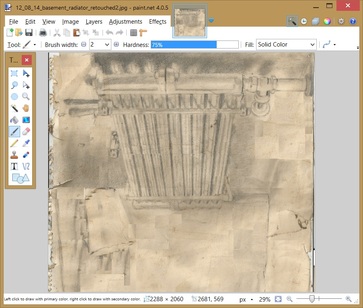
5. Paint.net. I'm a big fan of Windows' Paint utility, which doesn't do much, but does it well, if that makes any sense. Paint.net was created as a substitute for Paint with a boatload full of added formatting and editing features. The program's developers compare Paint.net to Adobe Photoshop, Corel Paint Shop Pro, and the free, open-source GIMP image editor.
I used Paint.net to attempt a quick retouch of a water-damaged pencil drawing a friend had given me years before. The program supports layers and adjustments just as the popular commercial image-editing programs do. It has an eye-dropper color picker and offers a couple dozen automated effects, such as blurs, glow, fractals, and noise adjustments.
If somebody as unartistically inclined as I am can manage to improve an image even a little bit, the program has proven its worth. While Paint.net may lack the advanced features of Photoshop and Paint Shop Pro, for simple, straight-forward image edits, the program is a true bargain.
----------------------------------------------------------
New tools tell you what the trackers and snoops know about you
Want to get creeped out? Use one of the many programs that tell you what personal information social media and other Web sites have collected about you: Creepy, PleaseRobMe.com, and Girls Around Me, which is a service that locates pictures of women who are near you and superimposes the pictures onto a map.
There are also apps that scan social-media posts in an attempt to identify people who are suicidal; others track your movements through a store; and one called Turnstyle even follows you around the city of Toronto.
The Guardian's Ben Goldacre explains in a December 5, 2014, article that nearly all security is now digital, but we don't understand how it works. Instead, we are dealing with "a series of black boxes into which we entrust our money, our privacy and everything else we might hope to have under lock and key. We have no clear sight into this world, and we have few sound intuitions into what is safe and what is flimsy – let alone what is ethical and what is creepy. We are left operating on blind, ignorant, misplaced trust; meanwhile, all around us, without our even noticing, choices are being made."
Two areas in particular where reams of sensitive data are being collected are health and finance. Imagine your refrigerator reporting to your insurance company on your excessive ice cream intake. Or merchants basing the price you pay for their goods and services on what they know about how badly you need the product, or how willing you would be to overpay (whether you know you're overpaying or not.)
Now imagine the market intelligence in the hands of consumers, who can determine more precisely the market value of an item right here, right now, and can time their purchases accordingly. Which way do you think the information-distribution pendulum will swing?
-----------------------------------------------------------------
There's a reason why Internet services don't talk about privacy
People on the Internet are increasingly concerned about losing their privacy. That's according to the results of a recent Pew Research Internet Project survey. The Pew numbers, which were released on November 12, 2014, indicate that 91 percent of U.S. adults agree or strongly agree that consumers have lost control of the collection and use of their personal information by companies.
The results of another Pew survey, released on December 4, 2014, show that more than half of us erroneously believe that a Web site's privacy policy ensures the company keeps confidential all information it collects about its customers. In fact, they should be called anti-privacy policies because they grant the company the right to use whatever information it collects about you in nearly any way it chooses.
In any event, few people bother reading privacy policies, which isn't a surprise, considering that Joseph Turow of the University of Pennsylvania Annenberg School Communications calls the policies "unreadable."
Forbes' Jonathan Salem Baskin writes in a December 7, 2014, article that people may not know much about what's happening with their personal information now, but it won't take long for them to realize there's an "asymmetrical exchange of information" going on, and consumers are getting the short end of the stick. Baskin hints that some of the more forward-thinking of the multibillion-dollar behemoths might want to get ahead of this trend before the inevitable consumer backlash swamps them.
---------------------------------------------------------------------------
Common-sense drug policy from courts in the Land of the Midnight Sun
In 1975, the Alaska Supreme Court ruled that the state's Constitutional right to privacy prevented law enforcement from preventing people from smoking marijuana in their own homes. The state would need a "compelling interest" to violate the person's privacy, not the lower threshold of an interest that is merely "rationally related[] to the accomplishment of a permissible state policy."
The state argued that the health and safety of its citizens outweighed the privacy rights of individuals who wanted to smoke marijuana in their homes. The court disagreed, ruling that marijuana use "does not constitute a public health problem of any significant dimensions. It is, for instance, far more innocuous in terms of physiological and social damage than alcohol or tobacco.”
In 1978, the Alaska Supreme Court revisited the issue, this time as it related to cocaine use. In this instance, the court ruled that cocaine is far more dangerous than marijuana, in part because you can die of an overdose. Therefore, the state's argument that it must protect the health and safety of citizens justifies the violation of the constitutional right to privacy. The police can arrest you for using cocaine in your home.
Fast-forward to 1984, when the issue came up again in relation to alcohol use. Some local communities had taken advantage of a 1981 Alaska statute that allowed them to ban alcohol, although people could still drink alcoholic beverages in their homes. A man was convicted of importing alcohol to one such community in violation of the ordinance. The man argued that the conviction violated his constitutional right to privacy. The court ruled that alcohol was more like cocaine than marijuana in terms of its threat to the community's health and safety.
Last month, Alaskans approved the sale and use of marijuana in the state. Some communities want to include marijuana in their local prohibition of alcohol. Even if the legislature (or the state courts) allow marijuana to be prohibited in local communities that decide to do so, it appears people in those areas would retain a constitutional right to use the drug in their own homes.
As AlterNet's David Morris states in a December 4, 2014, article, the Alaska courts are to be commended for using "scientific evidence to determine the balance between the right of the state to protect its citizens with the right of its citizens to be left alone. The U.S. Congress and Supreme Court have much to learn from the next to last state to join the Union."
I used Paint.net to attempt a quick retouch of a water-damaged pencil drawing a friend had given me years before. The program supports layers and adjustments just as the popular commercial image-editing programs do. It has an eye-dropper color picker and offers a couple dozen automated effects, such as blurs, glow, fractals, and noise adjustments.
If somebody as unartistically inclined as I am can manage to improve an image even a little bit, the program has proven its worth. While Paint.net may lack the advanced features of Photoshop and Paint Shop Pro, for simple, straight-forward image edits, the program is a true bargain.
----------------------------------------------------------
New tools tell you what the trackers and snoops know about you
Want to get creeped out? Use one of the many programs that tell you what personal information social media and other Web sites have collected about you: Creepy, PleaseRobMe.com, and Girls Around Me, which is a service that locates pictures of women who are near you and superimposes the pictures onto a map.
There are also apps that scan social-media posts in an attempt to identify people who are suicidal; others track your movements through a store; and one called Turnstyle even follows you around the city of Toronto.
The Guardian's Ben Goldacre explains in a December 5, 2014, article that nearly all security is now digital, but we don't understand how it works. Instead, we are dealing with "a series of black boxes into which we entrust our money, our privacy and everything else we might hope to have under lock and key. We have no clear sight into this world, and we have few sound intuitions into what is safe and what is flimsy – let alone what is ethical and what is creepy. We are left operating on blind, ignorant, misplaced trust; meanwhile, all around us, without our even noticing, choices are being made."
Two areas in particular where reams of sensitive data are being collected are health and finance. Imagine your refrigerator reporting to your insurance company on your excessive ice cream intake. Or merchants basing the price you pay for their goods and services on what they know about how badly you need the product, or how willing you would be to overpay (whether you know you're overpaying or not.)
Now imagine the market intelligence in the hands of consumers, who can determine more precisely the market value of an item right here, right now, and can time their purchases accordingly. Which way do you think the information-distribution pendulum will swing?
-----------------------------------------------------------------
There's a reason why Internet services don't talk about privacy
People on the Internet are increasingly concerned about losing their privacy. That's according to the results of a recent Pew Research Internet Project survey. The Pew numbers, which were released on November 12, 2014, indicate that 91 percent of U.S. adults agree or strongly agree that consumers have lost control of the collection and use of their personal information by companies.
The results of another Pew survey, released on December 4, 2014, show that more than half of us erroneously believe that a Web site's privacy policy ensures the company keeps confidential all information it collects about its customers. In fact, they should be called anti-privacy policies because they grant the company the right to use whatever information it collects about you in nearly any way it chooses.
In any event, few people bother reading privacy policies, which isn't a surprise, considering that Joseph Turow of the University of Pennsylvania Annenberg School Communications calls the policies "unreadable."
Forbes' Jonathan Salem Baskin writes in a December 7, 2014, article that people may not know much about what's happening with their personal information now, but it won't take long for them to realize there's an "asymmetrical exchange of information" going on, and consumers are getting the short end of the stick. Baskin hints that some of the more forward-thinking of the multibillion-dollar behemoths might want to get ahead of this trend before the inevitable consumer backlash swamps them.
---------------------------------------------------------------------------
Common-sense drug policy from courts in the Land of the Midnight Sun
In 1975, the Alaska Supreme Court ruled that the state's Constitutional right to privacy prevented law enforcement from preventing people from smoking marijuana in their own homes. The state would need a "compelling interest" to violate the person's privacy, not the lower threshold of an interest that is merely "rationally related[] to the accomplishment of a permissible state policy."
The state argued that the health and safety of its citizens outweighed the privacy rights of individuals who wanted to smoke marijuana in their homes. The court disagreed, ruling that marijuana use "does not constitute a public health problem of any significant dimensions. It is, for instance, far more innocuous in terms of physiological and social damage than alcohol or tobacco.”
In 1978, the Alaska Supreme Court revisited the issue, this time as it related to cocaine use. In this instance, the court ruled that cocaine is far more dangerous than marijuana, in part because you can die of an overdose. Therefore, the state's argument that it must protect the health and safety of citizens justifies the violation of the constitutional right to privacy. The police can arrest you for using cocaine in your home.
Fast-forward to 1984, when the issue came up again in relation to alcohol use. Some local communities had taken advantage of a 1981 Alaska statute that allowed them to ban alcohol, although people could still drink alcoholic beverages in their homes. A man was convicted of importing alcohol to one such community in violation of the ordinance. The man argued that the conviction violated his constitutional right to privacy. The court ruled that alcohol was more like cocaine than marijuana in terms of its threat to the community's health and safety.
Last month, Alaskans approved the sale and use of marijuana in the state. Some communities want to include marijuana in their local prohibition of alcohol. Even if the legislature (or the state courts) allow marijuana to be prohibited in local communities that decide to do so, it appears people in those areas would retain a constitutional right to use the drug in their own homes.
As AlterNet's David Morris states in a December 4, 2014, article, the Alaska courts are to be commended for using "scientific evidence to determine the balance between the right of the state to protect its citizens with the right of its citizens to be left alone. The U.S. Congress and Supreme Court have much to learn from the next to last state to join the Union."
