Menu
Instant access to all your recent files
The chances are pretty good you store your important files in four, five, or even more different Windows folders. Even if you can usually remember where to find a particular file, now and then it becomes a guessing game. Documents? Downloads? Desktop? Dropbox? Google Drive?
The quickest way to find a file that has gone AWOL is to press the Windows key and R to open the Run dialog box, type "recent" (without the quotes), and press Enter. This opens an Explorer window that lists all the files you've touched, starting with the most recent.
The Recent Places folder in Windows 8 shows only your recent folders and searches, as Eric Ravenscraft points out in an October 2, 2014, article on LifeHacker. (A commenter to that article points out that you can add a folder shortcut to your Favorites list by navigating to the folder, right-clicking Favorites in the Navigation pane, and selecting "Add current location to Favorites.")
Equal time for Macs: Click the Apple icon in the top-left corner and choose Recent Items. Too easy.
The quickest way to find a file that has gone AWOL is to press the Windows key and R to open the Run dialog box, type "recent" (without the quotes), and press Enter. This opens an Explorer window that lists all the files you've touched, starting with the most recent.
The Recent Places folder in Windows 8 shows only your recent folders and searches, as Eric Ravenscraft points out in an October 2, 2014, article on LifeHacker. (A commenter to that article points out that you can add a folder shortcut to your Favorites list by navigating to the folder, right-clicking Favorites in the Navigation pane, and selecting "Add current location to Favorites.")
Equal time for Macs: Click the Apple icon in the top-left corner and choose Recent Items. Too easy.

Four sisters, 40 years, 40 portraits
The four Brown sisters are the definition of growing old(er) gracefully. Their portraits captured once a year since 1975 make aging together look not so bad after all. (Don't rush through the black-and-white images.)
Bonus link: If you like perusing vintage photos, check out Vintage Everyday, another donation site whose images of San Francisco in the late 19th century caught my eye.
Free app encrypts your phone, protects your privacy
Government officials are still criticizing Apple's decision to allow iPhone and iPad users to encrypt their devices without Apple or anyone else but them being able to decrypt it. (Google quickly followed Apple's move by announcing it would allow the same level of encryption on Android devices; I wrote about this in a September 22, 2014, article.)
As the Register's Iain Thomson explains in an October 4, 2014, article, the only real change is that law enforcement must now get a warrant before ordering that the phone be decrypted. Finding evidence of a crime on an encrypted device is more difficult and potentially more time-consuming, but doing so is not impossible.
For added protection, a German company called ZenGuard offers the free ZenMate VPN browser extension that encrypts your phone's connection and keeps your location a secret. The extension works with iPhones/iPads, Android phones and tablets, and the Chrome and Firefox browsers.
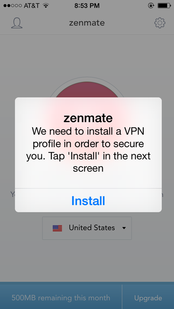
When I tested the free version of the app on an iPhone 5, it installed without a hitch. You get a 30-day trial of the fee-based version's data encryption and automatic blocking of "harmful" sites. Sign up by providing an email address and password. You'll be promoted to install a VPN profile by pressing the Install button (as shown in the screen above).
Government officials are still criticizing Apple's decision to allow iPhone and iPad users to encrypt their devices without Apple or anyone else but them being able to decrypt it. (Google quickly followed Apple's move by announcing it would allow the same level of encryption on Android devices; I wrote about this in a September 22, 2014, article.)
As the Register's Iain Thomson explains in an October 4, 2014, article, the only real change is that law enforcement must now get a warrant before ordering that the phone be decrypted. Finding evidence of a crime on an encrypted device is more difficult and potentially more time-consuming, but doing so is not impossible.
For added protection, a German company called ZenGuard offers the free ZenMate VPN browser extension that encrypts your phone's connection and keeps your location a secret. The extension works with iPhones/iPads, Android phones and tablets, and the Chrome and Firefox browsers.
When I tested the free version of the app on an iPhone 5, it installed without a hitch. You get a 30-day trial of the fee-based version's data encryption and automatic blocking of "harmful" sites. Sign up by providing an email address and password. You'll be promoted to install a VPN profile by pressing the Install button (as shown in the screen above).
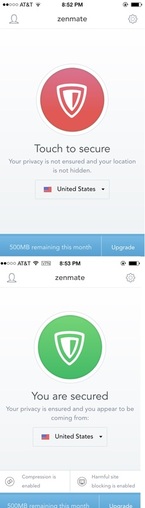
To encrypt your connection, open the app and press the big red "Touch to secure" button. The button will turn green and state that "You are secured." The screen also shows the amount of your 500MB monthly data allotment you have remaining, and the country "you appear to be coming from." You can change this via a drop-down menu.
I didn't notice any slow-down in data transfers when ZenMate's VPN was enabled, but I tested the app only over a WiFi connection, not on my carrier's 4G network.
You can also set up a VPN connection on your iPhone without needing a separate app, as the Apple Support site explains. You'll have to contact your network administrator to get the required configuration information, however.
ZenMate's premium account costs $3 a month or $30 a year, which gets you unlimited data use in addition to data encryption and harmful-site blocking.
Before you buy that used iPhone...
Check to make sure a pre-owned iPhone you're thinking of buying isn't also pre-stolen by visiting Apple's Check Activation Lock Status page. There you can enter the Device IMEI or serial number (plus a captcha) to determine whether the phone has been reported lost or stolen.
TechCrunch's Greg Kumparak explains in an October 2, 2014, article that thieves have figured out how to bypass the iPhone's activation lock screen far enough to make the phone look legitimate. That's why potential buyers of used iPhones need to go to the source to confirm the device's ownership status via Apple's database.
I didn't notice any slow-down in data transfers when ZenMate's VPN was enabled, but I tested the app only over a WiFi connection, not on my carrier's 4G network.
You can also set up a VPN connection on your iPhone without needing a separate app, as the Apple Support site explains. You'll have to contact your network administrator to get the required configuration information, however.
ZenMate's premium account costs $3 a month or $30 a year, which gets you unlimited data use in addition to data encryption and harmful-site blocking.
Before you buy that used iPhone...
Check to make sure a pre-owned iPhone you're thinking of buying isn't also pre-stolen by visiting Apple's Check Activation Lock Status page. There you can enter the Device IMEI or serial number (plus a captcha) to determine whether the phone has been reported lost or stolen.
TechCrunch's Greg Kumparak explains in an October 2, 2014, article that thieves have figured out how to bypass the iPhone's activation lock screen far enough to make the phone look legitimate. That's why potential buyers of used iPhones need to go to the source to confirm the device's ownership status via Apple's database.
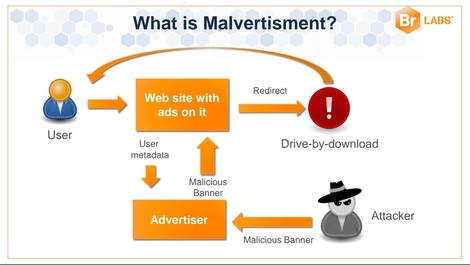
Malicious ads strike again!
Online ads are becoming the preferred medium for malware. In a September 26, 2014, article on Forbes, Thomas Fox-Brewster explains how Google's DoubleClick network was serving up ads laced with the Zemot Trojan that is used to install even more malware on infected machines. Security firm Malwarebytes discovered the ad-network breach and traced it to ad-provider Zedo. UK security company Bromium identified malware-ad attacks in August 2014 against Yahoo, Dictionary.com, and Answers.com, according to Fox-Brewster.
The malware authors fool the ad networks into thinking they are legitimate businesses. The malware they ultimately deliver takes advantage of vulnerabilities in old versions of Adobe Flash and Internet Explorer; it also affects the Firefox and Opera browsers, according to Malwarebytes. One researcher was able to use the malware's technique to take over an Android phone, accessing its camera, email, data, and other resources.
The best prevention is to keep all software up-to-date, especially Flash and browsers. For more on the dangers of online advertising, see my June 10, 2014, article.
Will we finally own our own data?
MIT Media Lab researchers are creating a personal data store designed to protect your sensitive information while also allowing you to share it easily when you choose to. openPDS works by collecting and storing your personal data locally, according to MIT graduate student Yves-Alexandre de Montjoye, who is working on the project with MIT Media Lab Director Alex Pentland. When an app requests your information, openPDS's SafeAnswers system shares only the data the app requires to function, according to de Montjoye.
Jessica Leber describes the project on the Fast Company Co.Exist site.
The example de Montjoye gives is an app that needs to know whether you are home. Rather than providing the app with your complete GPS log (including the location of your home), SafeAnswers will reply with a simple "yes" or "no." openPDS also makes it possible for users to monetize the sharing of their personal information. Instead of Google or Facebook selling your private details to advertisers, you could offer it to the companies yourself and negotiate your own terms.
I can see the exchange now: "You really want to know what I had for dinner? What's it worth to you?"
Online ads are becoming the preferred medium for malware. In a September 26, 2014, article on Forbes, Thomas Fox-Brewster explains how Google's DoubleClick network was serving up ads laced with the Zemot Trojan that is used to install even more malware on infected machines. Security firm Malwarebytes discovered the ad-network breach and traced it to ad-provider Zedo. UK security company Bromium identified malware-ad attacks in August 2014 against Yahoo, Dictionary.com, and Answers.com, according to Fox-Brewster.
The malware authors fool the ad networks into thinking they are legitimate businesses. The malware they ultimately deliver takes advantage of vulnerabilities in old versions of Adobe Flash and Internet Explorer; it also affects the Firefox and Opera browsers, according to Malwarebytes. One researcher was able to use the malware's technique to take over an Android phone, accessing its camera, email, data, and other resources.
The best prevention is to keep all software up-to-date, especially Flash and browsers. For more on the dangers of online advertising, see my June 10, 2014, article.
Will we finally own our own data?
MIT Media Lab researchers are creating a personal data store designed to protect your sensitive information while also allowing you to share it easily when you choose to. openPDS works by collecting and storing your personal data locally, according to MIT graduate student Yves-Alexandre de Montjoye, who is working on the project with MIT Media Lab Director Alex Pentland. When an app requests your information, openPDS's SafeAnswers system shares only the data the app requires to function, according to de Montjoye.
Jessica Leber describes the project on the Fast Company Co.Exist site.
The example de Montjoye gives is an app that needs to know whether you are home. Rather than providing the app with your complete GPS log (including the location of your home), SafeAnswers will reply with a simple "yes" or "no." openPDS also makes it possible for users to monetize the sharing of their personal information. Instead of Google or Facebook selling your private details to advertisers, you could offer it to the companies yourself and negotiate your own terms.
I can see the exchange now: "You really want to know what I had for dinner? What's it worth to you?"
