Menu
Should all web traffic be encrypted? |
Suppose the government owned a master key that could open any locked door. How would that go over with civil libertarians?
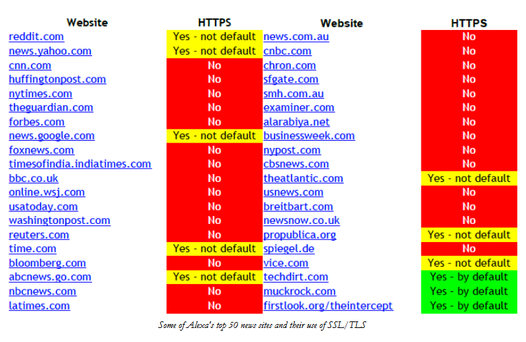
Now the government is asking that all data-encryption technologies include a "back door" that would allow law enforcement agencies to decrypt the data. In fact, the U.S. National Security Agency is requesting a "front door" with "multiple... big locks," according to NSA director Michael S. Rogers. Rogers made the comment during a recent speech at Princeton University; the Washington Post's Ellen Nakashima and Bruce Gellman report on Rogers' address in an April 10, 2015, article. Even if you trust the government not to abuse this spying capability, creating a chink in the encryption armor is an open invitation to criminals to help themselves to the data by figuring out how to access the back door (or front door) themselves. Yet the question of whether it should be illegal to create an unbreakable data lock has government security officials and private-sector security experts poles apart. From the government's perspective, it may already be too late to bell the encryption cat. Strong encryption is readily available -- to good guys and bad guys alike. We learn yet again that technology is neutral: whether it's used for our benefit or to our detriment is up to us. Outlawing the technology is not the solution, and will likely only make matters worse. Then there's that minor Constitutional matter of a right to free speech. Can you say "prior restraint"? HTTPS's Achilles heel: Bogus certificates are rampant The technology to encrypt data as it travels between web servers and our browsers has existed since the earliest days of the web. HTTPS applies the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocol to standard HTTP traffic. It depends on a Certificate Authority to issue certificates intended to verify that the site you're visiting is indeed what it purports to be. Unfortunately, HTTPS is "hopelessly broken," as The Register's Dan Goodin explained in an April 11, 2011, article. It's too easy for criminals to get their hands on "legitimate" certificates. Goodin quotes several security experts who blame a lack of accountability among certificate authorities, which have issued thousands of credentials to "unqualified" domain names, such as "localhost" and "exchange." Last week's Weekly described how the Superfish ad-injecting malware placed an unsafe certificate on victims' computers. The bad certificate was used to steal the users' data by launching man-in-the-middle attacks. In an April 13, 2015, article, Computerworld's Michael Horowitz explains two simple techniques that would go a long way toward preventing such attacks, neither of which is ever likely to be implemented widely. The first is for the browser to display the name of the certificate authority issuing each site's credential. If the same authority appears for all sites, you can bet the system has been compromised. The second technique, which was suggested by Jonathan Zdziarski, is more automatic: Whenever the same certificate authority appears repeatedly, the browser would generate a warning. (Note that many legitimate security programs replace the certificate authorities with their own when they scan web connections for malware.) Horowitz believes the reason no such defense will be added to browsers is that the tech industry prefers to keep their customers uninformed. He examines several possible solutions to the insecure-certificate problem, such as Google's Certificate Transparency project and Zdziarski's Certificate Validation Framework. But there's another big reason why HTTPS is underused: It's difficult to implement, and that means higher costs for Internet services. Get ready for end-to-end web encryption The Electronic Frontier Foundation is addressing the low HTTPS adoption rate via its Let's Encrypt program scheduled to debut in "mid-2015," according to the organization. Let's Encrypt creates a "free, automated, and open" certificate authority being developed by the Internet Security Research Group in collaboration with The Linux Foundation and several big-name vendors. (In the interim, be sure to download and install the EFF's free HTTPS Everywhere browser extension, which I wrote about most recently in the March 17, 2015, Weekly. The program automatically switches from insecure HTTP sites to their more-secure HTTPS counterparts whenever such sites are available.) In a November 20, 2014, article, The Intercept's Micah Lee blames the low HTTPS adoption rate on the difficulty of implementing the technology on web servers, which causes some web hosting firms to charge more to host HTTPS sites. The EFF's survey of popular sites indicates that only a handful use HTTPS by default. |
More importantly, HTTPS sites can't host non-HTTPS content, which means ad networks that don't support encryption can't place their ads on HTTPS sites. Let's Encrypt is intended to make applying HTTPS as simple as running a single command.
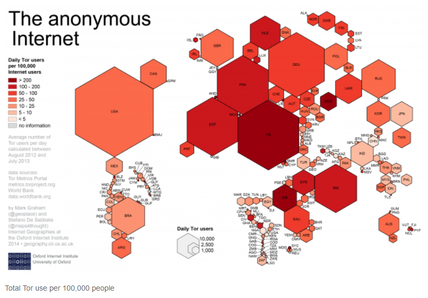
A program such as Let's Encrypt isn't the silver bullet that will solve all web security problems. Certificates could still be compromised, for example, but doing so would require more effort -- at least in theory. The government would still be able to decrypt specific data, but only after targeting the sites they're after rather than gobbling up web data indiscriminately. Another benefit of end-to-end web encryption is that it makes it more difficult for countries such as China, Iran, and North Korea to block web content. Forbes' Thomas Fox-Brewster writes in an April 10, 2015, article that China's new Great Cannon "censorship machine" was used to launch a distributed denial-of-service (DDOS) attack on the code-sharing site Github. The attack was designed to redirect traffic intended for the country's Baidu search engine (its equivalent of Google). Great Cannon has many other potentially nefarious uses, according to the Canadian-based Citizen Lab, such as intercepting unencrypted email and substituting malware payloads for legitimate file attachments. As Fox-Brewster points out, encryption transforms the Great Cannon into the Great Pumpkin -- but only if Let's Encrypt and other certificate authorities are able to keep their certificates out of the hands of the Chinese government. That's a pretty big "if." The do-it-yourself encryption alternative: Virtual private networks It would be nice if all web sites encrypted all the data that traveled between their servers and our browsers, but that's not likely to happen soon even with the arrival of simpler HTTPS implementations such as Let's Encrypt. If you prefer to take data security into your own hands, you can use a virtual private network, which creates an encrypted "tunnel" through which your web data travels. In a February 14, 2011, article, I described the OpenVPN-based SecurityKISS service, which is available in a limited free version and in various paid versions. Two alternatives are Private Internet Access and the granddaddy of free anonymous services, the Tor Project. In fact, Tor and other VPN services are so popular in Russia that the country is reportedly considering outlawing the programs, as ExtremeTech's Joel Hruska reports in a February 13, 2015, article. It's a fact that Tor and other VPN products are used by web criminals, but Hruska claims the vast majority of VPN users are law-abiding citizens who merely want to maintain their privacy, often as protection from authoritarian regimes. This is indicated by the stylized map of daily Tor users that appears at the top of this post. Blaming encryption for Internet crime is like blaming cars for drunk driving. Besides, if Vladimir Putin is against people's use of encryption, how bad can it be? Generally speaking, what Putin is for, I'm against, and what Putin's against, I'm for. If only everything in life were so simple. |
