Menu
Free VPN service helps keep public Wi-Fi safe
The SecureKiss virtual private network service is relatively simple to install and use. The free version lets you transmit up to 300MB per day without having to register.
The last time you used a public Wi-Fi hot spot, did you get the feeling you were being watched? Good. You very well may have been.
Just last week the U.S. Federal Trade Commission published the Wise Up About Wi-Fi page that offers tips for safe use of public Wi-Fi. Among the tips is the familiar advice to use encryption at all times (look for "https:" in the address header and the lock icon in the address bar or it the bottom status bar, depending on your browser).
The FTC's public-Wi-Fi safety page recommends that you heed your browser's warnings about unsafe sites; in November 2009 I compared the security features of five browsers: Internet Explorer, Firefox, Google Chrome, Safari, and Opera. While they differ in their approach, all five programs do a good job of preventing malicious sites from opening and malware from being downloaded and installed.
But there's not much a browser can do to protect against Wi-Fi snoops, particularly when using an unencrypted connection or visiting unencrypted sites. Browser add-ons such as the Electronic Frontier Foundation's free HTTPS Everywhere for Firefox will encrypt some--but not all--data traveling between your PC and the site you're visiting. (I described that program and other Firefox security add-ons in a post from last November.)
Another recommendation on the Wise Up About Wi-Fi page is to use a virtual private network to create a secure tunnel that protects all the data sent over the connection. The organization you work for may help you install and set up a VPN link to its internal network that you may also be able to use to secure a public Wi-Fi connection.
The do-it-yourself approach to VPN can be a difficult--especially if you try to configure Windows' built-in VPN service. After spending the better part of an afternoon attempting and failing to set up the Windows VPN, I threw up my hands and started looking for a simpler alternative. I found it in the free, OpenVPN-based SecurityKiss service.
Keeping VPN simple -- and registration-free
Last November's post on Firefox security add-ons included a link to the LogMeIn Hamachi VPN product (free for non-commercial use), as well as links to two free encryption programs: the open-source TrueCrypt and the non-open-source UltraVPN.
No other VPN service I've tested can match SecurityKiss for ease of use. You have to select "Open as administrator" when you install the program, but other than that added step, getting SecurityKiss set up is as straightforward as security gets.
When the installation completes, you'll find a SecurityKiss shortcut on the Start menu and the service's icon in the taskbar notification area. After you open the program, click the Connect button at the bottom of its window. After a few seconds, you'll see a message indicating that "you are now in the encrypted tunnel" and listing your local and external IP addresses.
The SecurityKiss window includes a graph of the amount of data you've transmitted and the time spent in encrypted mode. The free version's daily limit is 300MB, which is sufficient for the casual public Wi-Fi user. Paid packages cost from 4 euros (about $5.39) a month or 40 euros a year for up to 20GB of data per month, to 10 euros (about $13.48) a month or 100 euros a year for up to 80GB a month (the details are available on the company's Packages page).
The service's options let you switch servers and enable the VPN connection automatically on start-up. SecurityKiss claims to offer many other advantages for users, such as allowing access to sites that your employer or Internet provider may block, the ability to open ports that have been blocked on your PC, and "complete anonymity."
One of the nicest features of the free service is that it's available without having to register, which makes it a bit easier to believe the company's claim of complete anonymity. Still, I find it difficult to trust any such claim, in large part because anonymity would be difficult for anyone to prove. In my opinion, "complete anonymity" on the Internet is impossible.
That doesn't mean you can't make it tougher for snoops to find out about you, especially considering most online thieves will target the low-hanging fruit. For safer use of public Wi-Fi hot spots, SecurityKiss is a great tool. Should you stake your job or reputation on a promise of anonymity from this or any other Web service? No.
Facebook balks at a VPN login
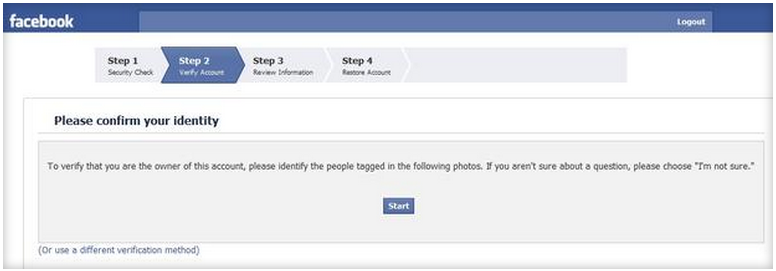
The only glitch I encountered while testing SecurityKiss occurred when I attempted to sign in to my Facebook account. For some reason, Facebook sent me through the four-step process of reactivating my account, which included identifying friends in photos from their Facebook profiles. (I could've used another method to verify my identity, according to the reactivation wizard.)
Just last week the U.S. Federal Trade Commission published the Wise Up About Wi-Fi page that offers tips for safe use of public Wi-Fi. Among the tips is the familiar advice to use encryption at all times (look for "https:" in the address header and the lock icon in the address bar or it the bottom status bar, depending on your browser).
The FTC's public-Wi-Fi safety page recommends that you heed your browser's warnings about unsafe sites; in November 2009 I compared the security features of five browsers: Internet Explorer, Firefox, Google Chrome, Safari, and Opera. While they differ in their approach, all five programs do a good job of preventing malicious sites from opening and malware from being downloaded and installed.
But there's not much a browser can do to protect against Wi-Fi snoops, particularly when using an unencrypted connection or visiting unencrypted sites. Browser add-ons such as the Electronic Frontier Foundation's free HTTPS Everywhere for Firefox will encrypt some--but not all--data traveling between your PC and the site you're visiting. (I described that program and other Firefox security add-ons in a post from last November.)
Another recommendation on the Wise Up About Wi-Fi page is to use a virtual private network to create a secure tunnel that protects all the data sent over the connection. The organization you work for may help you install and set up a VPN link to its internal network that you may also be able to use to secure a public Wi-Fi connection.
The do-it-yourself approach to VPN can be a difficult--especially if you try to configure Windows' built-in VPN service. After spending the better part of an afternoon attempting and failing to set up the Windows VPN, I threw up my hands and started looking for a simpler alternative. I found it in the free, OpenVPN-based SecurityKiss service.
Keeping VPN simple -- and registration-free
Last November's post on Firefox security add-ons included a link to the LogMeIn Hamachi VPN product (free for non-commercial use), as well as links to two free encryption programs: the open-source TrueCrypt and the non-open-source UltraVPN.
No other VPN service I've tested can match SecurityKiss for ease of use. You have to select "Open as administrator" when you install the program, but other than that added step, getting SecurityKiss set up is as straightforward as security gets.
When the installation completes, you'll find a SecurityKiss shortcut on the Start menu and the service's icon in the taskbar notification area. After you open the program, click the Connect button at the bottom of its window. After a few seconds, you'll see a message indicating that "you are now in the encrypted tunnel" and listing your local and external IP addresses.
The SecurityKiss window includes a graph of the amount of data you've transmitted and the time spent in encrypted mode. The free version's daily limit is 300MB, which is sufficient for the casual public Wi-Fi user. Paid packages cost from 4 euros (about $5.39) a month or 40 euros a year for up to 20GB of data per month, to 10 euros (about $13.48) a month or 100 euros a year for up to 80GB a month (the details are available on the company's Packages page).
The service's options let you switch servers and enable the VPN connection automatically on start-up. SecurityKiss claims to offer many other advantages for users, such as allowing access to sites that your employer or Internet provider may block, the ability to open ports that have been blocked on your PC, and "complete anonymity."
One of the nicest features of the free service is that it's available without having to register, which makes it a bit easier to believe the company's claim of complete anonymity. Still, I find it difficult to trust any such claim, in large part because anonymity would be difficult for anyone to prove. In my opinion, "complete anonymity" on the Internet is impossible.
That doesn't mean you can't make it tougher for snoops to find out about you, especially considering most online thieves will target the low-hanging fruit. For safer use of public Wi-Fi hot spots, SecurityKiss is a great tool. Should you stake your job or reputation on a promise of anonymity from this or any other Web service? No.
Facebook balks at a VPN login
The only glitch I encountered while testing SecurityKiss occurred when I attempted to sign in to my Facebook account. For some reason, Facebook sent me through the four-step process of reactivating my account, which included identifying friends in photos from their Facebook profiles. (I could've used another method to verify my identity, according to the reactivation wizard.)
Connecting to Facebook over SecurityKiss' VPN link required that I reactivate my account via a four-step process.
The reactivation process took less than a minute, and after disconnecting the VPN link I was able to sign in to the account as usual. None of the other half-dozen-or-so sites I logged in to over VPN required any extra steps, although their performance slowed down a bit -- as you would expect from use of any VPN service.
I'm not sure whether the Facebook account reactivation was part of Facebook's security precautions, nor whether other Web services might react similarly when you use them over a VPN connection. Since I'm not a big user of public Wi-Fi, a few such glitches are a small price to pay for the added level of security this free service provides. For frequent public Wi-Fi users, however, these types of sign-in problems could become irritating very quickly.
I'm not sure whether the Facebook account reactivation was part of Facebook's security precautions, nor whether other Web services might react similarly when you use them over a VPN connection. Since I'm not a big user of public Wi-Fi, a few such glitches are a small price to pay for the added level of security this free service provides. For frequent public Wi-Fi users, however, these types of sign-in problems could become irritating very quickly.