Menu
|
We're in the midst of a third civil war
|
|
What if they held a war and didn't bother to tell anyone about it? Even worse, what if America lost the war but we didn't find out until after the enemy had dismantled the last vestige of our democracy?
|
February 7, 2018: We're running out of words
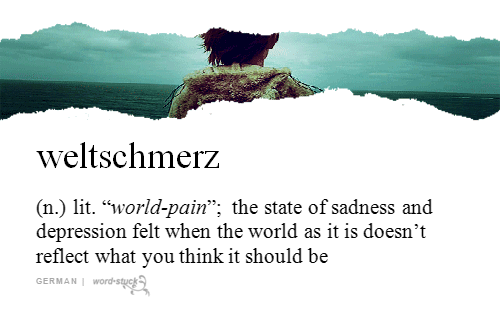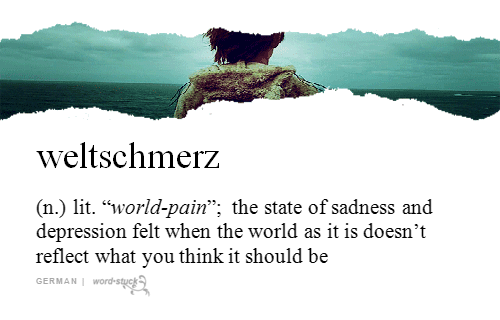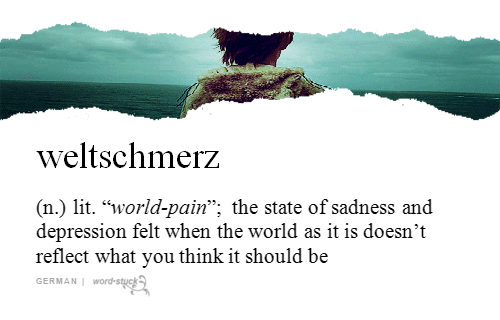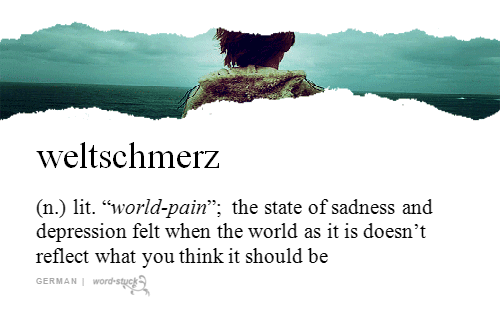
Sometimes the only way to accurately express new sentiments or describe novel situations is by raiding the vocabularies of other languages, or perhaps by fashioning some new vocabulary out of whatever phonemes are available. Here are some humble nominees for the Dictionary of 21st Century American Politics.
January 31, 2018: Help fight information pollution

When information is being used as a weapon, a healthy democracy requires the ability to distinguish accurate, complete information from its unfactual, incomplete, or misrepresented counterpart. People young and old need to be educated about finding reliable information sources and defending against unreliable ones.
January 24, 2018: Privacy infographic-palooza

Some pictures tell more than one story. This collection of images manages to pack a boatload full of privacy tips, advice, and guidance in relatively compact packages.
January 17, 2018: Another great reason to celebrate the life of Martin Luther King, Jr.

The American hero knew the struggle for economic justice would be long and hard-fought. King also identified the fight for racial equality as central to the dream of economic equality, going so far as to insist that a guaranteed income was the necessary first step toward the elimination of poverty.
January 10, 2018: Bye-bye, Fourth Amendment: Spy agencies feed tips to law enforcement

Using a technique called 'parallel construction,' the government hides the true source of evidence against defendants -- sources that are often unconstitutional. By concocting fictions about their investigative techniques, prosecutors prevent judges from ensuring the constitutionality of evidence presented in court.
January 3, 2018: Bring virtue to the internet by keeping trackers at bay
A new web tracking technique called session recording lets sites watch and play back every action you take on their pages -- even collecting the information you enter in web forms before you submit them. Another taps into your browser's password manager to extract your email address and other private data.
December 21, 2017: Can artificial intelligence give the tech industry a heart and save us from capitalism run amok?
Folks are lining up to bash the tech giants they pledged everlasting fealty to not so long ago. Some of the most vocal critics are members of the tech elite who now see the dangers inherent in their creations. Dangers they failed to spot until after the evils had made the new naysayers as rich as sultans.
December 13, 2017: Your email use is being tracked, and not just by marketers and spammers
A survey by a vendor of anti-tracking tools reports that 40 percent of the mail you receive from companies and 20 percent of the message you get from individuals include elements that report back to the sender, telling them when you opened it, where you were at the time, and other information about how you react to it.
December 6, 2017: Time to let others do the talking

There are so many potential topics for this Weekly, I became tongue-tied at the prospects of synthesizing it all down to a thousand-or-so words. That's why I decided to let the Big Thinkers share their thoughts on the Things That Really Matter Right Now without any (or much) intervention on my part.
November 29, 2017: Our front-row seat for the crashing and burning of the internet

The impending demise of net neutrality will ultimately result in an internet controlled by the handful of companies that control the platforms and pipes through which the data we rely on travels. Ceding ownership of the internet to big-name tech companies will stifle competition, freeze out little guys, and force tomorrow's innovative industry disrupters elsewhere.
November 16, 2017: Your location location location means money money money for trackers
A quick change to your Google Maps settings prevents the company from collecting and reselling information about where you've been, when you were there, and -- by inference -- what you did there. Plus: Set your phone apps to track and record your location only when you're actually using the programs.
November 8, 2017: YouTube: Unsafe for all ages

Google's video-streaming site has become the preferred platform for predators targeting children, and YouTube's built-in controls for protecting children from inappropriate content have been shown to be ineffective. The safest approach is to keep your kids off the service for good.
November 2, 2017: Birthday wishes

Wherein I get to pretend this is the day all my wishes come true. (That's a lot of pretending!)
October 25, 2017: That Weekly when everything was pretty good, or at least not so bad

For just one Weekly, can the gloom and doom be put on pause? Can something resembling good news be reported, just as a change of pace? It's worth a try... so long as you're willing to abide a splash of cynicism. After all, Trump is still President.
October 19, 2017: Addiction by design: Don't let tech products run your life

When we multitask 24/7, we compromise our ability to focus on the one thing that is most important right now, whether that one thing is a meeting with the boss, a first-run movie, or a warning about an approaching storm. Now is the time to enforce self-imposed limitations on when and how often we turn our attention to our digital devices -- before the devices start imposing limits on us.
October 4, 2017: Essential internet privacy tips, 2017 edition

Preventing your personal information from being shared indiscriminately isn't as onerous a process as you might think. Some simple precautions will go a long way toward ensuring your private data doesn't fall into the wrong hands.
September 27, 2017: Unreported news story: 'Algorithmic takeover' of journalism

Reporters are now trained to write stories in a way that maximizes clicks, regardless of whether the article tells the whole story, or is even factual. As Mark Twain said, "A lie can travel halfway around the world while the truth is putting on its shoes." When Google and Facebook tell the story, the truth might as well stay in bed.
September 22, 2017: The door slams shut on the open internet

A new web standard that gives copyright holders control over content, and the rescission of government net-neutrality protections signal a transfer of power from consumers to the internet services and media companies.
September 13, 2017: The best response to the Equifax breach: Don't deal with Equifax

The last thing you want to do is provide even more personal information to the company that just proved beyond doubt that it cannot be trusted with it. There are many simple, straightforward ways to minimize the chances that you'll be a victim of identity theft as a result of the Equifax data breach.
September 6, 2017: In business and government, the bullies are calling the shots

The more power someone has, the more likely they are to abuse that power. A handful of tech companies now possess more power than anyone could've imagined just a few years ago. Google, Facebook, and a few others are now indispensable. Who is protecting us from the internet's private utilities?
August 30, 2017: There's no stopping tech giants' surveillance for profit

Security experts insist that only government regulation can rein in the unfettered collection and commercialization of our private information by a handful of data monopolies. While European regulators will soon require more transparency and the informed consent of consumers, people in the U.S. continue to put more faith in private corporations than they put in their own government.
August 23, 2017: How to deter 'fingerprint' trackers from identifying your computers and devices
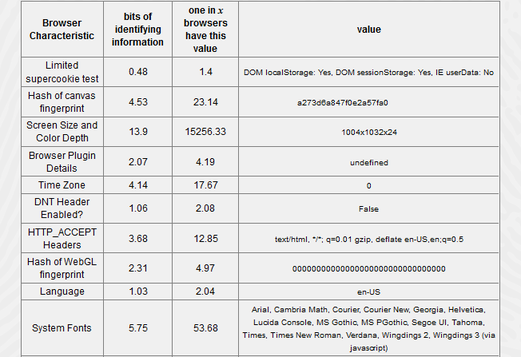 Source: no-sec.org - https://no-sec.net/fingerprinting-of-web-browsers-and-the-consequences-for-privacy/
Source: no-sec.org - https://no-sec.net/fingerprinting-of-web-browsers-and-the-consequences-for-privacy/
New techniques for keeping a close watch on your internet activities require a bit more diligence than sweeping out and blocking web tracking cookies. Several free tools are available to take a big bite out of the collection of your private information by services, ad networks, and the government.
August 16, 2017: That was the week that was, 2017 revival

We've been here before, and not so long ago -- August of 1939, to be exact. This is our time to quash tyranny and restore democracy, to say "no" to hate and "yes" to love, to chase Nazis and white supremacists back into the disease-infested holes they so recently crawled out of -- including a despicable "so-called President."
August 9, 2017: Find the internet security level that's right for your needs

Make sure the security features built into your PC or device are enabled and up-to-date; use passwords that are long and memorable; enable two-factor authentication for access to accounts containing private data; and encrypt a little or a lot, depending on how much protection your data needs.
August 3, 2017: Internet Media 101: The bigger the lie, the greater the profit

Internet news substitutes 'affective engagement' for traditional editorial and reportorial principles of newsworthiness, accuracy, and completeness. The algorithms used by Facebook and other news feeds are reprogramming our brains based on their comprehensive -- and growing -- record of our activities.
July 26, 2017: Cyber-crimestoppers: How individuals and companies help nab internet crooks

Criminals have taken to the internet in a big way, targeting people and businesses of all descriptions. An army of mostly volunteer hackers are assisting law enforcement in detecting, arresting, and prosecuting the perpetrators of online scams, malware, ransomware, and other digital wrongdoing.
July 19, 2017: A free press: The antidote to authoritarianism

When Americans choose to sacrifice their freedom in exchange for a promise of improved security, they sell out the principles that are the foundation of government of, by, and for the people. The bad choices made in the aftermath of 9/11 have led inexorably to the election of the most damaging politician in U.S. history.
July 12, 2017: A novel concept: Let consumers decide which personal data to share with trackers
The use of ad blockers continues to increase, which threatens publishers already pressured by declining revenues. Studies indicate people are willing to allow ad networks and publishers to collect their private information, but only if consumers are given the power to choose what gets shared and what stays private.
July 5, 2017: We're in the midst of the third American Civil War, and democracy is losing

Fundamental rights and Constitutional protections are under a heavy assault by corporations hiding behind their puppet Republican party, which now controls all three branches of government. The way to fight back and preserve our republic is by withholding our attention and our money -- the few greenbacks we have left.
June 28, 2017: Keep online trackers at bay without breaking a sweat

Sites, apps, and advertisers that collect information about us have gone far beyond cookies to keep close tabs on what we do, and when and where we do it. A few free tools and a little smartphone location scrubbing go a long way toward minimizing the amount of your private data that is gathered and shared.
June 21, 2017: Pleas for civility meet with... incivility, but that's okay

Before we can promise to treat each other with courtesy and respect, we have to come to a consensus on what constitutes civil behavior. Interrupting a speaker to shout "Liar!" passes the civility test for some misguided politicos. What we need is a return to niceness for its own sake.
June 14, 2017: The price we pay for allowing unbridled digital surveillance
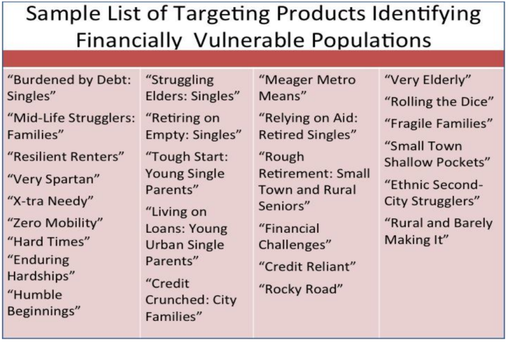
Companies of all types use the detailed dossiers they have compiled on billions of people to determine consumers' creditworthiness, decide whether they qualify for health insurance, and other purposes that extend far beyond serving up targeted advertising.
June 7, 2017: Privacy protections may form the basis of antitrust actions against internet giants

Consumers and antitrust regulators are beginning to recognize that Google, Facebook, Amazon, Apple, and Microsoft are no longer merely dominating tech markets, they are the tech markets. Stifled competition and exorbitant profits are the price we all pay for services that morph into irreplaceable and unassailable platforms.
May 31, 2017: Privacy tips for the most vulnerable: Children and seniors

Preventing your personal information from falling into the wrong hands is difficult enough for seasoned internet veterans. Imagine the challenge of protecting the privacy of the two populations who are the most trusting and the least tech-savvy.
May 24, 2017: Applying Fourth Amendment search protections to data in the cloud

Government prosecutors are attempting to expand the geographic scope of search warrants to include electronic information that is stored on computers outside the U.S. Google's defense of Gmail data held overseas states that warrants should be based on the user's location, not the data's.
May 17, 2017: Just when you thought you couldn't be tracked any closer....

Camera-equipped outdoor display ads use biometrics to determine your mood when you walk by and tailor the ad to how you're feeling. Ultrasonic beacons are broadcast in stores and into your home via TV to gain access to data on your phone or device. We are being bombarded by digital snoops!
May 10, 2017: Facebook addiction turns users into marketing guinea pigs

The ubiquitous social network's ability to manipulate and capitalize on people's emotions gives Facebook unprecedented power to shape the world into whatever form its advertisers prefer -- including the ability to swing elections in favor of whichever candidate pays Facebook the most money.
May 3, 2017: America: A tale of two countries
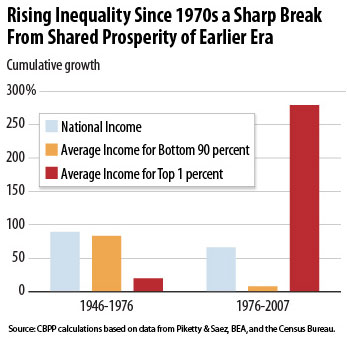
According to one MIT economics professor, the key to re-establishing a U.S. middle class is to spend less on military and more on people and infrastructure: Eliminate the debtor class, end mass incarceration, keep public services public, and tax both the income of the rich and their capital.
April 26, 2017: The internet: Destroyer of truth, justice, and the American Way

Obviously, there is no longer any such thing as 'politics as usual.' That doesn't mean we're prisoners of a New Normal where any web service can be gamed by anonymous humans and their bot armies. Work has begun to ensure machines work for the good of all humans, not just for the humans who own and control the machines.
April 19, 2017: The death and ultimate rebirth of the public internet

A handful of giants control the internet and have leveraged that control to become the most valuable corporations in the world. Work has begun on publicly controlled alternatives to internet services that have made a handful of men wealthy and left millions unemployed.
April 12, 2017: An internet dinosaur spits in the eye of extinction

In the digital universe, success is measured in numbers: more page views, more eyeballs, more followers, more ads, more money. What kind of a nut would do it any other way? Certainly not one ready for the end of net neutrality and the dawning of the age of censorship.
April 5, 2017: Trust Busters 2.0: Dismantling modern monopolies

Thirty-five years of laissez-faire sentiment toward consolidation in industries of all types has led to barely regulated monopolies that discourage innovation and reward the very few at the expense of the very many. Our democracy is imperiled by the concentration of wealth and political power.
March 29, 2017: Simple, free ways to lock down your private data
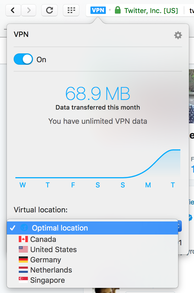
The Opera browser offers a built-in virtual private network that blocks your ISP and other internet services from recording and sharing your browsing history. Opera also features an ad blocker, but you'll still need two free privacy add-ons from the Electronic Frontier Foundation to complete your privacy arsenal.
March 22, 2017: Let big data benefit consumers, not marketers

In the 'post-marketing' era, our private information will be shared with the organizations we choose to do business with, but on our terms and in ways that serve us. The first step is to eliminate the profit-taking and manipulation of soon-to-be-obsolete marketers.
March 8, 2017: Gig economy changes what it means to be an 'employee'

Concocting a third category of worker between "employee" and "independent contractor" creates another opportunity for employers to take advantage of their, um, employees. A simpler and more reasonable approach is to codify the court's broad, adaptable definition of "employee," which describes Uber drivers to a "T".
March 1, 2017: Privacy: There's just no percentage in it
The businesses and government agencies that collect and sell personal information about their customers will have fewer restrictions on their data-collection operations as more federal regulations are quashed.
December 13, 2016: Practical security precautions for the worst-case scenario

The world would be a different place today if everyone encrypted their communications and stored files. In the face of direct threats to our Constitutional rights to speak freely and to be secure in our "persons, houses, papers, and effects," personal data-security protections become our civic duty.
December 6, 2016: The Rough Beast's lies indicate his intention - Just like the Nazis
The media and private citizens alike have a responsibility to call BS when confronted by lies told by government officials and their surrogates. But beyond fact-checking, we must acknowledge that the lies are intended only as advance justification for the crimes the liars are about to commit.
November 29, 2016: Government phone searches: Return of the 'general warrant'

A single warrant issued by a magistrate in a federal district court was 'served' on 8,000 different computers located in 120 countries. This is a scope of search unprecedented since the 18th century British writs of assistance, opposition to which marked the 'birth of the child Independence,' according to John Adams.
November 23, 2016: Before the deluge: Spend your attention wisely

News media and web services both make their money by converting our attention into cold, hard cash. It doesn't matter whether it's good attention or bad attention, real or fake - it's all money to them.
November 16, 2016: You can't hide from facial-recognition systems - Or can you?

Law enforcement agencies and web services are going full steam ahead on the use of technology that identifies people based on their face or other physical feature. What's lagging far behind is any oversight of their use of our biometric data to identify us without our knowledge or consent.
November 8, 2016: The 'consumer boycott' of web advertising is gaining momentum
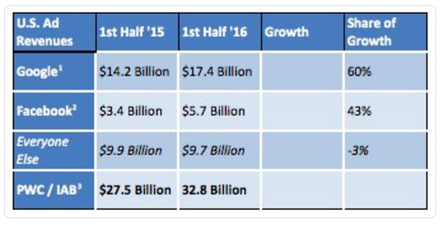
The failure of online advertisers to keep malware off their networks makes the use of ad-blocking browser extensions a security essential. The proliferation of ad-based malware hasn't affected the growing ad revenue of Google and Facebook, though other sites are seeing their ad revenue decline.
November 1, 2016: Encryption: It's not just for banking anymore

Not many people need to encrypt every message they send and every file they store, but everyone needs to protect some of their communications and documents by applying encryption. For businesses in particular, an encryption-everywhere strategy may be the safest bet.
October 25, 2016: A call to action: Stop the surveillance - by web services, apps

There is no 'deal': The internet has never been free, and we have never given the web services and applications that collect and monetize our personal information explicit permission to do so. It's time to turn the tables.
October 18, 2016: Web ad networks are malware authors' best friends

Internet criminals are taking advantage of the targeting offered by online ad networks to infect the computers and phones of the most vulnerable among us. Increasingly, this means people who aren't yet using an ad-blocking browser extension.
October 11, 2016: Privacy is becoming fashionable - Yippee!

Young people are showing signs of rejecting the quest for celebrity, choosing instead to be more circumspect than their parents and grandparents when it comes to sharing the details of their lives.
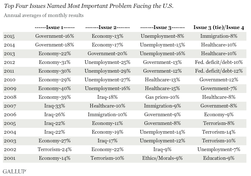
October 4, 2016: How do we bridge the growing media and political divides?
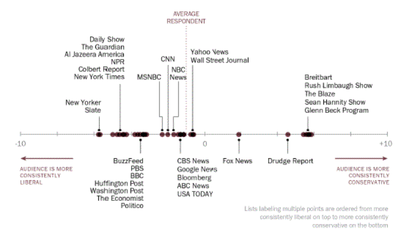 (Click image to enlarge)
(Click image to enlarge)
Even fact checkers are now accused of political bias - primarily be politicians. In the post-truth era, when no one can agree on what constitutes a 'fact', finding common ground becomes the first great challenge.
September 27, 2016: Safety essentials: 10-step security revisited, 11 years later

Much has changed since 2005's PC-security guide: Windows offers better malware protection, and opening your email isn't as risky as it once was. Yet malware threats are more sophisticated and more dangerous than ever, which makes these basic security tips more important than ever.
September 20, 2016: Simple ways to limit the private information you surrender on the web

A handful of easy-to-implement precautions - and a little bit of mindfulness - can may you feel like you're in charge of the collection and dissemination of your personal data. Well, some of the private info, anyway.
September 13, 2016: Top 10 reasons why people hate listicles - and yes, this is a joke headline

Triple play: The lucrative business of internet hoaxes; a tip of the hat to an internet freedom (of information) fighter; and why you should be concerned about the private data collected by fitness trackers - not to mention more intimate personal electronics.
September 6, 2016: Why internet voting is a terrible idea

There is no way to secure the internet, and there is no way to protect the single most important activity to a thriving democracy without reliable security. That's why the internet - as it exists today - will never be a suitable medium for casting ballots.
August 30, 2016: No consent needed for ISPs to scan email and create ad-targeting profiles of non-customers

A recent decision by the U.S. District Court of Northern California finds that ISPs scanning the emails sent to and received by non-customers, and targeting ads based on teh profiles, doesn't violate the Wiretap Act or the California Invasion of Privacy Act.
August 23, 2016: The web is broken - Guess who's trying to fix it?

What began 25 years ago as a decentralized network for sharing information has become the province of a handful of mega-services whose fortunes are built on the collection and use of our information.
August 16, 2016: Supreme Court throws 'fruit of the poisonous tree' doctrine under the bus

By broadening the power of police to conduct a warrant search on anyone, even when the officer lacks a reasonable suspicion of wrongdoing, the decision in Utah v. Strieff makes everyone subject to 'legal verifcation' at any time.
August 9, 2016: Dragging the online trackers - kicking and screaming - into the light of day

It's nearly impossible to avoid being tracked by web services and their ad-tech partners. What's neeed is transparency about what information is being collected, who it's shared with, and how it's being used.
August 2, 2016: Silly questions: Who 'owns' video captured by police? And does Facebook really 'enhance' privacy?

The doublespeak is coming hot and heavy this election season, and it isn't limited to politics. Imagine a personal-info sinkhole like Facebook making you more private. Now there's a stretch!
June 28, 2016: It's official - No expectation of privacy on the internet

There's no warrant requirement when the law wants at your computer, says one District Court judge, because we're all just data-theft victims waiting to happen.
June 21, 2016: How to wrest control of our government away from corporations

In an era when public opinion has zero impact on policy, only a concerted effort by U.S. citizens can liberate our country from the clutches of the billionaire class.
June 14, 2016: The fight against privacy smashers continues

Tech giants continue their unwavering, under-the-radar assault on the privacy of their customers -- despite a growing number of legal challenges.
May 31, 2016: Publishers are losing the battle against their ad-blocking visitors -- So what's next?
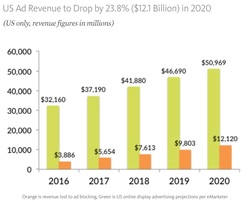
The ad-tech industry has a chance to win back the trust of consumers by being more transparent in how ad networks track people on the Internet and mobile phones.
May 25, 2016: Tech companies resist government attempts to broaden definition of 'personal information'

The more we rely on mobile and Internet services, the less opportunity we have to protect our privacy.
May 17, 2016: Privacy threats on parade

People are starting to be more careful about the personal information they share with Internet services, which has a chilling effect on both free speech and economic activity.
May 10, 2016: Government goes dark as private lives are exposed

Wait a minute. Just as our private lives are exposed at unprecedented levels, government agencies – particularly the courts – are hiding all their activities from public scrutiny. When exactly did things start to go topsy-turvy?
May 3, 2016: The great online-advertising swindle

Google and Facebook accounted for 85 percent of all new online ad spending in the first quarter of 2016. According to a Morgan Stanley executive, $1 of each $3 generated by online ads is fraudulent. Where does that leave Google and Facebook?
April 26, 2016: Modern news media: Too big not to fail?, April 26, 2016

Instead of constantly seeking more and more eyeballs with schlock, Internet publishers need to tell the best stories to the right audience.
April 20, 2016: Internet Confidential: How to establish a privacy right on the public Internet

Private data retains its confidentiality even after it has been shared with an Internet service. Yet in the absence of legal privacy protections, sharing with one is sharing with all.
April 13, 2016: The new browser wars: Thou shalt not block our ads and trackers

Web publishers threaten legal action against a new browser that replaces their ads, but what they really want is unfettered access to their visitors' personal data.
April 6, 2016: FCC to regulate ISP data collection, but Google, Facebook off the hook

New rules require Internet service providers to get customers' explicit consent before collecting certain private data. Will big-name web services be held to the same standards?
March 29, 2016: Five questions, no answers

Expansive appetites -- for resources and information -- keep the economy growing, but for how long? Why can't learning be fun? And what's with those too-tight suits?
March 23, 2016: How to save the Internet: Ratchet down the anonymity, rein in the ads

When people own their words, they're more civil. When ad networks run amok, malware authors have a field day.
March 15, 2016: How we lose ourselves in private data collection

The personal information we provide to data collectors becomes the property of the collectors, who can do with it nearly as they please.
March 8, 2016: People tracking is about to get even creepier

Mobile phones and other wired devices serve up reams of information about where we are, what we do, when we do it, and increasingly, what we're thinking.
March 2, 2016: Silicon Valley's long-standing connections to the U.S. government

The public sector helped create and foster Silicon Valley, and only the public sector can ensure the industry puts justice and humanity first.
March 2, 2016: Campaign 2016: The first social-media election

The most likely source of election information for Millennials is social media, while Baby Boomers get most of their election information from cable news. As young people become more politically active, social media's influence will soar.
February 24, 2016: How to build the future of work
Our children's well-being depends on businesses and government working together to rebuild our economic and educational infrastructure.
February 24, 2016: The end is near for passwords (not really)
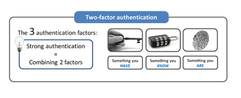
Two-factor authentication verifies your identity by adding something you have (like a phone) or something you are (like a fingerprint) to something you know (a password).
February 16, 2016: Why it's a bad idea to trust private companies with the job of protecting our rights

Tech giants will often look after the interests of their customers -- unless doing so runs counter to their own interests.
February 9, 2016: Your Internet life is an open book: The dark side of online-ad profiling
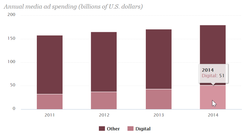
The more personal information you share, the easier it is for companies to use what they know about you to their benefit, and often to your detriment.
February 2, 2016: Why don't Americans care as much about privacy as Europeans do?

Soon Europeans will have privacy protections that U.S. citizens lack. Why? Because they demanded them!
January 26, 2016: New fronts open in the battle against privacy-invading online ads

From inside and outside government, plans for reining in the out-of-control ad networks are gaining traction.
January 19, 2016: Fifteen ways to stay safe on the Internet

The security of our personal information is in the hands of the companies we deal with, but there's still plenty we can do to minimize the chances that we'll be victimized.
January 13, 2016: Prepare for the inevitable theft of your personal information

There isn't much we can do to prevent the collection of sensitive personal data, but diligent monitoring and other precautions can minimize the damage of a data breach.
January 5, 2016: 'Hey gang, let's put on a government!'
We've never been more estranged from our government, which is no longer of, by, or for the people. The time is right for a direct democracy, but only if we're willing to do the heavy lifting.
December 22, 2015: The appropriate response to living in a surveillance state: Ignore it
Don't let the threat of an irrational response by the mobocracy dissuade you from expressing a legitimate dissenting or unpopular opinion.
Legal shorts for December 22, 2015: Citizens have zero influence on public policy, and a dark chapter of court history resurfaces
Politicians are tone-deaf to 'average Americans'
"The preferences of the average American appear to have only a minuscule, near-zero, statistically nonsignificant impact upon public policy."
“[P]olicymaking is dominated by powerful business organizations and a small number of affluent Americans….”
Martin Gilens and Benjamin Page, Testing Theories of American Politics: Elites, Interest Groups, and Average Citizens
When it comes to who influences American politics, populism has proven to be the exception rather than the rule. As Slate’s Boer Deng points out in an April 24, 2014, essay, the Founding Fathers were most interested in protecting the rights of property owners, who were a minority of citizens in the 18th and 19th centuries.
Some 80 years after the height of populism in America – President Franklin Delano Roosevelt’s New Deal – we’re about as far away from populism as we’ve ever been. Democrats ignore public opinion just as much as Republicans these days. One of the first policy initiatives to reverse the trend of the rich paying less and the poor paying more is President Barack Obama’s Affordable Care Act, which Deng states serves as a surcharge on the rich.
As nice as it would be to believe populism is making a comeback, it will take more than a good showing by populist candidate Bernie Sanders in his run for the Democratic Presidential nomination in 2016 to put us average, everyday folk back in the politicians’ good graces. It starts with a top-to-bottom reformation of the corrupt electoral process, which in its current state makes permanent fundraising the top priority for anyone in or seeking office. So what do you say we all take Harvard Professor Lawrence Lessig’s advice and Fix Democracy First!
--------------------------------------------------------------------------
The awful, terrible, horrible Korematsu decision rears its ugly head once again
In the June 25, 2015, Weekly I cited Bush v. Gore as the worst decision in the history of the U.S. Supreme Court, in large part because the case was decided along completely political lines and had no substantial legal underpinnings. In a December 18, 2015, post, Constitution Daily’s Scott Bomboy reports on the three worst Supreme Court decisions, according to a consensus of Constitution scholars of every political stripe: Dred Scott (African-Americans aren’t full-fledged citizens); Plessey (separate but equal is constitutional); and Korematsu (it’s constitutional to round up and imprison citizens during times of war based solely on their nationality)
After Republican Presidential candidate Donald Trump cited FDR’s internment of Japanese Americans during World War II as rationale for barring Muslims from entering the U.S., Korematsu was held up as the legal justification for such a ban. Bomboy points out the most obvious difference: Trump wants to ban people based on their religion, while Korematsu allowed them to be imprisoned based on their ethnicity.
While the broad consensus is that the Korematsu decision was a tragic mistake that shouldn’t be repeated, the case remains “good law,” according to Temple Law Professor Peter Spiro, as quoted in a December 8, 2015, New York Times column. Bomboy quotes Justice Antonin Scalia as stating that “another Korematsu situation” could happen.
In a December 18, 2015, op-ed piece in the Los Angeles Times, John Inazu and Karen Tani, whose grandparents were U.S. citizens interred during World War II, write that the legacy of Korematsu for every American is that our “freedom could be taken, [our] rights ignored, and [our] lives disrupted, solely because of [our] ancestry.” Two wrongs, three wrongs, four wrongs – add up any number of wrongs you want, you still won’t make a single right.
"The preferences of the average American appear to have only a minuscule, near-zero, statistically nonsignificant impact upon public policy."
“[P]olicymaking is dominated by powerful business organizations and a small number of affluent Americans….”
Martin Gilens and Benjamin Page, Testing Theories of American Politics: Elites, Interest Groups, and Average Citizens
When it comes to who influences American politics, populism has proven to be the exception rather than the rule. As Slate’s Boer Deng points out in an April 24, 2014, essay, the Founding Fathers were most interested in protecting the rights of property owners, who were a minority of citizens in the 18th and 19th centuries.
Some 80 years after the height of populism in America – President Franklin Delano Roosevelt’s New Deal – we’re about as far away from populism as we’ve ever been. Democrats ignore public opinion just as much as Republicans these days. One of the first policy initiatives to reverse the trend of the rich paying less and the poor paying more is President Barack Obama’s Affordable Care Act, which Deng states serves as a surcharge on the rich.
As nice as it would be to believe populism is making a comeback, it will take more than a good showing by populist candidate Bernie Sanders in his run for the Democratic Presidential nomination in 2016 to put us average, everyday folk back in the politicians’ good graces. It starts with a top-to-bottom reformation of the corrupt electoral process, which in its current state makes permanent fundraising the top priority for anyone in or seeking office. So what do you say we all take Harvard Professor Lawrence Lessig’s advice and Fix Democracy First!
--------------------------------------------------------------------------
The awful, terrible, horrible Korematsu decision rears its ugly head once again
In the June 25, 2015, Weekly I cited Bush v. Gore as the worst decision in the history of the U.S. Supreme Court, in large part because the case was decided along completely political lines and had no substantial legal underpinnings. In a December 18, 2015, post, Constitution Daily’s Scott Bomboy reports on the three worst Supreme Court decisions, according to a consensus of Constitution scholars of every political stripe: Dred Scott (African-Americans aren’t full-fledged citizens); Plessey (separate but equal is constitutional); and Korematsu (it’s constitutional to round up and imprison citizens during times of war based solely on their nationality)
After Republican Presidential candidate Donald Trump cited FDR’s internment of Japanese Americans during World War II as rationale for barring Muslims from entering the U.S., Korematsu was held up as the legal justification for such a ban. Bomboy points out the most obvious difference: Trump wants to ban people based on their religion, while Korematsu allowed them to be imprisoned based on their ethnicity.
While the broad consensus is that the Korematsu decision was a tragic mistake that shouldn’t be repeated, the case remains “good law,” according to Temple Law Professor Peter Spiro, as quoted in a December 8, 2015, New York Times column. Bomboy quotes Justice Antonin Scalia as stating that “another Korematsu situation” could happen.
In a December 18, 2015, op-ed piece in the Los Angeles Times, John Inazu and Karen Tani, whose grandparents were U.S. citizens interred during World War II, write that the legacy of Korematsu for every American is that our “freedom could be taken, [our] rights ignored, and [our] lives disrupted, solely because of [our] ancestry.” Two wrongs, three wrongs, four wrongs – add up any number of wrongs you want, you still won’t make a single right.
December 17, 2015: Separating the bitcoin hype from the blockchain substance

Blockchain promises to be the next Internet-sized disrupter. But not yet. Check back in about a decade.
Shorts for December 17, 2015: Trump's legal ineptitude, and eight ways the world is getting better
Trump’s lawyer is as clueless as the candidate
Donald Trump suspected that a SuperPAC backing Jeb Bush was about to run ads critical of the Republican Presidential front-runner. Trump had his lawyer, Alan Garten, send the SuperPAC a cease-and-desist letter before the ads ran. As Above the Law’s Staci Zaretsky reports in a December 11, 2015, article, there were only a few small problems with the letter.
The biggest problem was that the letter was sent to the wrong SuperPAC. Jeb Bush’s SuperPAC is named Right to Rise USA, while the warning was issued to one named Right to Rise PAC, Inc. This group supports conservative candidates generally, one of whom is Jeb Bush. Charles Spies, the lawyer for Right to Rise PAC, responded with a letter to Garten that is a classic in the genre, according to Zaretsky.
In his letter, Spies recommends that Garten take a break from his bankruptcy filings on behalf of Trump to review the Supreme Court’s decision in New York Times v. Sullivan, which states the rules for defamation and prior restraint of free speech. Spies also notes that just as his client is taking a crash course in the basics of foreign affairs, Garten could benefit from a quick review of election laws (the letter included a complaint Spies filed against Trump with the Federal Elections Commission calling for an investigation of Trump’s expenditures).
Should Trump actually win the 2016 Presidential election – gulp! – Spies asks whether Garten will be the person writing the cease-and-desist letters to Russian President Vladimir Putin.
----------------------------------------------------------------------------
Eight ways the world is changing for the better
These days, it’s difficult to get more than halfway through your daily newspaper (or online newsfeed) without coming to the conclusion that the wheels have officially come off and the world is careening toward the precipice at breakneck speed. Then somebody comes along and reminds you that maybe things aren’t all that bad, and in fact there are some fundamentally good changes underway.
That’s how I felt as I read Gustavo Tanaka’s October 6, 2015, essay on Medium entitled “There is something extraordinary happening in the world.” Tanaka states that he recently freed himself from the “standard-procedure society” and discovered that tremendous changes are going on that most of us are not yet fully cognizant of. He lists eight reasons for this belief. (Note: This is not your typical “listicle.”)
The change that resonated the most with me is that “No one can stand the employment model any longer.” People hate their corporate jobs. The work lacks purpose, leaving employees feeling empty and leading an increasing number of people to become entrepreneurs. The nature of entrepreneurship is changing as well, according to Tanaka. Rather than focusing on fundraising (which perpetuates the blind chase for profits that afflicts so much corporate work), the goal is to collaborate with other entrepreneurs to create something useful and meaningful for consumers and producers alike.
Tanaka claims that the full impact of the Internet as a great leveler of power is just now taking hold with people. Slowly, Big Media’s control of the news is collapsing. (A future Weekly will look at why the mainstream media is ignoring the 2016 Presidential candidate who is by far the most popular contender on the Internet, Bernie Sanders.)
Also dying a slow death is the media’s non-stop message to consume, consume, consume. So-called lowsumerism is taking hold, according to Tanaka. People are increasingly willing to purchase used products and to share and barter. Overspending and crass consumerism have become déclassé. We’re more concerned than ever about the quality and healthiness of the food we eat, and we’re purchasing more food and other products from local producers.
The last two changes Tanaka cites are the ones with the most potential impact for society. We’re rethinking the way we teach our children as we realize the 19th and 20th century approaches to education do a disservice to students, parents, and communities. And last but not least, spirituality is becoming the center of people’s lives. As Tanaka puts it, “we’ve come to the edge of reason and rationality.” Meditation and other mindfulness exercises are taking hold in schools, workplaces, and healthcare settings.
I believe that people worldwide thinking peace helped bring us back from the precipice of nuclear war in the 1980s. We can do the same peace-thinking today to turn the tide away from the hate that threatens to destroy us, and toward the love that promises to redeem us.
That’s my message to you this holiday season: Think peace, please! Today and every day.
Donald Trump suspected that a SuperPAC backing Jeb Bush was about to run ads critical of the Republican Presidential front-runner. Trump had his lawyer, Alan Garten, send the SuperPAC a cease-and-desist letter before the ads ran. As Above the Law’s Staci Zaretsky reports in a December 11, 2015, article, there were only a few small problems with the letter.
The biggest problem was that the letter was sent to the wrong SuperPAC. Jeb Bush’s SuperPAC is named Right to Rise USA, while the warning was issued to one named Right to Rise PAC, Inc. This group supports conservative candidates generally, one of whom is Jeb Bush. Charles Spies, the lawyer for Right to Rise PAC, responded with a letter to Garten that is a classic in the genre, according to Zaretsky.
In his letter, Spies recommends that Garten take a break from his bankruptcy filings on behalf of Trump to review the Supreme Court’s decision in New York Times v. Sullivan, which states the rules for defamation and prior restraint of free speech. Spies also notes that just as his client is taking a crash course in the basics of foreign affairs, Garten could benefit from a quick review of election laws (the letter included a complaint Spies filed against Trump with the Federal Elections Commission calling for an investigation of Trump’s expenditures).
Should Trump actually win the 2016 Presidential election – gulp! – Spies asks whether Garten will be the person writing the cease-and-desist letters to Russian President Vladimir Putin.
----------------------------------------------------------------------------
Eight ways the world is changing for the better
These days, it’s difficult to get more than halfway through your daily newspaper (or online newsfeed) without coming to the conclusion that the wheels have officially come off and the world is careening toward the precipice at breakneck speed. Then somebody comes along and reminds you that maybe things aren’t all that bad, and in fact there are some fundamentally good changes underway.
That’s how I felt as I read Gustavo Tanaka’s October 6, 2015, essay on Medium entitled “There is something extraordinary happening in the world.” Tanaka states that he recently freed himself from the “standard-procedure society” and discovered that tremendous changes are going on that most of us are not yet fully cognizant of. He lists eight reasons for this belief. (Note: This is not your typical “listicle.”)
The change that resonated the most with me is that “No one can stand the employment model any longer.” People hate their corporate jobs. The work lacks purpose, leaving employees feeling empty and leading an increasing number of people to become entrepreneurs. The nature of entrepreneurship is changing as well, according to Tanaka. Rather than focusing on fundraising (which perpetuates the blind chase for profits that afflicts so much corporate work), the goal is to collaborate with other entrepreneurs to create something useful and meaningful for consumers and producers alike.
Tanaka claims that the full impact of the Internet as a great leveler of power is just now taking hold with people. Slowly, Big Media’s control of the news is collapsing. (A future Weekly will look at why the mainstream media is ignoring the 2016 Presidential candidate who is by far the most popular contender on the Internet, Bernie Sanders.)
Also dying a slow death is the media’s non-stop message to consume, consume, consume. So-called lowsumerism is taking hold, according to Tanaka. People are increasingly willing to purchase used products and to share and barter. Overspending and crass consumerism have become déclassé. We’re more concerned than ever about the quality and healthiness of the food we eat, and we’re purchasing more food and other products from local producers.
The last two changes Tanaka cites are the ones with the most potential impact for society. We’re rethinking the way we teach our children as we realize the 19th and 20th century approaches to education do a disservice to students, parents, and communities. And last but not least, spirituality is becoming the center of people’s lives. As Tanaka puts it, “we’ve come to the edge of reason and rationality.” Meditation and other mindfulness exercises are taking hold in schools, workplaces, and healthcare settings.
I believe that people worldwide thinking peace helped bring us back from the precipice of nuclear war in the 1980s. We can do the same peace-thinking today to turn the tide away from the hate that threatens to destroy us, and toward the love that promises to redeem us.
That’s my message to you this holiday season: Think peace, please! Today and every day.
December 10, 2015: Re-reinterpeting our constitutional right to bear arms

If we truly want to abide by the intent of the Framers, we would require gun owners to form 'well regulated' militia.
Shorts for December 10, 2015: Big data applied to 120 years of yearbook photos, 2015's most popular how-to's, Google violates the student pledge, and the Pope says 'no' to killer robots
Data mining converts millions of high school yearbook pictures into a single aggregate image, one male, one female, for each of the past 12 decades. The upshot: We’re smiling more now than ever.
MIT Technology Review, November 24, 2015
Lifehacker's most popular how-to guides of 2015 range from the expected (how to jailbreak your iPhone, how to do a clean install of Windows 10) to the offbeat (the polar-opposite how to cure bad breath and how to fart in public unobtrusively) to the worrisome (how to clean yourself, how to stop buying stuff you don’t need) to the eminently practical (how to get a bartender’s attention without being a jerk). If only I knew that last one 40 years ago.
Kristin Wong, Lifehacker, December 7, 2015
Is Google illegally spying on students? That’s what the Electronic Frontier Foundation believes is happening with a feature on the Google Chromebooks running Apps for Education, which many students are getting for free. The Chrome Sync function that lets you access your favorites and other settings on different systems is on by default on Chromebooks. EFF claims Google is using the information it is collecting about students for purposes unrelated to education. This violates the Student Data Privacy pledge, which the company signed previously. Google is also sharing the student information it’s collecting with third parties, which is also a violation of the pledge, according to the EFF. Google denies all the EFF’s allegations.
Just in case, the EFF provides instructions for changing the default settings on a student’s Chromebook to prevent the private data from being collected.
Jackie Wertz, JD Supra Business Advisor, December 8, 2015
The Pope says killer robots are a bad idea, and that sounds about right to me. Then again, I’m no militiaman.
Catholic News Agency, December 2, 2015
MIT Technology Review, November 24, 2015
Lifehacker's most popular how-to guides of 2015 range from the expected (how to jailbreak your iPhone, how to do a clean install of Windows 10) to the offbeat (the polar-opposite how to cure bad breath and how to fart in public unobtrusively) to the worrisome (how to clean yourself, how to stop buying stuff you don’t need) to the eminently practical (how to get a bartender’s attention without being a jerk). If only I knew that last one 40 years ago.
Kristin Wong, Lifehacker, December 7, 2015
Is Google illegally spying on students? That’s what the Electronic Frontier Foundation believes is happening with a feature on the Google Chromebooks running Apps for Education, which many students are getting for free. The Chrome Sync function that lets you access your favorites and other settings on different systems is on by default on Chromebooks. EFF claims Google is using the information it is collecting about students for purposes unrelated to education. This violates the Student Data Privacy pledge, which the company signed previously. Google is also sharing the student information it’s collecting with third parties, which is also a violation of the pledge, according to the EFF. Google denies all the EFF’s allegations.
Just in case, the EFF provides instructions for changing the default settings on a student’s Chromebook to prevent the private data from being collected.
Jackie Wertz, JD Supra Business Advisor, December 8, 2015
The Pope says killer robots are a bad idea, and that sounds about right to me. Then again, I’m no militiaman.
Catholic News Agency, December 2, 2015
December 2, 2015: How open data can help save the world

There's a treasure trove of information in government databases. Providing this data to the public can make government more efficient and more effective.
November 18, 2015: Consumers may be ready to pay for an ad-free, tracking-free Internet

The 'behavioral advertising revenue model' is in dire need of a fix, according to researchers. A pay option for popular web services can benefit customers and providers.
Shorts for November 18, 2015: Don't fall for a fake charity, and go for the silver! (health plan)
Before you donate this holiday season, check out the Tampa Bay Times' list of America's 25 worst charities, as reported in a November 14, 2015, post on AlterNet by Daily Kos’s Leslie Salzillo. Some of the “charities” on the list pay 0 dollars directly to the cause they claim to be helping, despite having names such as the Kids Wish Network, Cancer Fund of America, and Project Cure. (Back in December 2013, I wrote about the Charity Navigator site that lets you vet organizations before you donate to them.)
Shopping for health plans? Go silver. ‘Tis also the season to shop for healthcare plans. Mother Jones’s Kevin Drum writes in a November 15, 2015, article that the lowest-cost Bronze plans are in fact no bargain at all because of their sky-high deductibles. Drum points out that for most people, the Silver plans are much better deals despite having slightly higher premiums because their deductibles are a fraction of their bronze counterparts.
Shopping for health plans? Go silver. ‘Tis also the season to shop for healthcare plans. Mother Jones’s Kevin Drum writes in a November 15, 2015, article that the lowest-cost Bronze plans are in fact no bargain at all because of their sky-high deductibles. Drum points out that for most people, the Silver plans are much better deals despite having slightly higher premiums because their deductibles are a fraction of their bronze counterparts.
November 11, 2015: Fair use stages a comeback

New protections against copyright abuse are in place following recent rulings that broaden the definition of fair use and move closer to accommodating new technologies.
November 4, 2015: Get ready for the attention economy

Maintaining your focus on what's most important doesn't get any easier. As the distractions multiply, the value of our attention increases.
October 27, 2015: O'Jitterys Catch a Movie

In honor of my birthday week, here's one of the many stories I tell myself. Just for kicks -- hope you get a laugh out of it!
Tech shorts for October 27, 2015: Empty ISP-Bandwidth Promises, Endangered Middle Managers, Robotic Elder-Care, And Speaking Emoji
Are you getting all the bandwidth you’re paying for?
U.S. ISPs aren’t delivering the network speed they promise their customers. According to the March 31, 2015, Ookla Net Index, the U.S. ranks 25th in the world in download speeds and 40th in upload speeds. Bruce Kushnick writes about the global speed tests in an article on the Huffington Post that was last updated on June 1, 2015.
Now the New York Attorney General is asking Time Warner, Verizon, and Cablevision to prove they are delivering to their customers the access speeds those customers are paying for. In an October 27, 2015, post, the Guardian reports the office is concerned about slow-downs in the last mile – the leg of the connection closest to the customer. It is also investigating complaints from consumers about slow connections to Netflix, Yahoo, and other high-traffic sites.
In a post from May 2, 2014, I explain how to find a reliable network speed test. Recently, my Internet connection speeds slowed to a fraction of the download and upload rates promised by AT&T, my current ISP. In fact, the only time the speeds reached those AT&T claimed it would offer was when I was on the phone to AT&T technical support – a call I’ve had to make far too often recently.
I was getting upload speeds you would expect from a dialup modem – remember those? After the support person updated the firmware in the AT&T-supplied router, the network speeds improved, for a while. I’ve been testing the connection multiple times a day since then, and they have never reached even half the speed AT&T says I should be getting.
(By the way, when I asked whether I could buy my own router to replace the one AT&T charges a $10-a-month rental fee for, I was told flat-out, “No.”)
Would switching to another ISP improve my network speeds? It’s a crapshoot. For the time being, I choose to stick with the devil I know. After all, I’ve got the support phone number memorized.
-------------------------------------------------------------------------
Next on big data’s hit list: Middle managers
All you managers out there who spend your workdays writing reports and attending meetings where the reports are discussed and dissected until some enterprising soul comes up with a long list of action items, beware! Big data analysis is looking to put you out of a job.
Forbes’ Theo Priestley writes in an October 15, 2015, article that advances in data analytics will allow algorithms to decide what actions need to be taken based and who should be taking those actions. So in place of the analysis-action-re-analysis-re-action four-step, business workers will be instructed by these very smart algorithms on what they need to do next. Boy, that sure sounds like fun! Where can I get me one of them jobs?
Priestley offers several examples of such algorithms being used to streamline help-desk requests, detect and prevent fraud in financial transactions, even analyze medical images. If you think you’re dealing with more machines than humans now, well, you ain’t seen nothin’ yet!
---------------------------------------------------------------------------
Taking humans out of the elder-care equation
Speaking of dehumanizing our world, leading tech firms are preparing to take over responsibility for the care and socializing of older folks. The Guardian’s Evgeny Morozov writes in an October 24, 2015, article that a robot named RoboCoach provides old people in Singapore with tips and instructions for staying active. The government’s goal is to reduce both healthcare costs and elder-care costs by closely monitoring people in their homes, while simultaneously keeping them entertained via joke-telling robots.
In Italy, IBM’s Secure Living program puts sensors in people’s homes to collect and analyze data about their activities – all of which the company can display on a “remote central control room,” according to Morozov. IBM and other companies offering these services admit that they are motivated by the need to reduce the cost of caring for old folks.
Morozov claims that the true beneficiary of these robot-care technologies are the corporations who offer them. Not only do they profit from the government contracts, they get to collect an incredible amount of personal information about their “customers.” And us old folks? Maybe we live longer. Maybe we’re even healthier. But we’re no longer cared for so much as we’re managed – sort of like cattle at the feedlot. Welcome to Solitary Confinement 2.0!
---------------------------------------------------------------------
Do you speak ‘Emoji’?
Email, messaging, and other Internet communications lack the context you can provide with the tone of your voice (irony) and visual cues (big, happy smile). Linguist Neil Cohn writes in an October 13, 2015, article on BBC that our hands communicate in a way that “transcends and clarifies the message in speech.” Cohn believes emojis fill the same role to enhance the text messages we send and receive.
Is emoji a new language? Cohn says no, primarily because it lacks the malleability that a new language requires as it forms. The language speakers have to be able to create new forms and vocabulary. With emojis, it is nearly impossible for users to create new ones. Also, there is no way for a grammar to develop. Without grammar, the elements of meaning can be grouped only in limited ways, and new meanings are difficult to convey.
According to Cohn, there is a slim chance “emoji” could evolve into a full-blown language, but the characters are more likely to remain bound to the text they accompany. If they help us communicate more clearly, and minimize miscommunications, there’s nothing at all wrong with that, even for us old-timers who are still trying to puzzle out how to make a smiley face.
U.S. ISPs aren’t delivering the network speed they promise their customers. According to the March 31, 2015, Ookla Net Index, the U.S. ranks 25th in the world in download speeds and 40th in upload speeds. Bruce Kushnick writes about the global speed tests in an article on the Huffington Post that was last updated on June 1, 2015.
Now the New York Attorney General is asking Time Warner, Verizon, and Cablevision to prove they are delivering to their customers the access speeds those customers are paying for. In an October 27, 2015, post, the Guardian reports the office is concerned about slow-downs in the last mile – the leg of the connection closest to the customer. It is also investigating complaints from consumers about slow connections to Netflix, Yahoo, and other high-traffic sites.
In a post from May 2, 2014, I explain how to find a reliable network speed test. Recently, my Internet connection speeds slowed to a fraction of the download and upload rates promised by AT&T, my current ISP. In fact, the only time the speeds reached those AT&T claimed it would offer was when I was on the phone to AT&T technical support – a call I’ve had to make far too often recently.
I was getting upload speeds you would expect from a dialup modem – remember those? After the support person updated the firmware in the AT&T-supplied router, the network speeds improved, for a while. I’ve been testing the connection multiple times a day since then, and they have never reached even half the speed AT&T says I should be getting.
(By the way, when I asked whether I could buy my own router to replace the one AT&T charges a $10-a-month rental fee for, I was told flat-out, “No.”)
Would switching to another ISP improve my network speeds? It’s a crapshoot. For the time being, I choose to stick with the devil I know. After all, I’ve got the support phone number memorized.
-------------------------------------------------------------------------
Next on big data’s hit list: Middle managers
All you managers out there who spend your workdays writing reports and attending meetings where the reports are discussed and dissected until some enterprising soul comes up with a long list of action items, beware! Big data analysis is looking to put you out of a job.
Forbes’ Theo Priestley writes in an October 15, 2015, article that advances in data analytics will allow algorithms to decide what actions need to be taken based and who should be taking those actions. So in place of the analysis-action-re-analysis-re-action four-step, business workers will be instructed by these very smart algorithms on what they need to do next. Boy, that sure sounds like fun! Where can I get me one of them jobs?
Priestley offers several examples of such algorithms being used to streamline help-desk requests, detect and prevent fraud in financial transactions, even analyze medical images. If you think you’re dealing with more machines than humans now, well, you ain’t seen nothin’ yet!
---------------------------------------------------------------------------
Taking humans out of the elder-care equation
Speaking of dehumanizing our world, leading tech firms are preparing to take over responsibility for the care and socializing of older folks. The Guardian’s Evgeny Morozov writes in an October 24, 2015, article that a robot named RoboCoach provides old people in Singapore with tips and instructions for staying active. The government’s goal is to reduce both healthcare costs and elder-care costs by closely monitoring people in their homes, while simultaneously keeping them entertained via joke-telling robots.
In Italy, IBM’s Secure Living program puts sensors in people’s homes to collect and analyze data about their activities – all of which the company can display on a “remote central control room,” according to Morozov. IBM and other companies offering these services admit that they are motivated by the need to reduce the cost of caring for old folks.
Morozov claims that the true beneficiary of these robot-care technologies are the corporations who offer them. Not only do they profit from the government contracts, they get to collect an incredible amount of personal information about their “customers.” And us old folks? Maybe we live longer. Maybe we’re even healthier. But we’re no longer cared for so much as we’re managed – sort of like cattle at the feedlot. Welcome to Solitary Confinement 2.0!
---------------------------------------------------------------------
Do you speak ‘Emoji’?
Email, messaging, and other Internet communications lack the context you can provide with the tone of your voice (irony) and visual cues (big, happy smile). Linguist Neil Cohn writes in an October 13, 2015, article on BBC that our hands communicate in a way that “transcends and clarifies the message in speech.” Cohn believes emojis fill the same role to enhance the text messages we send and receive.
Is emoji a new language? Cohn says no, primarily because it lacks the malleability that a new language requires as it forms. The language speakers have to be able to create new forms and vocabulary. With emojis, it is nearly impossible for users to create new ones. Also, there is no way for a grammar to develop. Without grammar, the elements of meaning can be grouped only in limited ways, and new meanings are difficult to convey.
According to Cohn, there is a slim chance “emoji” could evolve into a full-blown language, but the characters are more likely to remain bound to the text they accompany. If they help us communicate more clearly, and minimize miscommunications, there’s nothing at all wrong with that, even for us old-timers who are still trying to puzzle out how to make a smiley face.
October 20, 2015: Do we have a right to know what they know about us?
A lot of good can come from the collection and analysis of our personal information. We ask only that we be told what's being collected, and what's being done with it.
October 13, 2015: Facial recognition ushers in the age of surveillance

Soon machines will identify us more accurately than our own friends and family. There will be no escape from the prying eyes of government and corporations.
Tech short for October 13, 2015: The future of identification: Facial recognition + social media profile = authentication
Selfies are one of the most prominent phenomena of the burgeoning smart-phone era. Soon you may sign into your computer, your phone, your online accounts, and your favorite web services by snapping a picture of yourself. That shot will be tied to a social-media search to generate a score indicating how likely you are who the computer/system/application expects you to be.
In an October 11, 2015, post on TechCrunch, Jason Oxman, CEO of the Electronic Transactions Association, describes the Perceive “real-time facial biometrics product” developed by Socure, a vendor of identity-verification systems. Perceive matches a photo of your face with “media profile data” instantly. It is intended to replace passwords and to identify attempts to spoof the system with still photos by applying “liveliness checks.”
By combining the social-media search with its facial-recognition technology, Socure is able to authenticate people who don’t have online bank accounts and don’t perform other transactions online, but who do have a “healthy” social-media presence.
If they serve no other purpose, systems such as Perceive remind us of how public our social-media profiles have become, even when we’ve designated those profiles as “private.”
In an October 11, 2015, post on TechCrunch, Jason Oxman, CEO of the Electronic Transactions Association, describes the Perceive “real-time facial biometrics product” developed by Socure, a vendor of identity-verification systems. Perceive matches a photo of your face with “media profile data” instantly. It is intended to replace passwords and to identify attempts to spoof the system with still photos by applying “liveliness checks.”
By combining the social-media search with its facial-recognition technology, Socure is able to authenticate people who don’t have online bank accounts and don’t perform other transactions online, but who do have a “healthy” social-media presence.
If they serve no other purpose, systems such as Perceive remind us of how public our social-media profiles have become, even when we’ve designated those profiles as “private.”
Legal short for October 13, 2015: GOP mega-donor sues Mother Jones, loses, sort of
What just happened to Mother Jones magazine shouldn’t be allowed. Frank VanderSloot, who Salon’s Elias Isquith refers to as a “GOP mega-donor,” sued the magazine for defamation in 2012 following an article that referred to support for a Mitt Romney Super PAC by VanderSloot’s company. Isquith’s story is on an October 10, 2015, post on AlterNet.
Mother Jones spent $2.5 million in winning the case. That’s more of a penalty to the magazine than whatever the case cost billionaire VanderSloot, who can slough off the legal costs of his loss as chump change. Isquith points out that VanderSloot got litigious only after Mother Jones broke the “47 percent” story that hurt Romney’s chances for the White House.
VanderSloot’s suit was perfectly legal, but as Isquith writes, it could be construed as an attempt to “stifle speech by roping journalists into a war of attrition.” The real issue for Isquith is the impact of the Citizens United decision on political campaign financing. Supreme Court Justice Anthony Kennedy asserted in his decision that “independent expenditures do not lead to, or create the appearance of, quid pro quo corruption.” Isquith labels this “self-evidently absurd,” and he cites public opinion polls that support his conclusion.
Of course independent expenditures lead to, and create the appearance of, quid pro quo corruption. To think a Supreme Court justice would argue otherwise is indeed absurd. What if the court had ruled against Citizens United and struck down or curtailed the types of PAC contributions and operations at issue in the case? My bet is that the Republicans in Congress would’ve attempted to have the campaign-contribution limitations removed. Whether they would have succeeded is an open question. Lucky for them, Justice Kennedy did their dirty work for them.
Mother Jones spent $2.5 million in winning the case. That’s more of a penalty to the magazine than whatever the case cost billionaire VanderSloot, who can slough off the legal costs of his loss as chump change. Isquith points out that VanderSloot got litigious only after Mother Jones broke the “47 percent” story that hurt Romney’s chances for the White House.
VanderSloot’s suit was perfectly legal, but as Isquith writes, it could be construed as an attempt to “stifle speech by roping journalists into a war of attrition.” The real issue for Isquith is the impact of the Citizens United decision on political campaign financing. Supreme Court Justice Anthony Kennedy asserted in his decision that “independent expenditures do not lead to, or create the appearance of, quid pro quo corruption.” Isquith labels this “self-evidently absurd,” and he cites public opinion polls that support his conclusion.
Of course independent expenditures lead to, and create the appearance of, quid pro quo corruption. To think a Supreme Court justice would argue otherwise is indeed absurd. What if the court had ruled against Citizens United and struck down or curtailed the types of PAC contributions and operations at issue in the case? My bet is that the Republicans in Congress would’ve attempted to have the campaign-contribution limitations removed. Whether they would have succeeded is an open question. Lucky for them, Justice Kennedy did their dirty work for them.
October 6, 2015: Fantasy sports gambling finally gets scrutinized
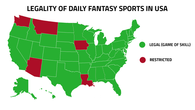
The legality of these popular betting sites is based on them being games of "skill," but many experts claim there's little if any skill involved in these games of chance.
Tech shorts for October 6, 2015: Beneficent 'malware,' a facial-recognition protest, and blocking ads for the greater good
A white-hat hacker ‘infects’ browsers to protect them
Normally when you discover a virus on one of your systems you rush to remove it and hope it hasn’t done any serious damage. But at least one hacker is releasing a virus designed to protect the Linux routers it “attacks.” Computerworld’s Peter Sayer reports in an October 2, 2015, article that a piece of malware called Linux.Wifatch has been tracked by Symantec security researchers since last January.
It turns out, the virus has been around since at least 2013, but no one knew what it was designed for – it didn’t appear to affect the systems on which it was found. Symantec claims that Linux.Wifatch is intended to keep other viruses from capitalizing on the same code defect that it used to install itself on the machine. Infected systems communicate via a peer-to-peer network to distribute updates about other malware threats, according to the researchers. The virus can also remove other malware it finds, and its code is in plain sight, which Symantec claims is an indication of the author’s good intentions.
---------------------------------------------------------------------------------
Artist creates masks to protest public facial recognition
Chicago is a surveillance lover’s paradise. The mayor is quoted in an ACLU report from 2012 (pdf) as predicting that there would be a video camera recording events on nearly every block of the city by 2016. Operation Virtual Field is a network of 24,000 cameras that can identify an individual based on their face and call up files associated with them automatically.
One of the problems with the current state of public facial recognition is the high level of false positives, as the Daily Dot’s Joseph Cox writes in a September 14, 2014, article. Leo Selvaggio, an artist who lives in Chicago, is attempting to counter the facial-recognition network in his city by creating and distributing masks that bear his likeness. Selvaggio’s URME Personal Surveillance Identity Prosthetic is close enough to the artist’s own facial features to fool the camera network, yet inconspicuous enough to be worn without the wearer calling attention to themselves, according to Selvaggio.
Facial scans are more dangerous from a privacy perspective than fingerprints, iris scans, and most other common forms of biometrics because your face can be scanned in public settings without your knowledge or consent. No, the artist doesn’t expect masks such as those he provides to become a standard component of modern wardrobes. He insists that the project’s goal is merely to raise awareness of the threats to privacy posed by new technologies such as facial recognition.
---------------------------------------------------------------------------------
Ad blocking as a political statement
Doc Searls is one of the sharpest minds in the technology biz. He has long been a proponent of Do Not Track and other privacy measures. In a September 25, 2015, post on his blog, Searls presents the sharp increase in the use of ad-blocking browser extensions and phone apps as a form of boycott. In fact, Searls calls it the “biggest boycott in human history.”
Searls points to two trends that spurred the increased adoption of ad blockers. In 2012, ad-supported commercial sites refused to honor Do Not Track. And from 2007 to 2011, adtech companies ramped up their retargeting efforts, which track us from site to site. That’s why you see the same ad on multiple sites as you browse.
Searls believes that we customers have to help marketers get past their attempts to gain our attention and trust through abuse and coercion. He states that ultimately, advertisers will realize that free customers beat captive ones; that genuine relationships beat those based on coercion; that volunteered, relevant personal data is worth more than that which is “involuntarily fracked”; and that customers’ expressions of real intent are worth more than intent inferred from this fracked data.
Normally when you discover a virus on one of your systems you rush to remove it and hope it hasn’t done any serious damage. But at least one hacker is releasing a virus designed to protect the Linux routers it “attacks.” Computerworld’s Peter Sayer reports in an October 2, 2015, article that a piece of malware called Linux.Wifatch has been tracked by Symantec security researchers since last January.
It turns out, the virus has been around since at least 2013, but no one knew what it was designed for – it didn’t appear to affect the systems on which it was found. Symantec claims that Linux.Wifatch is intended to keep other viruses from capitalizing on the same code defect that it used to install itself on the machine. Infected systems communicate via a peer-to-peer network to distribute updates about other malware threats, according to the researchers. The virus can also remove other malware it finds, and its code is in plain sight, which Symantec claims is an indication of the author’s good intentions.
---------------------------------------------------------------------------------
Artist creates masks to protest public facial recognition
Chicago is a surveillance lover’s paradise. The mayor is quoted in an ACLU report from 2012 (pdf) as predicting that there would be a video camera recording events on nearly every block of the city by 2016. Operation Virtual Field is a network of 24,000 cameras that can identify an individual based on their face and call up files associated with them automatically.
One of the problems with the current state of public facial recognition is the high level of false positives, as the Daily Dot’s Joseph Cox writes in a September 14, 2014, article. Leo Selvaggio, an artist who lives in Chicago, is attempting to counter the facial-recognition network in his city by creating and distributing masks that bear his likeness. Selvaggio’s URME Personal Surveillance Identity Prosthetic is close enough to the artist’s own facial features to fool the camera network, yet inconspicuous enough to be worn without the wearer calling attention to themselves, according to Selvaggio.
Facial scans are more dangerous from a privacy perspective than fingerprints, iris scans, and most other common forms of biometrics because your face can be scanned in public settings without your knowledge or consent. No, the artist doesn’t expect masks such as those he provides to become a standard component of modern wardrobes. He insists that the project’s goal is merely to raise awareness of the threats to privacy posed by new technologies such as facial recognition.
---------------------------------------------------------------------------------
Ad blocking as a political statement
Doc Searls is one of the sharpest minds in the technology biz. He has long been a proponent of Do Not Track and other privacy measures. In a September 25, 2015, post on his blog, Searls presents the sharp increase in the use of ad-blocking browser extensions and phone apps as a form of boycott. In fact, Searls calls it the “biggest boycott in human history.”
Searls points to two trends that spurred the increased adoption of ad blockers. In 2012, ad-supported commercial sites refused to honor Do Not Track. And from 2007 to 2011, adtech companies ramped up their retargeting efforts, which track us from site to site. That’s why you see the same ad on multiple sites as you browse.
Searls believes that we customers have to help marketers get past their attempts to gain our attention and trust through abuse and coercion. He states that ultimately, advertisers will realize that free customers beat captive ones; that genuine relationships beat those based on coercion; that volunteered, relevant personal data is worth more than that which is “involuntarily fracked”; and that customers’ expressions of real intent are worth more than intent inferred from this fracked data.
September 29, 2015: Google, Android, ads, and a tech titan's revenge

Steve Jobs' vendetta against Android -- which he called a "stolen product" -- could promote ad blocking, and ultimately lead to a change in how Web services make their money.
Legal shorts for September 29, 2015: Techies battle ISIS, and the social costs of unhealthy work environments
Techies join forces to combat ISIS propaganda
The immoral, unethical criminal gang that goes by “Islamic State” are the biggest bunch of hypocrites in the long, sordid history of hypocrites. They claim to want to return humanity to the Dark Ages – or even to bring about the end of human history entirely. Yet they rely on technology to spread their hateful, inhuman lies.
And they’re good at it, as Mark Mazzetti and Michael R. Gordon of the New York Times describe in a June 12, 2015, article. At the same time, the enemies of ISIS have not done a very good job of “counter-messaging” the effective recruitment disinformation being spread far and wide by the terrorist group.
Arizona State University’s CyberSocio Intelligent-Systems Laboratory, or CySIS, hopes to turn the tide in favor of the propaganda countermeasures. TechCrunch’s John Holden writes in a September 28, 2015, article that CySIS is developing tools that will identify and block online recruiting efforts by ISIS and other international criminal networks. CySIS hopes to point out the incongruities and contradictions in the Islamic State’s message.
CySIS will focus initially on Twitter use in such countries as Iraq, Syria, Nigeria, Indonesia, Malaysia, and the United Kingdom. The group’s approach differs from but complements efforts by hacktivists such as the group Anonymous to shut down their sites and communications channels. For example, Anonymous identifies Twitter feeds used by ISIS and other terrorists and then floods them with unrelated images in an attempt to prevent the feeds from appearing in search results.
Let’s hope that the truth will ultimately conquer their lies, just as love will ultimately conquer hate.
Now if we can just conquer over our unhealthy office work environments
I’m not the only person in the world who hates working in an office, but I am among the few (but growing) number of people who believe office work environments are a hazard to our physical and mental health, not to mention our careers.
Work-related stress has reached epidemic proportions, according to the experts cited by Anne-Marie Slaughter in a September 18, 2015, article in the New York Times Sunday Review. (I know – September 18 was a Friday, not a Sunday, but hey, it’s the New York Times.) It has gotten to the point where the only people able to thrive in the modern work environment are healthy young people who are rich enough not to have to care for children or other family members.
Employers don’t make room for care-giving, according to Slaughter. This causes women in particular to be forced out of the work world, or to be limited to entry and mid-level positions because they can’t make the time commitment required by senior-management jobs. That’s a lot of talent that never gets realized.
Slaughter states that the people who decide how we work are still living in the 1960s world glorified by the television show “Mad Men.” Researchers she cites claim the problem isn’t limited to women, though they appear to be affected by it to a greater extent than men. The real source of the stress epidemic is the culture of overwork. And there’s no way that culture will change from the inside because some companies will always choose profit over the health and well-being of their employees – and some employees will always choose to take the money and live with the negative consequences for them and their families.
According to Slaughter, the only cure for the stress epidemic is to change our culture so that care-giving is valued as it should be. She says we need to “stand up for care,” and for men and women alike to “claim an equal right to care.”
Sorry, but I just don’t see the boards and executives that run the large corporations that currently rule the world as having a “care” in the world about the need for their employees to care for their families. There’s just no profit in it, and as we all know, for them, profit is all that matters.
The immoral, unethical criminal gang that goes by “Islamic State” are the biggest bunch of hypocrites in the long, sordid history of hypocrites. They claim to want to return humanity to the Dark Ages – or even to bring about the end of human history entirely. Yet they rely on technology to spread their hateful, inhuman lies.
And they’re good at it, as Mark Mazzetti and Michael R. Gordon of the New York Times describe in a June 12, 2015, article. At the same time, the enemies of ISIS have not done a very good job of “counter-messaging” the effective recruitment disinformation being spread far and wide by the terrorist group.
Arizona State University’s CyberSocio Intelligent-Systems Laboratory, or CySIS, hopes to turn the tide in favor of the propaganda countermeasures. TechCrunch’s John Holden writes in a September 28, 2015, article that CySIS is developing tools that will identify and block online recruiting efforts by ISIS and other international criminal networks. CySIS hopes to point out the incongruities and contradictions in the Islamic State’s message.
CySIS will focus initially on Twitter use in such countries as Iraq, Syria, Nigeria, Indonesia, Malaysia, and the United Kingdom. The group’s approach differs from but complements efforts by hacktivists such as the group Anonymous to shut down their sites and communications channels. For example, Anonymous identifies Twitter feeds used by ISIS and other terrorists and then floods them with unrelated images in an attempt to prevent the feeds from appearing in search results.
Let’s hope that the truth will ultimately conquer their lies, just as love will ultimately conquer hate.
Now if we can just conquer over our unhealthy office work environments
I’m not the only person in the world who hates working in an office, but I am among the few (but growing) number of people who believe office work environments are a hazard to our physical and mental health, not to mention our careers.
Work-related stress has reached epidemic proportions, according to the experts cited by Anne-Marie Slaughter in a September 18, 2015, article in the New York Times Sunday Review. (I know – September 18 was a Friday, not a Sunday, but hey, it’s the New York Times.) It has gotten to the point where the only people able to thrive in the modern work environment are healthy young people who are rich enough not to have to care for children or other family members.
Employers don’t make room for care-giving, according to Slaughter. This causes women in particular to be forced out of the work world, or to be limited to entry and mid-level positions because they can’t make the time commitment required by senior-management jobs. That’s a lot of talent that never gets realized.
Slaughter states that the people who decide how we work are still living in the 1960s world glorified by the television show “Mad Men.” Researchers she cites claim the problem isn’t limited to women, though they appear to be affected by it to a greater extent than men. The real source of the stress epidemic is the culture of overwork. And there’s no way that culture will change from the inside because some companies will always choose profit over the health and well-being of their employees – and some employees will always choose to take the money and live with the negative consequences for them and their families.
According to Slaughter, the only cure for the stress epidemic is to change our culture so that care-giving is valued as it should be. She says we need to “stand up for care,” and for men and women alike to “claim an equal right to care.”
Sorry, but I just don’t see the boards and executives that run the large corporations that currently rule the world as having a “care” in the world about the need for their employees to care for their families. There’s just no profit in it, and as we all know, for them, profit is all that matters.
September 23, 2015: Fix problems caused by Apple's flaky iTunes updates

Undo the damage caused by patches gone awry -- and useful features gone missing.
Tech shorts for September 23, 2015: Internet freedom imperiled, targeted ads ineffective, and selfie safety
Centralized control is destroying the ‘free’ Internet
In 1993, computer scientist and Internet activist John Gilmore said, “The Net interprets censorship as damage and routes around it.”
Not anymore. Over the past 20 years, the Internet has done a 180 – evolving from a decentralized system that no single entity could control, to a centralized one in the hands of a few governments and large corporations (Google, Facebook, Amazon, and a handful of others). The result is the death of freedom on the Internet, according to Jennifer Granick, Director of Civil Liberties at the Stanford Center for Internet and Society.
In an August 5, 2015, article, TechCrunch’s Jon Evans reports on Granick’s keynote address at the recent Black Hat security conference. According to Granick, the act of patching software to maintain security creates a central authority and a single “choke point.”
Granick adds that “[p]eople want to use convenient, secure, and widely available online services… but this centralizes control even further.” These services are able to enforce their own “moral standards,” such as banning photographs of breast-feeding mothers.
These problems pale in comparison to what Granick identifies as the real culprit imperiling Internet freedom: secret law, which she calls “an abomination in the face of democracy.” In essence, the Internet has evolved from an open system that values freedom and privacy to a closed system predicated on security and surveillance. Granick’s solution? “[S]mash it apart and make something new and better.”
Okay, but who owns all the sledgehammers?
--------------------------------------------------------------------------------------
Why targeted advertising is doomed
It seemed like a good idea at the time: Show people coming to web sites ads that are tailored to their interests, based on information you collect about their Internet activities. If you spend a lot of time reading about patio furniture, maybe you’re looking to buy some, so serve up ads for Adirondack chairs and umbrella tables.
There’s only two problems with these targeted ads:
In a dissertation-length article, Don Marti of zgp.org explains that the true value of advertising is to present the vendor and its products as trustworthy. In essence, the advertiser is saying, “I believe this product is going to sell so well I’m willing to spend all this money on advertising in the belief that I’ll recoup it all, and more on top of that as profit.”
That’s why print advertising is perceived as more effective than online ads despite people spending far less time viewing print ads. A polished, flashy ad in New Yorker magazine tells potential buyers that this is a classy product for classy people. It’s not so much the content of the ad itself as it is the context of the ad.
Marti encourages online advertisers to embrace Do Not Track technologies and turn their energies and ad budgets toward applying technology to catch customers’ attention and communicate a context that gives their products prestige. Consumers will respond better to generic ads they see at the right time and in the right place. An ad that is obviously targeted specifically at them just gives them the creeps.
In the meantime, Marti recommends that consumers block third-party cookies in their browsers and apply other anti-tracking methods. (In the September 8, 2015, Weekly, I described how to block third-party cookies in Internet Explorer, Firefox, and Google Chrome.)
--------------------------------------------------------------------
Caution: Selfies can be hazardous to your health
A Japanese tourist taking a selfie at the Taj Mahal falls down the steps and dies. A teenager in Romania is taking a selfie on top of a railroad car, touches a high-voltage wire, and is electrocuted. Two Russians are taking a selfie with a hand grenade, and guess what happens? Yep, kaboom! Hand grenade 2, Russian selfie-takers, 0.
According to the Huffington Post’s Hilary Hanson in a September 23, 2015, article, you’re more likely to kill yourself while taking a selfie than you are to be killed in an unprovoked shark attack. Aside from questions about what constitutes an “unprovoked” shark attack, the comparison rests on some shaky statistical grounds. In fact, the experts claim that selfie-induced deaths are under-reported. A Russian government official is quoted as saying there have been dozens of selfie-related deaths in that country alone.
A good friend of mine had the perfect solution to problems related to vacation photography: Leave the camera at home and buy postcards. Okay, so not many people are likely to follow his example, but the next time you strike a pose, consider letting someone else work the shutter.
In 1993, computer scientist and Internet activist John Gilmore said, “The Net interprets censorship as damage and routes around it.”
Not anymore. Over the past 20 years, the Internet has done a 180 – evolving from a decentralized system that no single entity could control, to a centralized one in the hands of a few governments and large corporations (Google, Facebook, Amazon, and a handful of others). The result is the death of freedom on the Internet, according to Jennifer Granick, Director of Civil Liberties at the Stanford Center for Internet and Society.
In an August 5, 2015, article, TechCrunch’s Jon Evans reports on Granick’s keynote address at the recent Black Hat security conference. According to Granick, the act of patching software to maintain security creates a central authority and a single “choke point.”
Granick adds that “[p]eople want to use convenient, secure, and widely available online services… but this centralizes control even further.” These services are able to enforce their own “moral standards,” such as banning photographs of breast-feeding mothers.
These problems pale in comparison to what Granick identifies as the real culprit imperiling Internet freedom: secret law, which she calls “an abomination in the face of democracy.” In essence, the Internet has evolved from an open system that values freedom and privacy to a closed system predicated on security and surveillance. Granick’s solution? “[S]mash it apart and make something new and better.”
Okay, but who owns all the sledgehammers?
--------------------------------------------------------------------------------------
Why targeted advertising is doomed
It seemed like a good idea at the time: Show people coming to web sites ads that are tailored to their interests, based on information you collect about their Internet activities. If you spend a lot of time reading about patio furniture, maybe you’re looking to buy some, so serve up ads for Adirondack chairs and umbrella tables.
There’s only two problems with these targeted ads:
- People hate them.
- They don’t work.
In a dissertation-length article, Don Marti of zgp.org explains that the true value of advertising is to present the vendor and its products as trustworthy. In essence, the advertiser is saying, “I believe this product is going to sell so well I’m willing to spend all this money on advertising in the belief that I’ll recoup it all, and more on top of that as profit.”
That’s why print advertising is perceived as more effective than online ads despite people spending far less time viewing print ads. A polished, flashy ad in New Yorker magazine tells potential buyers that this is a classy product for classy people. It’s not so much the content of the ad itself as it is the context of the ad.
Marti encourages online advertisers to embrace Do Not Track technologies and turn their energies and ad budgets toward applying technology to catch customers’ attention and communicate a context that gives their products prestige. Consumers will respond better to generic ads they see at the right time and in the right place. An ad that is obviously targeted specifically at them just gives them the creeps.
In the meantime, Marti recommends that consumers block third-party cookies in their browsers and apply other anti-tracking methods. (In the September 8, 2015, Weekly, I described how to block third-party cookies in Internet Explorer, Firefox, and Google Chrome.)
--------------------------------------------------------------------
Caution: Selfies can be hazardous to your health
A Japanese tourist taking a selfie at the Taj Mahal falls down the steps and dies. A teenager in Romania is taking a selfie on top of a railroad car, touches a high-voltage wire, and is electrocuted. Two Russians are taking a selfie with a hand grenade, and guess what happens? Yep, kaboom! Hand grenade 2, Russian selfie-takers, 0.
According to the Huffington Post’s Hilary Hanson in a September 23, 2015, article, you’re more likely to kill yourself while taking a selfie than you are to be killed in an unprovoked shark attack. Aside from questions about what constitutes an “unprovoked” shark attack, the comparison rests on some shaky statistical grounds. In fact, the experts claim that selfie-induced deaths are under-reported. A Russian government official is quoted as saying there have been dozens of selfie-related deaths in that country alone.
A good friend of mine had the perfect solution to problems related to vacation photography: Leave the camera at home and buy postcards. Okay, so not many people are likely to follow his example, but the next time you strike a pose, consider letting someone else work the shutter.
September 15, 2015: Campaign 2016 -- Where's the love?

Voters want authenticity, compassion, and integrity in their leaders, and only one candidate is offering it. (No, not that guy on the left -- which may be the first time he's been on the left of anything short of the John Birch Society.)
Tech shorts for September 15, 2015: A Programming Book for Kids, and ad blocking catches on

New book helps students learn how to program
Back in the 1960s, my father recommended that I take a typing class. At the time, I thought that was an odd suggestion, but I took my father's advice and have been glad I did ever since.
Not everyone will make their living by developing or maintaining software. However, just as knowing how to touch type benefits people in many diverse walks of life, having a bit of programming experience will help many different categories of workers thrive in the future.
Danny Takeuchi, a senior at Centennial High School in Boise, Idaho, has written Animation for Kids with Scratch Programming — Digital Art, Story Telling and Coding, which is intended to be easy enough for a nine-year-old to use. Clark Corbin describes Takeuchi's unique approach to programming instruction in a September 10, 2015, article on the IdahoEdNews.org site.
Rather than focusing on tech terms and the standard STEM approach to programming instruction, Takeuchi emphasizes story telling and art, two concepts that youngsters are already familiar with. Watching my seven-year-old grandson blast through Minecraft makes me think that Scratch programming could be right up his virtual alley. And Takeuchi's instructional guide could be just the thing to help prepare him for whatever career he chooses.
-----------------------------------------------------------------------------
Online advertisers feel the heat from increased use of ad blockers
Some website owners claim that blocking ads is tantamount to stealing. Yet use of ad-blocking browser extensions continues to increase, particularly among gamers and other tech-savvy people who are among the eyeballs most coveted by advertisers.
In a September 11, 2015, article, TechCrunch's Anthony Ha explains the quandary facing website owners, who are seeing their ad-based revenue decline by as much as 20 percent as a result of ad blocking. The advertisers admit that online ads are out of control: They block content and otherwise hinder our ability to view sites unimpeded by obnoxious animations and pop-ups.
As I wrote in a post from April 7, 2015, the real problem with web ads isn't that they're annoying or that they threaten our privacy. It's that they have become a favorite medium for Internet crooks to deliver their malware payloads. Ha points out that there was never a time when people who use the Internet opted in to viewing ads -- they arrived after the fact.
Online advertisers have devised ways to get their ads past the blockers, and sites have begun to block content until visitors who are using an ad-blocking extension disable the program. Rather than getting into a spy-vs.-spy battle with their ad-blocking visitors, site owners would be better off working with their customers on "acceptable ads" such as those proposed by the makers of the popular AdBlock Plus extension.
The best solution would be to offer micropayment subscriptions to people who prefer to pay up front for web content minus the ads, and to serve up ad-laden versions of their pages for the folks who eschew the subscription model. As a rough estimate, would you be willing to pay a half-penny for each page you viewed for more than two or three seconds? I can spend all day working on the web and not open more than 100 pages total. That's about 50 cents a day, or $15 a month for an ad-free web experience.
(In fact, the half-penny-per-page figure is probably more than site owners generate from each page view at present. The actual figure is probably closer to one-fifth of a penny per page view. This would reduce the ad-free fee to about 20 cents a day, or $6 a month.)
So keep blocking those ads, and if you start to feel sorry for the revenue you're costing the sites you frequent, remember that they're the ones who made this mess, and they're the only ones who can clean it up.
Legal shorts for September 15, 2015: Web giants as privacy protectors, and facebook's underage problem
Could tech giants be our best hope against government overreaching?
Imagine trusting our privacy to Facebook, Google, and Apple. All three companies have less-than-stellar records for protecting the privacy of their customers, yet they continue to serve as our last line of defense against attempts by government agencies to access our private information without a proper warrant.
TruthDig's Thor Benson writes in a September 11, 2015, article that ordinary citizens are in no position to protect their private information stored with web services from overreaching government agencies. Benson cites a recent paper by University of Washington School of Law assistant professor Ryan Calo, who believes that web services are the only parties able to "resist excessive data requests." The companies are also the only ones with the legal firepower to battle the government. (A shorter version of Calo's paper is published on Fusion.)
Although Google has been awarded only three out of five stars on the Electronic Frontier Foundation's "Who has your back?" chart, the company is credited with following privacy best practices, publishing all government data requests it receives, and opposing built-in backdoors to thwart encryption. (Apple is noteworthy for its strong, steady objection to encryption backdoors.)
When the government comes looking for our private data, we have no choice but to trust the web services we frequent. As the EFF's Nate Cardozo points out in Benson's article, privacy is a prerequisite for democracy, and encryption is now a prerequisite for privacy. That's why we have no choice but to encrypt the entire Internet, even though encryption is anything but a privacy panacea. (I explain why in an April 14, 2015, article, "Should all web traffic be encrypted?", and in another article two weeks later entitled "The case against web encryption, Title II designation for ISPs.")
---------------------------------------------------------------------
Facebook has an underage problem
Not everyone realizes Facebook has an age limit: You have to be at least 13 years old to create a Facebook account. According to the International Business Times' Zairah Khurshid in a September 13, 2015, article, the age limit is the result of U.S. laws protecting the privacy of children.
Now the company is being sued by a British man who claims his daughter was subjected to sexual predators on a Facebook account she created when she was only 11 years old. The man's lawyers state that the company's registration system is too lax, which exposes children to "extreme material."
At present, a child can merely indicate that they are at least 13 years old when they register with Facebook. The company is quoted by Khurshid as removing as many as 20,000 accounts created by underage children each day. A pre-trial agreement reportedly calls for Facebook to pay the family some compensation. Should such suits proliferate, Facebook and many other sites may be required to implement a more-stringent age-verification system.
Maybe that's not such a bad idea.
Imagine trusting our privacy to Facebook, Google, and Apple. All three companies have less-than-stellar records for protecting the privacy of their customers, yet they continue to serve as our last line of defense against attempts by government agencies to access our private information without a proper warrant.
TruthDig's Thor Benson writes in a September 11, 2015, article that ordinary citizens are in no position to protect their private information stored with web services from overreaching government agencies. Benson cites a recent paper by University of Washington School of Law assistant professor Ryan Calo, who believes that web services are the only parties able to "resist excessive data requests." The companies are also the only ones with the legal firepower to battle the government. (A shorter version of Calo's paper is published on Fusion.)
Although Google has been awarded only three out of five stars on the Electronic Frontier Foundation's "Who has your back?" chart, the company is credited with following privacy best practices, publishing all government data requests it receives, and opposing built-in backdoors to thwart encryption. (Apple is noteworthy for its strong, steady objection to encryption backdoors.)
When the government comes looking for our private data, we have no choice but to trust the web services we frequent. As the EFF's Nate Cardozo points out in Benson's article, privacy is a prerequisite for democracy, and encryption is now a prerequisite for privacy. That's why we have no choice but to encrypt the entire Internet, even though encryption is anything but a privacy panacea. (I explain why in an April 14, 2015, article, "Should all web traffic be encrypted?", and in another article two weeks later entitled "The case against web encryption, Title II designation for ISPs.")
---------------------------------------------------------------------
Facebook has an underage problem
Not everyone realizes Facebook has an age limit: You have to be at least 13 years old to create a Facebook account. According to the International Business Times' Zairah Khurshid in a September 13, 2015, article, the age limit is the result of U.S. laws protecting the privacy of children.
Now the company is being sued by a British man who claims his daughter was subjected to sexual predators on a Facebook account she created when she was only 11 years old. The man's lawyers state that the company's registration system is too lax, which exposes children to "extreme material."
At present, a child can merely indicate that they are at least 13 years old when they register with Facebook. The company is quoted by Khurshid as removing as many as 20,000 accounts created by underage children each day. A pre-trial agreement reportedly calls for Facebook to pay the family some compensation. Should such suits proliferate, Facebook and many other sites may be required to implement a more-stringent age-verification system.
Maybe that's not such a bad idea.
September 8, 2015: Three simple ways to improve your privacy

Check your public Facebook profile, block third-party cookies/clear your browser history, and lock down your connection on public WiFi and elsewhere.
September 1, 2015: Use your free Google Voice number to make and receive phone calls
It's not one of the company's more popular services, but Google Voice is one of its most effective aggravation relievers.
August 25, 2015: Reclaiming government starts with universal Internet access

Open government requires transparency, participation, and collaboration, all of which rely on an informed citizenry.
August 4, 2015: Upon further review, times three

Taking a second look at cyberwar threats, race in America, and the right to be forgotten -- at least by Google.
Shorts for August 4, 2015: A Gmail track-buster, tracking you by your mouse movements, a Windows 10 mandatory-update reversal, and Jimmy Carter calls for oligarchy busting
Fifty percent of our emails are tracked, according to Forbes' Kate Vinton in a July 28, 2015, article. A new company called Trackbuster has developed a service that promises to remove the tracking code from Gmail messages; other email systems will be supported in the future.
The trackers can also ID you based on your mousing, among other characteristics, such as how you type and even your computer's battery level. That's according to Forbes' Thomas Fox-Brewster writing in a July 29, 2015, article. Now that more people are blocking ads and third-party cookies, the trackers need new ways to spy on us. There's no indication that such tracking technologies are being used at present, but as Fox-Brewster indicates, it's only a matter of time. (Tools for blocking these types of trackers are already being developed.)
Microsoft appears to be back-tracking on mandatory Windows 10 updates, according to Forbes' Antony Leather in a July 27, 2015, article (it's a Forbes trifecta!) Leather describes the process required to block updates in Windows 10, which prevents the patches from interfering with various applications and device drivers. Several early adopters of Windows 10 reported problems following some updates, which is what motivated Microsoft to make the change in policy, according to Leather.
According to Jimmy Carter, our nation has seen "a complete subversion of our political system as a payoff to major contributors, who want and expect and sometimes get favors for themselves after the election’s over." The solution President Carter proposes? As quoted in an August 1, 2015, article by Thom Hartmann of AlterNet, Carter claims only a "horrible, disgraceful" corruption scandal will turn the public against the U.S. Supreme Court's Citizens United decision that made the oligarchy possible. Presidential candidate Sen. Bernie Sanders has introduced a constitutional amendment that would overturn Citizens United and state unequivocally that corporations are not people and thus do not have the same rights as people. Go, Bernie! Go, Bernie! Go, Bernie!
The trackers can also ID you based on your mousing, among other characteristics, such as how you type and even your computer's battery level. That's according to Forbes' Thomas Fox-Brewster writing in a July 29, 2015, article. Now that more people are blocking ads and third-party cookies, the trackers need new ways to spy on us. There's no indication that such tracking technologies are being used at present, but as Fox-Brewster indicates, it's only a matter of time. (Tools for blocking these types of trackers are already being developed.)
Microsoft appears to be back-tracking on mandatory Windows 10 updates, according to Forbes' Antony Leather in a July 27, 2015, article (it's a Forbes trifecta!) Leather describes the process required to block updates in Windows 10, which prevents the patches from interfering with various applications and device drivers. Several early adopters of Windows 10 reported problems following some updates, which is what motivated Microsoft to make the change in policy, according to Leather.
According to Jimmy Carter, our nation has seen "a complete subversion of our political system as a payoff to major contributors, who want and expect and sometimes get favors for themselves after the election’s over." The solution President Carter proposes? As quoted in an August 1, 2015, article by Thom Hartmann of AlterNet, Carter claims only a "horrible, disgraceful" corruption scandal will turn the public against the U.S. Supreme Court's Citizens United decision that made the oligarchy possible. Presidential candidate Sen. Bernie Sanders has introduced a constitutional amendment that would overturn Citizens United and state unequivocally that corporations are not people and thus do not have the same rights as people. Go, Bernie! Go, Bernie! Go, Bernie!
July 28, 2015: Coming soon -- A more trustworthy form of encryption

MIT researchers are working on a system that allows encrypted data to be processed without disclosing the contents to unauthorized sources.
Tech shorts for July 28, 2015: Misuse of 23andMe's DNA database, delete emails after you send them, and online ad networks take more liberties
23andMe's DNA data used to restrict site access based on ancestry
If you signed up for genetic analysis by the 23andMe service and allowed your DNA data to be added to the service's public database, you may be in for a surprise. Fast Company's Pavithra Mohan reports in a July 23, 2015, article that a program called Genetic Access Control uses the 23andMe open API to allow web sites to identify and block visitors based on their "race, sex, and ancestry."
The program was posted briefly on GitHub, but 23andMe quickly blocked the app's access to its DNA database. The company claims only three people used the program before it was blocked. 23andMe's API policy prohibits any use that creates "hate materials or materials urging acts of terrorism or violence."
The good news is that 23andMe discovered and addressed the misuse promptly. The company's policy is to restrict access to the data while apps using it are being developed, and then approving full access only after the program has been reviewed by its staff.
The bad news is that our genetic information is more likely to be collected and shared in the future whether we consent to it or even know about it.
The bottom line is that 23andMe's customers must opt into making their DNA data part of the public database. The potential benefits of a DNA database are tremendous, but so are the risks to privacy. Until we can be assured our most personal of data is safe from misuse by third parties, it's a good idea to prevent it from being shared -- at least to the extent that we're able to control ourselves.
----------------------------------------------
Now you can delete emails after you send them
Email regret can be a terrible thing. There are ways to delay the emails you send to give yourself a chance to recall them before they're delivered, as I described for Outlook in a CNET post from 2008. There are also products that offer to review your messages before you send them to spot potential incendiary comments; the old Eudora program used one, two, or three hot-pepper icons to indicate the mail's emotional tone.
A new product called Dmail claims to let you delete a Gmail message after you've sent it, and ultimately to prevent an email from being forwarded. TechCrunch's Sarah Perez describes the product in a July 23, 2015, article. Dmail is being developed by the same people who created the Delicious social-bookmarking service.
The product differs from Gmail's own delayed-delivery option, which displays an "Undo Send" button for up to 30 seconds after you hit the Send button. By contrast, Dmail claims to allow any sent message to be deleted at any time. It works as an extension for Google's Chrome browser and adds a new option to the Gmail compose window. You can specify that you want the message deleted after an hour, a day, a week, or "never." Even if you chose the "never" option you can still access via your sent-messages folder and select the "Revoke Email" button.
Message recipients who don't have the Dmail extension installed are prompted to click a link to view the "secure message" on a web page. If the recipient has the extension, the message is displayed in Gmail. Once the message has been revoked, these recipients will be told "the message has been destroyed and is no longer available" whenever they attempt to access it.
The program's developers intend to add the ability to control access to PDFs and other files in addition to email. The current version of the product is available for free on the Google Chrome store.
------------------------------------------------
Online advertisers continue to be their own worst enemies
One of the Shorts from July 14, 2015, explained how a Canadian university reduced its total network bandwidth needs by 40 percent simply by blocking ads. These days, we're more likely to be viewing web content on our mobile devices, which often are subject to data-transfer caps. If your mobile plan limits you to 100MB of data traffic each month, for example, you could avoid extra charges simply by installing an ad-blocking extension on your phone or tablet.
Saving bandwidth charges is only one of the benefits of blocking ads. Abderrezak Kamel, chief technology officer at the tech news site Technorati, writes in a July 22, 2015, guest post on the AdExchanger site that online ad networks are abusing their access to the personal information they collect through our browsers. Kamel asserts that advertisers are capitalizing on the data without compensating publishers, and also degrading the user experience by adding so much overhead via their sophisticated and abundant data-collecting pixels.
Kamel calls for creation of a user-ID standard that browser makers could implement to manage the ad networks' data-collection activities. The standards would be enforced by "a governing body that everybody trusts," according to Kamel.
As commenters to the article point out, the main problem with such a standard is that the parties charged with implementing and enforcing it are the same parties that have profited so much from the current online-ad system: Google makes Chrome, Microsoft makes Internet Explorer, Apple makes Safari, and Mozilla sells ads on its home page.
The only way to rein in the out-of-control online ad networks is by promoting the use of ad-blocking browser extensions such as AdBlock Plus as a way to coerce the advertisers into respecting publishers and web users alike.
If you signed up for genetic analysis by the 23andMe service and allowed your DNA data to be added to the service's public database, you may be in for a surprise. Fast Company's Pavithra Mohan reports in a July 23, 2015, article that a program called Genetic Access Control uses the 23andMe open API to allow web sites to identify and block visitors based on their "race, sex, and ancestry."
The program was posted briefly on GitHub, but 23andMe quickly blocked the app's access to its DNA database. The company claims only three people used the program before it was blocked. 23andMe's API policy prohibits any use that creates "hate materials or materials urging acts of terrorism or violence."
The good news is that 23andMe discovered and addressed the misuse promptly. The company's policy is to restrict access to the data while apps using it are being developed, and then approving full access only after the program has been reviewed by its staff.
The bad news is that our genetic information is more likely to be collected and shared in the future whether we consent to it or even know about it.
The bottom line is that 23andMe's customers must opt into making their DNA data part of the public database. The potential benefits of a DNA database are tremendous, but so are the risks to privacy. Until we can be assured our most personal of data is safe from misuse by third parties, it's a good idea to prevent it from being shared -- at least to the extent that we're able to control ourselves.
----------------------------------------------
Now you can delete emails after you send them
Email regret can be a terrible thing. There are ways to delay the emails you send to give yourself a chance to recall them before they're delivered, as I described for Outlook in a CNET post from 2008. There are also products that offer to review your messages before you send them to spot potential incendiary comments; the old Eudora program used one, two, or three hot-pepper icons to indicate the mail's emotional tone.
A new product called Dmail claims to let you delete a Gmail message after you've sent it, and ultimately to prevent an email from being forwarded. TechCrunch's Sarah Perez describes the product in a July 23, 2015, article. Dmail is being developed by the same people who created the Delicious social-bookmarking service.
The product differs from Gmail's own delayed-delivery option, which displays an "Undo Send" button for up to 30 seconds after you hit the Send button. By contrast, Dmail claims to allow any sent message to be deleted at any time. It works as an extension for Google's Chrome browser and adds a new option to the Gmail compose window. You can specify that you want the message deleted after an hour, a day, a week, or "never." Even if you chose the "never" option you can still access via your sent-messages folder and select the "Revoke Email" button.
Message recipients who don't have the Dmail extension installed are prompted to click a link to view the "secure message" on a web page. If the recipient has the extension, the message is displayed in Gmail. Once the message has been revoked, these recipients will be told "the message has been destroyed and is no longer available" whenever they attempt to access it.
The program's developers intend to add the ability to control access to PDFs and other files in addition to email. The current version of the product is available for free on the Google Chrome store.
------------------------------------------------
Online advertisers continue to be their own worst enemies
One of the Shorts from July 14, 2015, explained how a Canadian university reduced its total network bandwidth needs by 40 percent simply by blocking ads. These days, we're more likely to be viewing web content on our mobile devices, which often are subject to data-transfer caps. If your mobile plan limits you to 100MB of data traffic each month, for example, you could avoid extra charges simply by installing an ad-blocking extension on your phone or tablet.
Saving bandwidth charges is only one of the benefits of blocking ads. Abderrezak Kamel, chief technology officer at the tech news site Technorati, writes in a July 22, 2015, guest post on the AdExchanger site that online ad networks are abusing their access to the personal information they collect through our browsers. Kamel asserts that advertisers are capitalizing on the data without compensating publishers, and also degrading the user experience by adding so much overhead via their sophisticated and abundant data-collecting pixels.
Kamel calls for creation of a user-ID standard that browser makers could implement to manage the ad networks' data-collection activities. The standards would be enforced by "a governing body that everybody trusts," according to Kamel.
As commenters to the article point out, the main problem with such a standard is that the parties charged with implementing and enforcing it are the same parties that have profited so much from the current online-ad system: Google makes Chrome, Microsoft makes Internet Explorer, Apple makes Safari, and Mozilla sells ads on its home page.
The only way to rein in the out-of-control online ad networks is by promoting the use of ad-blocking browser extensions such as AdBlock Plus as a way to coerce the advertisers into respecting publishers and web users alike.
July 21, 2015: Protect yourself while browsing by enabling click to play
Prevent Flash-based malware from infecting your machine by blocking Flash videos until you've explicitly approved them.
Tech short for July 21, 2015: Computers tie emotions to facial expressions
Imagine turning on your computer to start your workday only to have the machine ask whether you would like to talk to somebody about how you're feeling. A new company called Affectiva has developed a technology that the company claims can read and interpret your facial expressions. Brendan Marr writes about Affectiva's technology in a July 7, 2015, article on DataInformed.
Affectiva's software has been used to test the response to television ads or TV pilots, and to help children with Asperger Syndrome recognize emotions in facial expressions. Two areas the company is targeting are monitoring students as they progress through an assignment to determine when they've encountered some difficulties; and identifying when people are feeling depressed.
So what happens when our emotions are tied to our identities, or our emotional events are recorded for posterity? Psychologist Paul Ekman, on whose work much of the technology is based, writes in a post from May 2014 that not only will our emotions be recorded and used to manipulate our behavior, unscrupulous parties could apply the technology as a form of lie detector -- or even mind reader.
I can see it now: The Republicans introduce legislation outlawing the wearing of masks in public -- all in the name of national security. Can you say "poker face"?
Affectiva's software has been used to test the response to television ads or TV pilots, and to help children with Asperger Syndrome recognize emotions in facial expressions. Two areas the company is targeting are monitoring students as they progress through an assignment to determine when they've encountered some difficulties; and identifying when people are feeling depressed.
So what happens when our emotions are tied to our identities, or our emotional events are recorded for posterity? Psychologist Paul Ekman, on whose work much of the technology is based, writes in a post from May 2014 that not only will our emotions be recorded and used to manipulate our behavior, unscrupulous parties could apply the technology as a form of lie detector -- or even mind reader.
I can see it now: The Republicans introduce legislation outlawing the wearing of masks in public -- all in the name of national security. Can you say "poker face"?
July 14, 2015: The connection between poverty, hunger, and obesity
There's a physiological reason why hungry people crave sugary and fatty foods. Can we pay for free, healthy food by taxing the unhealthy stuff?
Shorts for July 14, 2015: A persistent recession for most of us, a candidate scarier than Trump, and Flash fizzles
Recession persists for all but the top 20 percent of wage earners
How are you doing compared to 2007? The U.S. Bureau of Labor Statistics released a graph of real compensation and wages for civilian workers, by percentile, 2007-2014. Kevin Drum writes in a July 13, 2015, article on Mother Jones that only the top 20 percent of wage earners increased their earnings, and only the top 10 percent increased by more than 3 percent.
(Sigh.)
-----------------------------------------------------
The only Republican Presidential candidate scarier than Donald Trump
Paul Krugman unmasks Jeb Bush, as reported by AlterNet's Janet Allon in a July 13, 2015, article.
------------------------------------------------------
Ad blocking saves a Canadian university 40 percent of its bandwidth bill
Researchers at Simon Foster University report (pdf) on the school's use of AdBlock Plus in an "enterprise setting." Tech Week Europe's Ben Sullivan writes in a July 10, 2015, article that AdBlock Plus reduced bandwidth on the university's internal network between 25 and 40 percent.
Saving bandwidth by blocking unwanted content: What's not to like?
-------------------------------------------------------
Flash is so 2005
When I heard that Firefox now blocks Adobe's Flash scripts by default, I was thankful we're a big step closer to putting the web-animation technology out of our misery. I've been blocking Flash and other scripts for so long it has become just another part of browsing.
As Macworld's Glenn Fleischman writes in a July 14, 2015, article, Flash had its day, but that day was a lot of years ago. Fleischman claims that Flash has already become such an afterthought that killing it once and for all would barely cause a ripple. Out with a whimper works for me.
How are you doing compared to 2007? The U.S. Bureau of Labor Statistics released a graph of real compensation and wages for civilian workers, by percentile, 2007-2014. Kevin Drum writes in a July 13, 2015, article on Mother Jones that only the top 20 percent of wage earners increased their earnings, and only the top 10 percent increased by more than 3 percent.
(Sigh.)
-----------------------------------------------------
The only Republican Presidential candidate scarier than Donald Trump
Paul Krugman unmasks Jeb Bush, as reported by AlterNet's Janet Allon in a July 13, 2015, article.
------------------------------------------------------
Ad blocking saves a Canadian university 40 percent of its bandwidth bill
Researchers at Simon Foster University report (pdf) on the school's use of AdBlock Plus in an "enterprise setting." Tech Week Europe's Ben Sullivan writes in a July 10, 2015, article that AdBlock Plus reduced bandwidth on the university's internal network between 25 and 40 percent.
Saving bandwidth by blocking unwanted content: What's not to like?
-------------------------------------------------------
Flash is so 2005
When I heard that Firefox now blocks Adobe's Flash scripts by default, I was thankful we're a big step closer to putting the web-animation technology out of our misery. I've been blocking Flash and other scripts for so long it has become just another part of browsing.
As Macworld's Glenn Fleischman writes in a July 14, 2015, article, Flash had its day, but that day was a lot of years ago. Fleischman claims that Flash has already become such an afterthought that killing it once and for all would barely cause a ripple. Out with a whimper works for me.
July 7, 2015: A long-overdue turning of the political tide

The Establishment -- Democrats and Republicans alike -- are slow to pick up on the nation's continuing shift to the left, toward a more-progressive social agenda.
July 7, 2015: Obamacare -- A misstep in the right direction

Republicans feign outrage at the Supreme Court decision that found the Affordable Care Act's federal exchanges are Constitutional, but their deep-pockets supporters stand to profit greatly as a result of the ruling.
June 30, 2015: Everyday Windows 10 users become beta testers for the Enterprise Edition

Microsoft's offer of a free upgrade for users of Windows 7 and 8.1 comes with a few gotchas -- but it's still an offer worth taking for most of us.
Tech shorts for June 30, 2015: Healthcare set to reap big-data benefits, and the advantages of front-loading your daily activities
Big data tackles mental healthcare...
According to a 2013 survey conducted by the U.S. Department of Health and Human Services (pdf), one in five people in the U.S. over the age of 12 has a serious substance-abuse or mental-health problem, yet nearly 70 percent of these people receive no treatment for the condition. In fact, more than 90 percent of the people who abuse or depend on alcohol remain untreated, according to the HHS survey.
A new company called Lyra Health hopes to improve the level of treatment for substance abuse and mental health by applying big data and predictive analytics to the problem. The company, which was founded by former Facebook and Genentech CFO David Ebersman, intends to help patients find appropriate treatment options, and to assist caregivers in identifying people in need of their help. Tech Crunch's Christine McGee describes Lyra Health's strategy in a June 26, 2015, article.
In the past week, two people very close to our family sought the help of mental-health professionals. I'm happy to report both are doing much better as they begin the long journey back to health.
--------------------------------------------------------------
...And does the same for cancer treatment
Perhaps the most important health battle of the age is the fight against cancer. Big data is playing a part in that war as well. As Forbes' Bernard Marr writes in a June 28, 2015, article, the American Society for Clinical Oncology has initiated the CancerLinQ project intended to aggregate data from all cancer patients in the U.S. and make it available for analysis by all researchers and healthcare providers.
In addition, IBM's Watson AI-based analytics engine has now been programmed to help match cancer patients with treatments tailored to their specific needs. Another cancer-treatment program applying big-data principles is Flatiron Health's OncologyCloud, which collects unstructured data from all cancer patients not participating in clinical trials and reformats it in a way that allows it to be analyzed as a single huge dataset.
Marr points out that there is a tremendous amount of work to be done to eliminate all cancer deaths, but with big data's help, cancer will become a chronic, treatable, non-terminal disease -- if not altogether curable.
--------------------------------------------------------------
It's enough to convert me into an early riser... almost
Most mornings I'm lucky to get one thing done before 8:00 a.m., let alone eight. (Does dreaming count? Snoring? Don't think so.) Benjamin Hardy claims in a June 23, 2015, article on the Observer site that a simple, eight-step morning routine will revitalize your life and shake you out of survival mode.
The first step I can usually handle okay: Get at least 7 hours of sleep each night. A good night's sleep has been associated with longer life, better memory, reduced inflammation, lower stress, increased attention and creativity, and less likelihood of getting into an accident.
Hardy's other steps are to pray or meditate each morning, engage in a "hard" physical activity, consume at least 30 grams of protein for breakfast (representing at least 40 percent of your breakfast calories), take a cold shower, read or listen to something uplifting, review your life vision, and accomplish something that gets you closer to your long-term goals.
And you thought your mornings were busy already.
I'm all for sleep, physical activity, uplifting media, prayer/meditation, and even cold showers (this is the one step I've actually adopted -- to an extent, at least). But considering an egg has about six grams of protein, getting a total of 30 protein grams in one meal could require one heck of a breakfast. The good news: Reviewing my "life vision" won't take much time at all, and my long-term goal remains to live long enough to have anything resembling a long-term goal.
So I guess you could say I'm ahead of the game in at least some respects. Wake me when it's time for my five-egg omelet.
According to a 2013 survey conducted by the U.S. Department of Health and Human Services (pdf), one in five people in the U.S. over the age of 12 has a serious substance-abuse or mental-health problem, yet nearly 70 percent of these people receive no treatment for the condition. In fact, more than 90 percent of the people who abuse or depend on alcohol remain untreated, according to the HHS survey.
A new company called Lyra Health hopes to improve the level of treatment for substance abuse and mental health by applying big data and predictive analytics to the problem. The company, which was founded by former Facebook and Genentech CFO David Ebersman, intends to help patients find appropriate treatment options, and to assist caregivers in identifying people in need of their help. Tech Crunch's Christine McGee describes Lyra Health's strategy in a June 26, 2015, article.
In the past week, two people very close to our family sought the help of mental-health professionals. I'm happy to report both are doing much better as they begin the long journey back to health.
--------------------------------------------------------------
...And does the same for cancer treatment
Perhaps the most important health battle of the age is the fight against cancer. Big data is playing a part in that war as well. As Forbes' Bernard Marr writes in a June 28, 2015, article, the American Society for Clinical Oncology has initiated the CancerLinQ project intended to aggregate data from all cancer patients in the U.S. and make it available for analysis by all researchers and healthcare providers.
In addition, IBM's Watson AI-based analytics engine has now been programmed to help match cancer patients with treatments tailored to their specific needs. Another cancer-treatment program applying big-data principles is Flatiron Health's OncologyCloud, which collects unstructured data from all cancer patients not participating in clinical trials and reformats it in a way that allows it to be analyzed as a single huge dataset.
Marr points out that there is a tremendous amount of work to be done to eliminate all cancer deaths, but with big data's help, cancer will become a chronic, treatable, non-terminal disease -- if not altogether curable.
--------------------------------------------------------------
It's enough to convert me into an early riser... almost
Most mornings I'm lucky to get one thing done before 8:00 a.m., let alone eight. (Does dreaming count? Snoring? Don't think so.) Benjamin Hardy claims in a June 23, 2015, article on the Observer site that a simple, eight-step morning routine will revitalize your life and shake you out of survival mode.
The first step I can usually handle okay: Get at least 7 hours of sleep each night. A good night's sleep has been associated with longer life, better memory, reduced inflammation, lower stress, increased attention and creativity, and less likelihood of getting into an accident.
Hardy's other steps are to pray or meditate each morning, engage in a "hard" physical activity, consume at least 30 grams of protein for breakfast (representing at least 40 percent of your breakfast calories), take a cold shower, read or listen to something uplifting, review your life vision, and accomplish something that gets you closer to your long-term goals.
And you thought your mornings were busy already.
I'm all for sleep, physical activity, uplifting media, prayer/meditation, and even cold showers (this is the one step I've actually adopted -- to an extent, at least). But considering an egg has about six grams of protein, getting a total of 30 protein grams in one meal could require one heck of a breakfast. The good news: Reviewing my "life vision" won't take much time at all, and my long-term goal remains to live long enough to have anything resembling a long-term goal.
So I guess you could say I'm ahead of the game in at least some respects. Wake me when it's time for my five-egg omelet.
June 30, 2015: Obamacare decision imposes limits on executive power

In a decision that parallels one of the most important in its history, the Supreme Court affirms the executive branch's interpretation of the Affordable Care Act while simultaneously asserting its role as the final arbiter of legislative intent.
June 23, 2015: It's time to get serious about prosecuting Internet threats

When web vermin cross the line from obnoxious, insulting, and crass comments to credible threats of violence, it's time to call the cops. But who ya gonna call?
June 16, 2015: Worst. Supreme. Court. Ever.

The U.S. Supreme Court is destroying our democracy. They've been at it now for more than two decades. Only Congress can undo the damage the court has done and continues to do. Will they? Don't hold your breath.
Tech shorts for June 16, 2015: Apple not a privacy paragon? And Google's ad-blocking quandary
Apple: Not quite the paragon of privacy virtue it claims to be?
When Apple CEO Tim Cook challenged Google (primarily), Facebook (secondarily), and other tech services that make their money by selling what they know about their customers to honor consumers' privacy, you had to know there would be a "pot calling the kettle black" response. (In the June 9, 2015, Weekly I wrote about Cook's speech at the Electronic Privacy Information Center's Champions of Freedom event at which he was honored.)
Sure enough, the pundits had a field day with Cook's comments, if not an outright feeding frenzy. In a June 10, 2015, article, the New York Times' Farhad Manjoo points out that Cook overlooked two facts: Apple collects quite a bit of information about its customers and profits from use of that data; and Apple benefits directly from the success of Google, Facebook, and other services whose revenue depends on selling what they know about their users to advertisers and other third parties.
Yes, "free" services have propelled the astounding growth of the Internet. Yes, those services deliver the Internet's benefits to billions of people around the world who would likely be locked out if they had to pay for them. And yes, Apple's products tend to lock customers into the Apple universe. But as Re/code's Walter Mossberg writes in a June 12, 2015, article, Apple is breaking new ground in the tech industry by presenting privacy as a product. The tagline? "You are in control."
If only we could really believe that. Well, it's a start.
------------------------------------------------------------
Google's caught in the middle of the ad-blocking war
When it comes to ad-blocking browser extensions, Google can't win for losing. The anti-ad-blocking service PageFair states in a June 8, 2015, post that Google CEO Larry Page "neatly sidestepp[ed]" a question at the company's recent stockholder meeting about the effect of ad blocking on Google's revenue. The web-ad universe criticized the company for agreeing to pay AdBlock Plus, reportedly $25 million, to participate in AdBlock's Acceptable Ads program.
PageFair guestimated the impact of ad blocking on Google's bottom line by using a conservative estimate of ad-blocking extensions being used by 10 percent of U.S. browsers (the actual figure is claimed to be closer to 14 percent). By being whitelisted, Google is recouping $1 billion in revenue it would otherwise have lost -- not a bad return on its $25 million investment. However, Google loses twice that amount from the ads that are blocked.
Since 57 percent of Google's overall traffic comes from overseas, and ad blocking is more prevalent in Europe in particular, PageFair extrapolates Google's losses and comes to a figure of $3.1 billion in revenue lost due to blocked ads. The real bad news for Google and other online services that depend on ads for their revenue: Use of ad blockers is expected to increase by 50 percent in 2015, and to spread to mobile devices. There's now a version of AdBlock Plus for Android devices, and the next release of Apple's Safari browser for iOS 9 will feature a downloadable ad-blocking extension, as NiemanLab's Joshua Benton writes in a June 10, 2015, article.
Sooner or later, Internet services will wise up and offer us a choice: Pay a little bit to get your content without ads and tracking, or get the content for free along with ads and tracking. The system could work much like California's FasTrak for bridge tolls: You keep money on deposit from which the web micropayment "tolls" would be paid. The best way for consumers to force the creation of such a pay-or-free system is to keep blocking ads.
When Apple CEO Tim Cook challenged Google (primarily), Facebook (secondarily), and other tech services that make their money by selling what they know about their customers to honor consumers' privacy, you had to know there would be a "pot calling the kettle black" response. (In the June 9, 2015, Weekly I wrote about Cook's speech at the Electronic Privacy Information Center's Champions of Freedom event at which he was honored.)
Sure enough, the pundits had a field day with Cook's comments, if not an outright feeding frenzy. In a June 10, 2015, article, the New York Times' Farhad Manjoo points out that Cook overlooked two facts: Apple collects quite a bit of information about its customers and profits from use of that data; and Apple benefits directly from the success of Google, Facebook, and other services whose revenue depends on selling what they know about their users to advertisers and other third parties.
Yes, "free" services have propelled the astounding growth of the Internet. Yes, those services deliver the Internet's benefits to billions of people around the world who would likely be locked out if they had to pay for them. And yes, Apple's products tend to lock customers into the Apple universe. But as Re/code's Walter Mossberg writes in a June 12, 2015, article, Apple is breaking new ground in the tech industry by presenting privacy as a product. The tagline? "You are in control."
If only we could really believe that. Well, it's a start.
------------------------------------------------------------
Google's caught in the middle of the ad-blocking war
When it comes to ad-blocking browser extensions, Google can't win for losing. The anti-ad-blocking service PageFair states in a June 8, 2015, post that Google CEO Larry Page "neatly sidestepp[ed]" a question at the company's recent stockholder meeting about the effect of ad blocking on Google's revenue. The web-ad universe criticized the company for agreeing to pay AdBlock Plus, reportedly $25 million, to participate in AdBlock's Acceptable Ads program.
PageFair guestimated the impact of ad blocking on Google's bottom line by using a conservative estimate of ad-blocking extensions being used by 10 percent of U.S. browsers (the actual figure is claimed to be closer to 14 percent). By being whitelisted, Google is recouping $1 billion in revenue it would otherwise have lost -- not a bad return on its $25 million investment. However, Google loses twice that amount from the ads that are blocked.
Since 57 percent of Google's overall traffic comes from overseas, and ad blocking is more prevalent in Europe in particular, PageFair extrapolates Google's losses and comes to a figure of $3.1 billion in revenue lost due to blocked ads. The real bad news for Google and other online services that depend on ads for their revenue: Use of ad blockers is expected to increase by 50 percent in 2015, and to spread to mobile devices. There's now a version of AdBlock Plus for Android devices, and the next release of Apple's Safari browser for iOS 9 will feature a downloadable ad-blocking extension, as NiemanLab's Joshua Benton writes in a June 10, 2015, article.
Sooner or later, Internet services will wise up and offer us a choice: Pay a little bit to get your content without ads and tracking, or get the content for free along with ads and tracking. The system could work much like California's FasTrak for bridge tolls: You keep money on deposit from which the web micropayment "tolls" would be paid. The best way for consumers to force the creation of such a pay-or-free system is to keep blocking ads.
June 9, 2015: Five indications that we are currently between regimes

People are starting to figure out that they're getting a raw deal from politicians and web services alike, but they're not yet sure what to do about it.
June 2, 2015: The five-minute Facebook security checkup
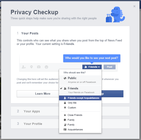
The social network's streamlined privacy settings make it easy to ensure you're not oversharing (or undersharing, for that matter).
Legal shorts for June 2, 2015: FCC to get tough with ISPs on customer privacy, and a warning to lawyers about the increasing ransomware threat
FCC warns ISPs: Tougher customer-privacy regulation coming soon
The U.S. Federal Communications Commission released an Enforcement Advisory for Internet service providers on May 20, 2015, that indicates they'll be required to follow stricter rules for use of their customers' personal information starting on June 12, 2015. ISPs are now subject to Section 222 of the Communications Act, which states that companies “shall only use, disclose, or permit access to individually identifiable customer proprietary network information” in the provision of services. (47 U.S.C. § 222(c)(1))
The specifics of what information is covered and what constitutes the provision of services are uncertain, according to Matthew Riemer and Paul Werner of Sheppard Mullin in a June 1, 2015, article on the JD Supra Business Advisor site. What is certain is that the FCC intends to hold ISPs to the higher Title II standard for protecting their customers' private information.
----------------------------------------------------------------
Ransomware puts lawyers behind the eight ball
At midnight on May 25, 2015, a piece of ransomware called Locker became active, blocking workers at several companies from signing into their computers until they had paid a ransom to the malware's authors. Security firm KnowBe4 describes how Locker works in a May 27, 2015, press release.
Ransomware such as Locker poses a tremendous threat to law firms in particular, according to Legaltech News' Ed Silverstein in a May 28, 2015, article (registration required). Once ransomware has encrypted the firm's data, it has no choice but to pay the ransom to decrypt it. Even then, the company could be liable for allowing a third party to access confidential client information.
KnowBe4 CEO Stu Sjouwerman recommends that people have a recent full backup handy at all times, keep all their software up-to-date, and avoid clicking ads, which are increasingly used to spread malware of all types. Sjouwerman also emphasizes the importance of training employees in good data-security practices.
Well, best of intentions aside, the malware purveyors find new ways to spread their menace quicker than security experts can defend against them. The safest approach to protecting clients' confidential information is to store it on a computer that isn't connected to any network, and that doesn't allow data to be copied to any removable media. (That's how Caitlyn Jenner's Vanity Fair photos were safeguarded prior to their publication earlier this week, by the way.)
Practical? Not at all, but you simply have to acknowledge that any data stored on a computer with a network link is inherently insecure. The best option for law firms of all sizes is to use an online storage service that encrypts all data in transit and when it's stored. Even then, the company will have to take great pains to protect the decryption keys, as well as ensure all the PCs, tablets, and phones used by employees to access the data use encryption to access and store it.
A recent roundup of online storage services by PC Magazine gave high grades for security to CertainSafe and Code42 Crash Plan. CertainSafe refers to itself as "Insanely Secure" because it uses MicroEncryption to encrypt individual files to the byte level, in addition to standard 256-bit AES encryption, authentication controls, and "personal challenge questions." Code42 Crash Plan offers the unique ability to skip the cloud by having your data stored securely on a PC at the location of your choice, such as a business-partner's office or even a friend's house.
Even with the most cautious approach to data security, law firms have to prepare for the day they are locked out of their own data. If you don't believe me, just ask Sony.
The U.S. Federal Communications Commission released an Enforcement Advisory for Internet service providers on May 20, 2015, that indicates they'll be required to follow stricter rules for use of their customers' personal information starting on June 12, 2015. ISPs are now subject to Section 222 of the Communications Act, which states that companies “shall only use, disclose, or permit access to individually identifiable customer proprietary network information” in the provision of services. (47 U.S.C. § 222(c)(1))
The specifics of what information is covered and what constitutes the provision of services are uncertain, according to Matthew Riemer and Paul Werner of Sheppard Mullin in a June 1, 2015, article on the JD Supra Business Advisor site. What is certain is that the FCC intends to hold ISPs to the higher Title II standard for protecting their customers' private information.
----------------------------------------------------------------
Ransomware puts lawyers behind the eight ball
At midnight on May 25, 2015, a piece of ransomware called Locker became active, blocking workers at several companies from signing into their computers until they had paid a ransom to the malware's authors. Security firm KnowBe4 describes how Locker works in a May 27, 2015, press release.
Ransomware such as Locker poses a tremendous threat to law firms in particular, according to Legaltech News' Ed Silverstein in a May 28, 2015, article (registration required). Once ransomware has encrypted the firm's data, it has no choice but to pay the ransom to decrypt it. Even then, the company could be liable for allowing a third party to access confidential client information.
KnowBe4 CEO Stu Sjouwerman recommends that people have a recent full backup handy at all times, keep all their software up-to-date, and avoid clicking ads, which are increasingly used to spread malware of all types. Sjouwerman also emphasizes the importance of training employees in good data-security practices.
Well, best of intentions aside, the malware purveyors find new ways to spread their menace quicker than security experts can defend against them. The safest approach to protecting clients' confidential information is to store it on a computer that isn't connected to any network, and that doesn't allow data to be copied to any removable media. (That's how Caitlyn Jenner's Vanity Fair photos were safeguarded prior to their publication earlier this week, by the way.)
Practical? Not at all, but you simply have to acknowledge that any data stored on a computer with a network link is inherently insecure. The best option for law firms of all sizes is to use an online storage service that encrypts all data in transit and when it's stored. Even then, the company will have to take great pains to protect the decryption keys, as well as ensure all the PCs, tablets, and phones used by employees to access the data use encryption to access and store it.
A recent roundup of online storage services by PC Magazine gave high grades for security to CertainSafe and Code42 Crash Plan. CertainSafe refers to itself as "Insanely Secure" because it uses MicroEncryption to encrypt individual files to the byte level, in addition to standard 256-bit AES encryption, authentication controls, and "personal challenge questions." Code42 Crash Plan offers the unique ability to skip the cloud by having your data stored securely on a PC at the location of your choice, such as a business-partner's office or even a friend's house.
Even with the most cautious approach to data security, law firms have to prepare for the day they are locked out of their own data. If you don't believe me, just ask Sony.
May 26, 2015: When ads attack: Web ad networks battle the blockers
Use of ad-blocking browser add-ons continues to increase, in large part due to the growing risk of malevolent ads.
May 19, 2015: Flying the furious skies: How to stay sane on a commercial flight

As travel season approaches, here's a gentle reminder about the importance of civility in transit -- by passengers and airline employees alike.
Tech shorts for May 19, 2015: A 'privacy fee' for airline passengers, free iPhone app for finding WiFi hotspots, and unobtrusive employee monitoring
Airlines preparing to charge their passengers a 'privacy' fee
When you shop for an airline ticket online, you may soon be quoted a higher price if you choose not to identify yourself beforehand. Elliott.org's Charlie Leocha writes in a May 9, 2015, post that a group of U.S. senators sent a letter to Department of Transportation Secretary Anthony Foxx in which they expressed their concern about personalized pricing of airline tickets.
Delta Airlines was already caught serving up different fees for the same flights when a person searched with and without identifying themselves, but the DOT called it the result of a "computer glitch." It appears inevitable that differential pricing is making its way to the airline industry. (Last week's Weekly described how to make differential pricing work for you rather than against you.)
------------------------------------------------------------
Free phone app helps you find a WiFi hotspot
I'm not a big fan of public WiFi, which has become a magnet for malware purveyors. But sometimes you'll be out and about when all of a sudden you just gotta get online, like right now. For those instances, there's the free WiFi Mapper app for iPhone -- and soon for Android devices, according to the program's vendor, OpenSignal.
TechCrunch's Natasha Lomas explains in a May 14, 2015, article that OpenSignal makes its money by selling anonymized cell-phone tracking data to telcos to help them determine the quality of their cell networks. By default, the app's cell-tracking feature is deactivated, but that could change in the future, according to the company. WiFi Mapper is said to offer more-accurate information about hotspots -- including whether they're free or paid -- by aggregating data on the WiFi activity of the program's 1.5 million active users.
WiFi Mapper coordinates with other sources, such as the Foursquare database, to make it easier to determine the hotspot's venue, such as whether it's located in a cafe or bar. OpenSignal intends to build on this "contextual awareness" to enhance user interaction with hotspots even further.
I can see it now: "Hide Starbucks, show Peet's."
---------------------------------------------------------------
The 'Lime Equation': The key to monitoring employees unobtrusively
If you're a manager, you need to be able to distinguish the employees who are doing well from those who aren't. In a May 18, 2015, post on TechCrunch, SumAll CEO Dane Atkinson describes how he was able to determine which bartender at the restaurant he was managing was stealing from the till by monitoring the establishment's consumption of limes.
Here's how it worked: First, Atkinson identified a correlation between total drink sales and the amount of limes being purchased each week. He scheduled bartenders and bar backs so that he could identify who was working when drink sales no longer fell in line with lime consumption. It took only a week to identify the thief, who Atkinson caught trying to leave work one day with $2,500 in cash in his bag. The other workers were mystified about how Atkinson was able to nab the dishonest employee, which served to prevent other thefts.
After he switched from the hospitality industry to a tech startup, Atkinson applied the principles behind the Lime Equation to another work-quality indicator: the total volume of email his employees sent and received, and the ratio of internal to external emails. Whenever a worker's email volume fell below a particular threshold, Atkinson met with the employee to determine whether they were feeling disgruntled at work or experiencing personal problems.
The secrets to the Lime Equation's success are that you have to find an accurate indicator of worker productivity (or honesty, in the case of the limes), and then to keep the indicator secret from the employees you're monitoring. The result, according to Atkinson, is a workforce that doesn't feel like it's under constant surveillance, and managers who are able to get a good reading on how well their employees are doing in their jobs.
When you shop for an airline ticket online, you may soon be quoted a higher price if you choose not to identify yourself beforehand. Elliott.org's Charlie Leocha writes in a May 9, 2015, post that a group of U.S. senators sent a letter to Department of Transportation Secretary Anthony Foxx in which they expressed their concern about personalized pricing of airline tickets.
Delta Airlines was already caught serving up different fees for the same flights when a person searched with and without identifying themselves, but the DOT called it the result of a "computer glitch." It appears inevitable that differential pricing is making its way to the airline industry. (Last week's Weekly described how to make differential pricing work for you rather than against you.)
------------------------------------------------------------
Free phone app helps you find a WiFi hotspot
I'm not a big fan of public WiFi, which has become a magnet for malware purveyors. But sometimes you'll be out and about when all of a sudden you just gotta get online, like right now. For those instances, there's the free WiFi Mapper app for iPhone -- and soon for Android devices, according to the program's vendor, OpenSignal.
TechCrunch's Natasha Lomas explains in a May 14, 2015, article that OpenSignal makes its money by selling anonymized cell-phone tracking data to telcos to help them determine the quality of their cell networks. By default, the app's cell-tracking feature is deactivated, but that could change in the future, according to the company. WiFi Mapper is said to offer more-accurate information about hotspots -- including whether they're free or paid -- by aggregating data on the WiFi activity of the program's 1.5 million active users.
WiFi Mapper coordinates with other sources, such as the Foursquare database, to make it easier to determine the hotspot's venue, such as whether it's located in a cafe or bar. OpenSignal intends to build on this "contextual awareness" to enhance user interaction with hotspots even further.
I can see it now: "Hide Starbucks, show Peet's."
---------------------------------------------------------------
The 'Lime Equation': The key to monitoring employees unobtrusively
If you're a manager, you need to be able to distinguish the employees who are doing well from those who aren't. In a May 18, 2015, post on TechCrunch, SumAll CEO Dane Atkinson describes how he was able to determine which bartender at the restaurant he was managing was stealing from the till by monitoring the establishment's consumption of limes.
Here's how it worked: First, Atkinson identified a correlation between total drink sales and the amount of limes being purchased each week. He scheduled bartenders and bar backs so that he could identify who was working when drink sales no longer fell in line with lime consumption. It took only a week to identify the thief, who Atkinson caught trying to leave work one day with $2,500 in cash in his bag. The other workers were mystified about how Atkinson was able to nab the dishonest employee, which served to prevent other thefts.
After he switched from the hospitality industry to a tech startup, Atkinson applied the principles behind the Lime Equation to another work-quality indicator: the total volume of email his employees sent and received, and the ratio of internal to external emails. Whenever a worker's email volume fell below a particular threshold, Atkinson met with the employee to determine whether they were feeling disgruntled at work or experiencing personal problems.
The secrets to the Lime Equation's success are that you have to find an accurate indicator of worker productivity (or honesty, in the case of the limes), and then to keep the indicator secret from the employees you're monitoring. The result, according to Atkinson, is a workforce that doesn't feel like it's under constant surveillance, and managers who are able to get a good reading on how well their employees are doing in their jobs.
May 12, 2015: Online shopping tips: Put differential pricing to work for you

Sites adjust the price of the items they sell based on your unique characteristics, which means you can save money by changing how you present yourself.
Tech shorts for May 12, 2015: Big-name ad networks serve up malware, and the $9 computer is almost here
The online-ad industry just got creepier
The April 7, 2015, Weekly explained why ad-injecting browser add-ons are dangerous: Not only do they cheat sites out of ad revenue, they deliver malware and otherwise threaten your privacy and security. A May 6, 2015, post on the Google Online Security Blog reports that 5.5 percent of the people visiting Google sites were using a browser that had an ad-injection add-on installed. These programs are ripping off such big-name retailers as Sears, Walmart, Target, and EBay. Even worse, 77 percent of the ad injectors spread by using one of the three major ad networks: dealtime.com, pricegrabber.com, and bizrate.com.
Google's post points out that the company is doing what it can to combat ad injectors, such as removing dozens of extensions from its Chrome Web Store and warning people when they're about to download "deceptive software." However, the real solution requires cleaning up the ad networks the injectors rely on. That doesn't appear to be happening anytime soon.
At the risk of repeating myself, you can protect against malicious ads and other web threats by using the free AdBlock Plus extension and the other security add-ons I described in the September 9, 2015, Weekly, "Three free browser add-ons protect against cyber-crime."
---------------------------------------------------------------
Coming soon: The $9 computer
Someday, maybe, computers will be free. Until then, there's Next Thing's $9 Chip, which has a 1GHz processor, 512MB of RAM, 4GB of internal storage, Wi-Fi, Bluetooth, built-in composite output, and the ability to link to VGA and HDMI displays via an adapter. ReadWrite's Brian P. Rubin describes the computer in a May 11, 2015, article.
The Chip even converts to a portable computer by attaching a 2.7 volt lithium-ion polymer battery to its built-in battery power circuit. The device's open-source operating system lets you run the Chromium browser and LibreOffice productivity software. As Rubin points out, while $9 sounds pretty cheap for a general-purpose computer, if you're willing to wait a little longer, you could get an even-better deal. A computer for free? Maybe not. For pocket change? Maybe so.
The April 7, 2015, Weekly explained why ad-injecting browser add-ons are dangerous: Not only do they cheat sites out of ad revenue, they deliver malware and otherwise threaten your privacy and security. A May 6, 2015, post on the Google Online Security Blog reports that 5.5 percent of the people visiting Google sites were using a browser that had an ad-injection add-on installed. These programs are ripping off such big-name retailers as Sears, Walmart, Target, and EBay. Even worse, 77 percent of the ad injectors spread by using one of the three major ad networks: dealtime.com, pricegrabber.com, and bizrate.com.
Google's post points out that the company is doing what it can to combat ad injectors, such as removing dozens of extensions from its Chrome Web Store and warning people when they're about to download "deceptive software." However, the real solution requires cleaning up the ad networks the injectors rely on. That doesn't appear to be happening anytime soon.
At the risk of repeating myself, you can protect against malicious ads and other web threats by using the free AdBlock Plus extension and the other security add-ons I described in the September 9, 2015, Weekly, "Three free browser add-ons protect against cyber-crime."
---------------------------------------------------------------
Coming soon: The $9 computer
Someday, maybe, computers will be free. Until then, there's Next Thing's $9 Chip, which has a 1GHz processor, 512MB of RAM, 4GB of internal storage, Wi-Fi, Bluetooth, built-in composite output, and the ability to link to VGA and HDMI displays via an adapter. ReadWrite's Brian P. Rubin describes the computer in a May 11, 2015, article.
The Chip even converts to a portable computer by attaching a 2.7 volt lithium-ion polymer battery to its built-in battery power circuit. The device's open-source operating system lets you run the Chromium browser and LibreOffice productivity software. As Rubin points out, while $9 sounds pretty cheap for a general-purpose computer, if you're willing to wait a little longer, you could get an even-better deal. A computer for free? Maybe not. For pocket change? Maybe so.
Legal shorts for May 12, 2015: Fight corruption by taking a tip from insects, and no warrant protections for cell-location data
The cure for corruption is... righteousness?
I never thought there were such things as renegade ants, wasps, and bees. But according to Suzanne Sadedin writing in a May 11, 2015, article on Aeon, every now and then one of these highly socialized insects will step out of line, perhaps deciding to lay their own eggs rather than leaving that job to the colony's queen. When this happens, the other members of the colony turn on the rebel and thereby maintain the social order.
Sadedin correlates an insect colony's response to aberrant behavior to corruption in our society. It all comes down to power: When you give one subgroup more power than the rest of the group, that subgroup ultimately abuses that power for its own benefit. Wherever there are police and other authority figures, there's corruption, particularly bribery. Sadedin uses game theory to show why corruption in such situations is inevitable. She demonstrates that people in power naturally feel entitled, and that entitlement allows them to act selfishly, and to justify their actions based on their power.
Sadedin's solution to widespread corruption in our society is for everyone to become a cop: "If we decrease power inequalities, increase punishments and reward punishers, in theory that should trigger a societal transition to righteousness." We're just too darned tolerant, according to Sadedin. If everyone reported every transgression they witness, however minor (such as rolling through a stop sign), peer pressure would ultimately serve as a deterrent.
Imagine a world where people are reporting their neighbors to the "authorities" for every little breach of social etiquette. I think I would settle for more transparency in how police and other government authorities operate. Practically speaking, there will always be a need for some people to be placed in positions of authority over the rest of us.
Of course, there will always be a need for a separate group of people to be given authority to watch the watchers. It's the stuff that happens in the shadows that we need to shine a light on.
---------------------------------------------------------------
Still no warrant requirement for cell-site location records
Police are relying on the Stored Communications Act to access people's cell-phone location history with a simple court order rather than requiring a search warrant. The Electronic Frontier Foundation's Cindy Cohn and Hanni Fakhoury write in a May 8, 2015, article on Gizmodo that the U.S. Court of Appeals for the Eleventh Circuit affirmed this in United States v. Davis. That case involved using the defendant's cell-site history to place him at the scenes of seven robberies.
The Eleventh Circuit ruled that people have no expectation of privacy when they give information to a third party, which in this case is their cell carrier. The third-party doctrine originated in a 1979 Supreme Court decision, Smith v. Maryland, which turned on access to a pen register that recorded the numbers dialed by a stationary telephone. As Cohn and Fakhoury explain, the amount of information collected by cell-site locators dwarfs that available in a 1970s-era pen register.
The authors also point out that the Eleventh Circuit is confusing privacy with secrecy. Just because you disclose personal information to one party doesn't mean you're waiving your right to withhold the information from anyone else. (See Samuel D. Warren and Louis D. Brandeis, The Right to Privacy, Harvard Law Review, V. IV, No. 5, December 1890.) When will these courts wise up?
I never thought there were such things as renegade ants, wasps, and bees. But according to Suzanne Sadedin writing in a May 11, 2015, article on Aeon, every now and then one of these highly socialized insects will step out of line, perhaps deciding to lay their own eggs rather than leaving that job to the colony's queen. When this happens, the other members of the colony turn on the rebel and thereby maintain the social order.
Sadedin correlates an insect colony's response to aberrant behavior to corruption in our society. It all comes down to power: When you give one subgroup more power than the rest of the group, that subgroup ultimately abuses that power for its own benefit. Wherever there are police and other authority figures, there's corruption, particularly bribery. Sadedin uses game theory to show why corruption in such situations is inevitable. She demonstrates that people in power naturally feel entitled, and that entitlement allows them to act selfishly, and to justify their actions based on their power.
Sadedin's solution to widespread corruption in our society is for everyone to become a cop: "If we decrease power inequalities, increase punishments and reward punishers, in theory that should trigger a societal transition to righteousness." We're just too darned tolerant, according to Sadedin. If everyone reported every transgression they witness, however minor (such as rolling through a stop sign), peer pressure would ultimately serve as a deterrent.
Imagine a world where people are reporting their neighbors to the "authorities" for every little breach of social etiquette. I think I would settle for more transparency in how police and other government authorities operate. Practically speaking, there will always be a need for some people to be placed in positions of authority over the rest of us.
Of course, there will always be a need for a separate group of people to be given authority to watch the watchers. It's the stuff that happens in the shadows that we need to shine a light on.
---------------------------------------------------------------
Still no warrant requirement for cell-site location records
Police are relying on the Stored Communications Act to access people's cell-phone location history with a simple court order rather than requiring a search warrant. The Electronic Frontier Foundation's Cindy Cohn and Hanni Fakhoury write in a May 8, 2015, article on Gizmodo that the U.S. Court of Appeals for the Eleventh Circuit affirmed this in United States v. Davis. That case involved using the defendant's cell-site history to place him at the scenes of seven robberies.
The Eleventh Circuit ruled that people have no expectation of privacy when they give information to a third party, which in this case is their cell carrier. The third-party doctrine originated in a 1979 Supreme Court decision, Smith v. Maryland, which turned on access to a pen register that recorded the numbers dialed by a stationary telephone. As Cohn and Fakhoury explain, the amount of information collected by cell-site locators dwarfs that available in a 1970s-era pen register.
The authors also point out that the Eleventh Circuit is confusing privacy with secrecy. Just because you disclose personal information to one party doesn't mean you're waiving your right to withhold the information from anyone else. (See Samuel D. Warren and Louis D. Brandeis, The Right to Privacy, Harvard Law Review, V. IV, No. 5, December 1890.) When will these courts wise up?
May 5, 2015: We're sitting on a big-data goldmine

The benefits to the public of gleaning today's massive data stores for insights into our health and safety are nearly limitless -- if only we can trust the people doing the collecting.
Legal shorts for May 5, 2015: Google's misuse of children's private info; Supreme Court to decide whether data brokers fall under FCRA
Google violates prohibition against profiling children
I was all set to write about Google's new extension for the Chrome browser that defends against phishing attacks by warning you when you enter your Google password at a non-Google site. Password Alert detects your password being entered on a potentially bogus site and pops up a warning that your password may have been compromised, so click the provided link to change it. The plug-in is described in an April 29, 2015, post on the Google Blog.
Before I could utter, "Bully for Google!" I came across an April 26, 2015, article on Medium.com by Tracy Mitrano that reports on Google's practice of creating profiles of children who use the company's services at school. The Family Educational Rights and Privacy Act (FERPA) requires that vendors act as "school officials" in protecting students' education records. This prohibits vendors from using and/or reselling education records for commercial purposes.
The U.S. Department of Education's Family Compliance Privacy Office has ruled that schools remain responsible for the protection of education records even after they have outsourced management of the records to a third party. The office has also ruled that any data mining of education records for commercial purposes is a per se violation of FERPA.
Similarly, the Children’s Online Privacy Protection Act (COPPA) requires "verifiable parental consent" for use of information related to children under the age of 13. That prohibition includes any form of online profiling. As Mitrano points out, Google prefers to beg forgiveness after than to ask for permission before. Google Apps for Education (GAFE) is used by more than 40 million students and teachers around the world, according to Mitrano, and Google Chromebooks will soon account for 50 percent of the computers in schools.
In a court filing from 2010 Google admitted that it mines data from GAFE emails, including those of students under the age of 13. At the same time, the company made it difficult for schools to determine what it was doing with student and teacher data, purposely obfuscating its practices in contract negotiations with the schools. For example, Google refused to include lawyers in the negotiations and continually redirected any question about data mining to the refer to "ads."
In April 2014, Google reported that it had ceased scanning student email accounts for the purpose of serving content-related ads. However, the company didn't state explicitly that it had stopped profiling students. Whether or not Google has violated the law by profiling students without their parents' "verifiable" consent, the company's educational operations are clearly deceptive. This isn't a big surprise, especially considering Google's statement in a motion filed in June 2013 related to a data-mining suit that “a person has no legitimate expectation of privacy in information… turned over to third parties.” Nothing deceptive about that statement. Immoral, unethical, potentially "evil"? Yes. Deceptive? No.
--------------------------------------------------------------
Supreme Court to determine whether data collectors are subject to FCRA
Suppose an online people directory lists inaccurate information about you. You sue the company for violating the Fair Credit Reporting Act, but the court rules that you lack Article III standing because you can't show an actual injury as a result of the inaccuracy. You claim the mistakes cost you a chance at a job when you were unemployed because the directory stated incorrectly that you were already employed.
Do you have standing to sue? Some federal courts have ruled yes, others have said no. Now the U.S. Supreme Court has agreed to hear the case of Spokeo Inc. v. Robins, Case Number 13-1339. The U.S. Court of Appeals for the Ninth Circuit reversed the dismissal by the U.S. District Court for the Central District of California for plaintiff's lack of Article III standing. The question is whether the defendant's "willful" violation of the FCRA is sufficient to confer Article III standing. In its petition to the Supreme Court, Spokeo pointed out that several other federal statutes include both private rights of action and statutory damages, including the Telephone Consumer Protection Act, Truth in Lending Act, Fair Debt Collection Practices Act, and Electronic Funds Transfer Act.
As Ashley B. Guffey of King & Spalding writes in an April 27, 2015, article on JD Supra Business Advisor, the case has widespread implications for actions related to data breaches and other privacy matters, for which it is often difficult to prove actual damages. In a class-action suit, each violation of the FCRA could be punishable by a fine of $1,000. For a service the size of Spokeo, loss of such a case could put the company out of business.
I was all set to write about Google's new extension for the Chrome browser that defends against phishing attacks by warning you when you enter your Google password at a non-Google site. Password Alert detects your password being entered on a potentially bogus site and pops up a warning that your password may have been compromised, so click the provided link to change it. The plug-in is described in an April 29, 2015, post on the Google Blog.
Before I could utter, "Bully for Google!" I came across an April 26, 2015, article on Medium.com by Tracy Mitrano that reports on Google's practice of creating profiles of children who use the company's services at school. The Family Educational Rights and Privacy Act (FERPA) requires that vendors act as "school officials" in protecting students' education records. This prohibits vendors from using and/or reselling education records for commercial purposes.
The U.S. Department of Education's Family Compliance Privacy Office has ruled that schools remain responsible for the protection of education records even after they have outsourced management of the records to a third party. The office has also ruled that any data mining of education records for commercial purposes is a per se violation of FERPA.
Similarly, the Children’s Online Privacy Protection Act (COPPA) requires "verifiable parental consent" for use of information related to children under the age of 13. That prohibition includes any form of online profiling. As Mitrano points out, Google prefers to beg forgiveness after than to ask for permission before. Google Apps for Education (GAFE) is used by more than 40 million students and teachers around the world, according to Mitrano, and Google Chromebooks will soon account for 50 percent of the computers in schools.
In a court filing from 2010 Google admitted that it mines data from GAFE emails, including those of students under the age of 13. At the same time, the company made it difficult for schools to determine what it was doing with student and teacher data, purposely obfuscating its practices in contract negotiations with the schools. For example, Google refused to include lawyers in the negotiations and continually redirected any question about data mining to the refer to "ads."
In April 2014, Google reported that it had ceased scanning student email accounts for the purpose of serving content-related ads. However, the company didn't state explicitly that it had stopped profiling students. Whether or not Google has violated the law by profiling students without their parents' "verifiable" consent, the company's educational operations are clearly deceptive. This isn't a big surprise, especially considering Google's statement in a motion filed in June 2013 related to a data-mining suit that “a person has no legitimate expectation of privacy in information… turned over to third parties.” Nothing deceptive about that statement. Immoral, unethical, potentially "evil"? Yes. Deceptive? No.
--------------------------------------------------------------
Supreme Court to determine whether data collectors are subject to FCRA
Suppose an online people directory lists inaccurate information about you. You sue the company for violating the Fair Credit Reporting Act, but the court rules that you lack Article III standing because you can't show an actual injury as a result of the inaccuracy. You claim the mistakes cost you a chance at a job when you were unemployed because the directory stated incorrectly that you were already employed.
Do you have standing to sue? Some federal courts have ruled yes, others have said no. Now the U.S. Supreme Court has agreed to hear the case of Spokeo Inc. v. Robins, Case Number 13-1339. The U.S. Court of Appeals for the Ninth Circuit reversed the dismissal by the U.S. District Court for the Central District of California for plaintiff's lack of Article III standing. The question is whether the defendant's "willful" violation of the FCRA is sufficient to confer Article III standing. In its petition to the Supreme Court, Spokeo pointed out that several other federal statutes include both private rights of action and statutory damages, including the Telephone Consumer Protection Act, Truth in Lending Act, Fair Debt Collection Practices Act, and Electronic Funds Transfer Act.
As Ashley B. Guffey of King & Spalding writes in an April 27, 2015, article on JD Supra Business Advisor, the case has widespread implications for actions related to data breaches and other privacy matters, for which it is often difficult to prove actual damages. In a class-action suit, each violation of the FCRA could be punishable by a fine of $1,000. For a service the size of Spokeo, loss of such a case could put the company out of business.
April 28, 2015: The case against web encryption, Title II designation for ISPs

Encryption is anything but a security panacea, and regulation of the Internet could do more harm than good. Then again....
Tech shorts for April 28, 2015: Web ads are indistinguishable from spyware, and innovation comes to web searching (finally!)
Web ads and spyware are now synonymous
There's a delightful new euphemism popping up all over tech news sites: "potentially unwanted programs," also known as "potentially unwanted applications," or PUAs. Many of these programs sneak onto your PC or device as part of some other download. Nearly all of them record your activities and report back to their creators -- usually ad networks that use the information to pitch their products and services to you, among other money-making purposes.
Some PUAs also replace the ads that appear on the websites you visit with their own ads. In an April 19, 2015, article, TechCrunch's John Biggs describes one such program, WeLikeTheWeb's WebSiteRecommendation plug-in for Firefox and Google Chrome browsers. A close examination of the program's code reveals that it's siphoning off the few pennies sites make when they refer their visitors to other sites -- usually by clicking an ad.
As Biggs points out, the online advertisers who promulgate this and other types of spyware are spending a ton of money lobbying Congress against prohibiting or otherwise regulating their nefarious operations. This kind of snooping and behind-the-scenes manipulation is ubiquitous on the web. Be very, very careful about the programs you download. Many of the vendors behind the programs are doing some nasty things behind your back -- and making bank vaults full of money as a result.
---------------------------------------------------------------
A new search technology debuts. Should Google be worried?
It's unthinkable: Google no longer the King of Search? Couldn't happen.
Until it does. I'm not saying the Memex search technology released as open source recently by the Defense Advanced Research Projects Agency is going to put Google out of business anytime soon -- or ever. But Memex does offer something that has been missing in the web search industry for many years: innovation.
Forbes' Thomas Fox-Brewster writes in an April 17, 2015, article that Memex is used by law enforcement agencies around the world to track down criminals operating on the "dark web." Three organizations have created the TellFinder and DIG front ends for Memex-based searches: Uncharted Software, the University of Southern California, and Next Century Corp. Fox-Brewster describes several other Memex-related research projects, including ArrayFire, Diffeo, and Hyperion Gray.
Something tells me nobody in the Googleplex is losing any sleep over Memex. Yet.
There's a delightful new euphemism popping up all over tech news sites: "potentially unwanted programs," also known as "potentially unwanted applications," or PUAs. Many of these programs sneak onto your PC or device as part of some other download. Nearly all of them record your activities and report back to their creators -- usually ad networks that use the information to pitch their products and services to you, among other money-making purposes.
Some PUAs also replace the ads that appear on the websites you visit with their own ads. In an April 19, 2015, article, TechCrunch's John Biggs describes one such program, WeLikeTheWeb's WebSiteRecommendation plug-in for Firefox and Google Chrome browsers. A close examination of the program's code reveals that it's siphoning off the few pennies sites make when they refer their visitors to other sites -- usually by clicking an ad.
As Biggs points out, the online advertisers who promulgate this and other types of spyware are spending a ton of money lobbying Congress against prohibiting or otherwise regulating their nefarious operations. This kind of snooping and behind-the-scenes manipulation is ubiquitous on the web. Be very, very careful about the programs you download. Many of the vendors behind the programs are doing some nasty things behind your back -- and making bank vaults full of money as a result.
---------------------------------------------------------------
A new search technology debuts. Should Google be worried?
It's unthinkable: Google no longer the King of Search? Couldn't happen.
Until it does. I'm not saying the Memex search technology released as open source recently by the Defense Advanced Research Projects Agency is going to put Google out of business anytime soon -- or ever. But Memex does offer something that has been missing in the web search industry for many years: innovation.
Forbes' Thomas Fox-Brewster writes in an April 17, 2015, article that Memex is used by law enforcement agencies around the world to track down criminals operating on the "dark web." Three organizations have created the TellFinder and DIG front ends for Memex-based searches: Uncharted Software, the University of Southern California, and Next Century Corp. Fox-Brewster describes several other Memex-related research projects, including ArrayFire, Diffeo, and Hyperion Gray.
Something tells me nobody in the Googleplex is losing any sleep over Memex. Yet.
Legal shorts for April 28, 2015: Post-breach research protected from discovery, and a trade-secrets battle over betting machines
Cybersecurity research falls under attorney-client, work product protections
A company is hit by hackers and suffers a data breach. It hires two cybersecurity firms to investigate the matter. The company is later sued by a credit-card company, which seeks the results of the cybersecurity firms' research as part of discovery. Does the plaintiff credit-card company get the information from the defendant breach victim?
The U.S. District Court for the Middle District of Tennessee ruled recently in Genesco, Inc. v. Visa U.S.A., Inc. that the cybersecurity firms' research is protected by both the attorney-client privilege and the work-product doctrine. Shea Gordon Leitch, Antony Kim, and Aravind Swaminathan of Orrick, Herrington, and Sutcliffe LLP write about the decision in an April 24, 2015, article on the JD Supra Business Advisor site.
The authors point out that the court's ruling signals the key role legal counsel -- whether in-house or outside -- takes in the investigation of data breaches. By protecting the information collected by security experts on behalf of the potential plaintiffs, the legal counsel provides their corporate clients with a "safe place" to discuss the implications of the breach for the company, its customers, and its business partners.
---------------------------------------------------------
Shenanigans in 'historical' horse-race betting games
I bet you didn't know you can bet on horse races that have already been run. (Makes me wish I had saved all those old Racing Forms.) There's a company called AmTote International that sells betting machines to race tracks and other customers that let people place bets on live and historical horse races.
According to an April 24, 2015, article on the JD Supra Business Advisor site written by Mark Mermelstein and Robert Uriarte of Orrick, Kentucky Downs swapped out its AmTote betting machines in April 2015 for models from competitor Encore Gaming. AmTote sued Kentucky Downs, three of the track's high-ranking employees, and Encore Gaming, alleging misappropriation of AmTote's trade secrets.
AmTote hopes to win an injunction against the defendants under the "inevitable disclosure" doctrine. That doctrine avers that the defendants had no choice but to rely on information it gleaned from using the AmTote machines, which the track had been using since 2011. The inherent similarities of the betting machines from the two companies plays in AmTote's favor, according to the authors.
While the case will likely turn on whether the betting machines' diagnostic reports and other components qualify as trade secrets, what astonishes me is that somebody is making money from bets placed on races that were run years ago. The only reason I bring up the case here is because it gives me an opportunity to wish the entrants in this Saturday's 141st running of the Kentucky Derby the best of racing luck.
Just don't ask me who I've got in the race. I think my pick from last year's race is still circling the Churchill Downs track.
A company is hit by hackers and suffers a data breach. It hires two cybersecurity firms to investigate the matter. The company is later sued by a credit-card company, which seeks the results of the cybersecurity firms' research as part of discovery. Does the plaintiff credit-card company get the information from the defendant breach victim?
The U.S. District Court for the Middle District of Tennessee ruled recently in Genesco, Inc. v. Visa U.S.A., Inc. that the cybersecurity firms' research is protected by both the attorney-client privilege and the work-product doctrine. Shea Gordon Leitch, Antony Kim, and Aravind Swaminathan of Orrick, Herrington, and Sutcliffe LLP write about the decision in an April 24, 2015, article on the JD Supra Business Advisor site.
The authors point out that the court's ruling signals the key role legal counsel -- whether in-house or outside -- takes in the investigation of data breaches. By protecting the information collected by security experts on behalf of the potential plaintiffs, the legal counsel provides their corporate clients with a "safe place" to discuss the implications of the breach for the company, its customers, and its business partners.
---------------------------------------------------------
Shenanigans in 'historical' horse-race betting games
I bet you didn't know you can bet on horse races that have already been run. (Makes me wish I had saved all those old Racing Forms.) There's a company called AmTote International that sells betting machines to race tracks and other customers that let people place bets on live and historical horse races.
According to an April 24, 2015, article on the JD Supra Business Advisor site written by Mark Mermelstein and Robert Uriarte of Orrick, Kentucky Downs swapped out its AmTote betting machines in April 2015 for models from competitor Encore Gaming. AmTote sued Kentucky Downs, three of the track's high-ranking employees, and Encore Gaming, alleging misappropriation of AmTote's trade secrets.
AmTote hopes to win an injunction against the defendants under the "inevitable disclosure" doctrine. That doctrine avers that the defendants had no choice but to rely on information it gleaned from using the AmTote machines, which the track had been using since 2011. The inherent similarities of the betting machines from the two companies plays in AmTote's favor, according to the authors.
While the case will likely turn on whether the betting machines' diagnostic reports and other components qualify as trade secrets, what astonishes me is that somebody is making money from bets placed on races that were run years ago. The only reason I bring up the case here is because it gives me an opportunity to wish the entrants in this Saturday's 141st running of the Kentucky Derby the best of racing luck.
Just don't ask me who I've got in the race. I think my pick from last year's race is still circling the Churchill Downs track.
April 21, 2015: More examples of judges clueless about technology... and one that gets it

Recent court decisions show the disconnect between the way people use technology, and the way laws are misapplied against their interests.
April 21, 2015 Tech shorts: A language-translation browser extension, two new ways to protect data, and a documentary that helps you track the trackers
Learn a new language while you browse
Sometimes I think I'm engaged in the world's most-protracted language-learning program. I studied Spanish in high school, then moved on to other languages in college as I earned my undergrad degree in Linguistics. But off and on through the years I have returned to learning Spanish, primarily through a CD-based language-instruction program. (Secondarily through regular visits to our wonderful taquerias here in Santa Rosa.)
Now I can brush up on my dusty, rusty Spanish while I browse. The Readlang extension for Google's Chrome browser and its accompanying website translate words and phrases in dozens of languages. I'm using the Chrome extension, which places a green "R" icon in the top-right corner of the window. Click it to open a translation bar across the top of the screen.
Once the translation bar is enabled, words on the page are highlighted as you mouse over them. Choose a word or phrase to see the translation. (Note that translating phrases requires signing into a Google account or creating an email account on the Readlang site.)
The free version offers unlimited translations of single words and translations of up to 10 phrases each day. Unlimited phrase translations cost $24 per year.
----------------------------------------------------------------
Two new methods for protecting data: One hides it, the other tracks breaches in near-real-time
Encryption: It's the wave of the future, the wave of the future, the wave of the future, the wave of the future....
With apologies to Martin Scorsese's fictionalized version of Howard Hughes in "The Aviator," allow me to repeat myself over and over by reiteratingly saying the same thing I just said time and again. Last week's Weekly looked at the prospect of end-to-end encryption being offered on the web. A company called Ionic Security has developed software that encrypts all of an organization's data, all the time, except when the specific file is opened by an authorized user on an authorized computer or device. MIT Technology Review's Tom Simonite describes the technology in an April 14, 2015, article.
The company claims its product allows you to decrypt only some portions of a document or file, leaving other parts that the user isn't privy to encrypted. Simonite points to some of the technology's downsides: It requires an Internet connection, so you can't view files offline; the connection has to be authorized beforehand, so no ad-hoc network access is possible; and the encryption system itself could be hacked.
That's where another recent security innovation comes into play. A company called Tanium has created software that can show the status of every Internet connection on a network almost instantaneously. Forbes' Brian Solomon writes about the company in an April 15, 2015, article.
Tanium is based on what Solomon calls a new type of peer-to-peer network in which each computer/node communicates with its neighbor to pass information along a chain that leads to the central monitoring server. Network status reports that previously took hours or days to complete can now be generated in a few seconds, according Solomon. The goal is for network managers to be notified within seconds of any potential data breach. The quicker they can respond, the less damage an attacker can inflict on their networks.
The company is working to scale up to support the largest enterprise networks. Its current customer list includes Visa, Amazon, Best Buy, Nasdaq, and the U.S. Department of Defense. It also benefits from some very deep-pocket investors, including Marc Andreessen and Ben Horowitz.
It appears companies of all types and sizes are getting serious about security -- and not a moment too soon.
---------------------------------------------------------------
An interactive look at the web's many trackers
You know your web activities are tracked and recorded, and for the most part, you don't care. But do you really know what's being tracked, who's doing the tracking, and what they're doing with the information they collect about you?
An "online interactive documentary" entitled Do Not Track debuted recently at the Tribeca Film Festival New York, as Forbes' Joseph Steinberg describes in an April 16, 2015, article. Creator and director Brett Gaylor, who previously worked for the Mozilla Foundation, intends the series to educate web users about the dangers of being tracked, and about how they can limit the tracking.
The problem is, most anti-tracking techniques are difficult to implement and ultimately ineffective. For example, the "do not track" option in popular browsers is voluntary: sites can ignore the setting if they wish and track you all they want. Also, methods such as device fingerprinting render other tracker-blocking approaches all but useless.
The best way to protect your privacy online, along with blocking ads and third-party cookies, is simply to refrain from sharing personal information via social networks and other web services. You'll still be tracked, but at least you can limit what the trackers know about you.
Sometimes I think I'm engaged in the world's most-protracted language-learning program. I studied Spanish in high school, then moved on to other languages in college as I earned my undergrad degree in Linguistics. But off and on through the years I have returned to learning Spanish, primarily through a CD-based language-instruction program. (Secondarily through regular visits to our wonderful taquerias here in Santa Rosa.)
Now I can brush up on my dusty, rusty Spanish while I browse. The Readlang extension for Google's Chrome browser and its accompanying website translate words and phrases in dozens of languages. I'm using the Chrome extension, which places a green "R" icon in the top-right corner of the window. Click it to open a translation bar across the top of the screen.
Once the translation bar is enabled, words on the page are highlighted as you mouse over them. Choose a word or phrase to see the translation. (Note that translating phrases requires signing into a Google account or creating an email account on the Readlang site.)
The free version offers unlimited translations of single words and translations of up to 10 phrases each day. Unlimited phrase translations cost $24 per year.
----------------------------------------------------------------
Two new methods for protecting data: One hides it, the other tracks breaches in near-real-time
Encryption: It's the wave of the future, the wave of the future, the wave of the future, the wave of the future....
With apologies to Martin Scorsese's fictionalized version of Howard Hughes in "The Aviator," allow me to repeat myself over and over by reiteratingly saying the same thing I just said time and again. Last week's Weekly looked at the prospect of end-to-end encryption being offered on the web. A company called Ionic Security has developed software that encrypts all of an organization's data, all the time, except when the specific file is opened by an authorized user on an authorized computer or device. MIT Technology Review's Tom Simonite describes the technology in an April 14, 2015, article.
The company claims its product allows you to decrypt only some portions of a document or file, leaving other parts that the user isn't privy to encrypted. Simonite points to some of the technology's downsides: It requires an Internet connection, so you can't view files offline; the connection has to be authorized beforehand, so no ad-hoc network access is possible; and the encryption system itself could be hacked.
That's where another recent security innovation comes into play. A company called Tanium has created software that can show the status of every Internet connection on a network almost instantaneously. Forbes' Brian Solomon writes about the company in an April 15, 2015, article.
Tanium is based on what Solomon calls a new type of peer-to-peer network in which each computer/node communicates with its neighbor to pass information along a chain that leads to the central monitoring server. Network status reports that previously took hours or days to complete can now be generated in a few seconds, according Solomon. The goal is for network managers to be notified within seconds of any potential data breach. The quicker they can respond, the less damage an attacker can inflict on their networks.
The company is working to scale up to support the largest enterprise networks. Its current customer list includes Visa, Amazon, Best Buy, Nasdaq, and the U.S. Department of Defense. It also benefits from some very deep-pocket investors, including Marc Andreessen and Ben Horowitz.
It appears companies of all types and sizes are getting serious about security -- and not a moment too soon.
---------------------------------------------------------------
An interactive look at the web's many trackers
You know your web activities are tracked and recorded, and for the most part, you don't care. But do you really know what's being tracked, who's doing the tracking, and what they're doing with the information they collect about you?
An "online interactive documentary" entitled Do Not Track debuted recently at the Tribeca Film Festival New York, as Forbes' Joseph Steinberg describes in an April 16, 2015, article. Creator and director Brett Gaylor, who previously worked for the Mozilla Foundation, intends the series to educate web users about the dangers of being tracked, and about how they can limit the tracking.
The problem is, most anti-tracking techniques are difficult to implement and ultimately ineffective. For example, the "do not track" option in popular browsers is voluntary: sites can ignore the setting if they wish and track you all they want. Also, methods such as device fingerprinting render other tracker-blocking approaches all but useless.
The best way to protect your privacy online, along with blocking ads and third-party cookies, is simply to refrain from sharing personal information via social networks and other web services. You'll still be tracked, but at least you can limit what the trackers know about you.
April 14, 2015: Should all web traffic be encrypted?

Attempts are underway to implement end-to-end encryption on the web, but the prospect has some government security officials crying "foul."
April 7, 2015: More reasons why you need to block web ads

Not only are the ads on web sites annoying, they could infect your computer or device with malware. The ad model also perpetuates centralized control of the web by a handful of ginormous services.
Tech shorts for April 7, 2015: How much is your Internet privacy worth to you? And a social network designed to help you cope
AT&T puts a price on your privacy
How much is your online privacy worth to you? If you're a customer of AT&T's GigaPower high-speed fiber-optic Internet service, maintaining your privacy will cost you $60 a month. The Motley Fool's Daniel B. Kline writes in an April 5, 2015, article that GigaPower's rates start at an affordable $70 a month. However, at that price customers have to opt into AT&T's "Internet Preferences" program.
Internet Preferences gives AT&T permission to observe your browsing, serve up ads based on the sites you visit, send you email offers, and even have junk mail delivered to your house. You can opt out of the program by paying an extra $29 a month, but as Kline points out, when you get your phone and television service via GigaPower, staying private will cost you $60 a month. That doesn't even include having to pay the installation and modem fees that are waived for Internet Preferences participants.
As Kline states, opting out of such tracking should not require a "penalty fee." AT&T touts the $70-a-month rate in ads comparing its fiber-optic home service with its primary competitor, Google Fiber, even though Google's service doesn't entail anything like GigaPower's level of tracking. (Note that Google Fiber is attempting to make TV ads as targeted as their web counterparts, as MediaPost's Brian Wieser writes in a March 27, 2015, article.)
--------------------------------------------------------------
This social network wants to help you stop worrying so much
When he first started learning how to program, MIT researcher Rob Morris relied on sites such as the Stack Overflow online forum for help in solving the problems he encountered. That's where he got the notion that if a crowd of programmers could help him figure out code glitches, why couldn't a crowd of people help others figure out glitches in their own thought processes?
Morris was motivated to create a tool called Panoply that "crowdsources treatment for anxiety and depression," as Mother Jones' Rebecca Cohen writes in an April 3, 2015, article. The tool is currently called Koko and is available only by invitation, although prospective users can sign up for a chance to participate. The idea is to help people break the irrational thought patterns that distort their perception of the situations they encounter.
For example, suppose someone just lost their job and they become convinced that they'll ever find another one. They describe their situation and how they feel about it on the Koko forum, and others help them reframe their predicament in a more rational way. Cohen points out that the effectiveness of the approach has been confirmed by a study in the Journal of Internet Medical Research. The study found that people who used the service for at least 25 minutes a week for three weeks were "significantly less depressed and better at cognitive reappraisal" than people who spent three weeks engaged in a typical treatment for depression, expressive writing exercises.
Morris states that while the study focused on depression, he considers Panoply more of a stress-reduction application, in part because of the stigma of the word "depression." It's really just another fitness app, he claims, one that anyone who's fretting over a situation can benefit from using. Crowdsourcing emotional well-being sounds to me like a healthy use of the Internet, with the caveat that no one should expect any miracle cures. Sometimes there's no substitute for the personal attention of trained healthcare professionals.
How much is your online privacy worth to you? If you're a customer of AT&T's GigaPower high-speed fiber-optic Internet service, maintaining your privacy will cost you $60 a month. The Motley Fool's Daniel B. Kline writes in an April 5, 2015, article that GigaPower's rates start at an affordable $70 a month. However, at that price customers have to opt into AT&T's "Internet Preferences" program.
Internet Preferences gives AT&T permission to observe your browsing, serve up ads based on the sites you visit, send you email offers, and even have junk mail delivered to your house. You can opt out of the program by paying an extra $29 a month, but as Kline points out, when you get your phone and television service via GigaPower, staying private will cost you $60 a month. That doesn't even include having to pay the installation and modem fees that are waived for Internet Preferences participants.
As Kline states, opting out of such tracking should not require a "penalty fee." AT&T touts the $70-a-month rate in ads comparing its fiber-optic home service with its primary competitor, Google Fiber, even though Google's service doesn't entail anything like GigaPower's level of tracking. (Note that Google Fiber is attempting to make TV ads as targeted as their web counterparts, as MediaPost's Brian Wieser writes in a March 27, 2015, article.)
--------------------------------------------------------------
This social network wants to help you stop worrying so much
When he first started learning how to program, MIT researcher Rob Morris relied on sites such as the Stack Overflow online forum for help in solving the problems he encountered. That's where he got the notion that if a crowd of programmers could help him figure out code glitches, why couldn't a crowd of people help others figure out glitches in their own thought processes?
Morris was motivated to create a tool called Panoply that "crowdsources treatment for anxiety and depression," as Mother Jones' Rebecca Cohen writes in an April 3, 2015, article. The tool is currently called Koko and is available only by invitation, although prospective users can sign up for a chance to participate. The idea is to help people break the irrational thought patterns that distort their perception of the situations they encounter.
For example, suppose someone just lost their job and they become convinced that they'll ever find another one. They describe their situation and how they feel about it on the Koko forum, and others help them reframe their predicament in a more rational way. Cohen points out that the effectiveness of the approach has been confirmed by a study in the Journal of Internet Medical Research. The study found that people who used the service for at least 25 minutes a week for three weeks were "significantly less depressed and better at cognitive reappraisal" than people who spent three weeks engaged in a typical treatment for depression, expressive writing exercises.
Morris states that while the study focused on depression, he considers Panoply more of a stress-reduction application, in part because of the stigma of the word "depression." It's really just another fitness app, he claims, one that anyone who's fretting over a situation can benefit from using. Crowdsourcing emotional well-being sounds to me like a healthy use of the Internet, with the caveat that no one should expect any miracle cures. Sometimes there's no substitute for the personal attention of trained healthcare professionals.
Legal shorts for April 7, 2015: The mosaic theory extends Fourth Amendment protections to web data, and an evidence-based approach to intellectual property rights
The mosaic theory: Why online searches fall under Fourth Amendment limitations
The legal system depends on analogies to adapt existing laws and regulations to new situations. It took decades for the courts to rule that telephone conversations were protected by Fourth Amendment search requirements: You need a warrant issued by a judge that states with particularity what it is you're searching for, where and when you're searching, and why you're searching for it.
Gabriel R. Schlabach states in Privacy in the Cloud: The Mosaic Theory and the Stored Communications Act that only a court order or administrative subpoena is required for the government to order companies to turn over to them the detailed customer records the companies have created. However, when you apply the mosaic theory to modern data collection methods, it's clear that extended surveillance violates a suspect's reasonable expectation of privacy even though each individual act of surveillance would not fall under the Fourth Amendment search protections.
Schlabach writes that "the government can analyze the information in the aggregate to infer private details about the suspect that no individual member of the public could reasonably discover by observing her for a short time." He proposes an amendment to the Stored Communications Act component of the Electronic Communications Privacy Act of 1986 that would incorporate the mosaic theory in the statute to require a warrant and probable cause for the government to request online content as well as "noncontent" metadata.
Schlabach's article appears in the Stanford Law Review, Vol. 67, pages 677-721.
-----------------------------------------------------------
Losing 'faith' in intellectual property protections
Why does the law protect intellectual property? In a paper entitled Faith-based Intellectual Property, Stanford Law Professor Mark A. Lemley posits that IP rights have always been justified by their utility: granting such rights will make the world a better place. However, this position is based only on faith rather than on evidence. Lemley argues that the scholars who promote IP rights have turned their back on evidence that would confirm or contradict this faith-based assumption of social value.
The main problem with faith-based IP is the inability of its supporters to entertain any possibility that they could be wrong. The government allows the holders of IP rights to prevent use of the property by anyone else. This restriction on the freedom of individuals is justified by the social purpose of encouraging innovation and creation. Lemley points out that in a market-based economy, regulation requires some cost-benefit justification.
Scientists have studied IP rights extensively: from who acquires them, to how they use them, to how they affect the stock market, among other aspects. The consensus of all this research is that it remains uncertain whether patents, copyrights, and other IP have "a net positive effect on innovation," as researcher Lisa Ouellette states. To summarize Lemley's conclusion: It's complicated.
Many people have a strong vested interest in the IP status quo, and in the absence of any evidence in favor of or against our current approach to IP rights, it may make sense to continue things as they are. But "it's always been this way" doesn't cut it as a legitimate reason to restrict the freedom of individuals to make productive use of ideas that others may have thought of first. It does everyone a disservice to ignore data because it disagrees with your viewpoint, which Lemley argues some proponents of IP rights are doing. This retreat from evidence is what Lemley refers to as faith-based IP, and like a religion, it is a matter of belief among its proponents -- no evidence required.
To restate the obvious, intellectual property is not like real property, so the entitlement of property owners isn't automatically extendable by common-law traditions to IP. Lemley argues that it may make more sense to convey IP rights to the party who can make best use of the property rather than to the party who created it first. IP rights limit freedoms, particularly freedom of speech. It is imperative that the social benefit justify such freedom restrictions. How do we know whether this is so unless we examine the evidence? Otherwise we're making policy based on instinct.
Lemley's paper appears in the UCLA Law Review, Vol. 62, Issue 5. It was published on March 30, 2015.
The legal system depends on analogies to adapt existing laws and regulations to new situations. It took decades for the courts to rule that telephone conversations were protected by Fourth Amendment search requirements: You need a warrant issued by a judge that states with particularity what it is you're searching for, where and when you're searching, and why you're searching for it.
Gabriel R. Schlabach states in Privacy in the Cloud: The Mosaic Theory and the Stored Communications Act that only a court order or administrative subpoena is required for the government to order companies to turn over to them the detailed customer records the companies have created. However, when you apply the mosaic theory to modern data collection methods, it's clear that extended surveillance violates a suspect's reasonable expectation of privacy even though each individual act of surveillance would not fall under the Fourth Amendment search protections.
Schlabach writes that "the government can analyze the information in the aggregate to infer private details about the suspect that no individual member of the public could reasonably discover by observing her for a short time." He proposes an amendment to the Stored Communications Act component of the Electronic Communications Privacy Act of 1986 that would incorporate the mosaic theory in the statute to require a warrant and probable cause for the government to request online content as well as "noncontent" metadata.
Schlabach's article appears in the Stanford Law Review, Vol. 67, pages 677-721.
-----------------------------------------------------------
Losing 'faith' in intellectual property protections
Why does the law protect intellectual property? In a paper entitled Faith-based Intellectual Property, Stanford Law Professor Mark A. Lemley posits that IP rights have always been justified by their utility: granting such rights will make the world a better place. However, this position is based only on faith rather than on evidence. Lemley argues that the scholars who promote IP rights have turned their back on evidence that would confirm or contradict this faith-based assumption of social value.
The main problem with faith-based IP is the inability of its supporters to entertain any possibility that they could be wrong. The government allows the holders of IP rights to prevent use of the property by anyone else. This restriction on the freedom of individuals is justified by the social purpose of encouraging innovation and creation. Lemley points out that in a market-based economy, regulation requires some cost-benefit justification.
Scientists have studied IP rights extensively: from who acquires them, to how they use them, to how they affect the stock market, among other aspects. The consensus of all this research is that it remains uncertain whether patents, copyrights, and other IP have "a net positive effect on innovation," as researcher Lisa Ouellette states. To summarize Lemley's conclusion: It's complicated.
Many people have a strong vested interest in the IP status quo, and in the absence of any evidence in favor of or against our current approach to IP rights, it may make sense to continue things as they are. But "it's always been this way" doesn't cut it as a legitimate reason to restrict the freedom of individuals to make productive use of ideas that others may have thought of first. It does everyone a disservice to ignore data because it disagrees with your viewpoint, which Lemley argues some proponents of IP rights are doing. This retreat from evidence is what Lemley refers to as faith-based IP, and like a religion, it is a matter of belief among its proponents -- no evidence required.
To restate the obvious, intellectual property is not like real property, so the entitlement of property owners isn't automatically extendable by common-law traditions to IP. Lemley argues that it may make more sense to convey IP rights to the party who can make best use of the property rather than to the party who created it first. IP rights limit freedoms, particularly freedom of speech. It is imperative that the social benefit justify such freedom restrictions. How do we know whether this is so unless we examine the evidence? Otherwise we're making policy based on instinct.
Lemley's paper appears in the UCLA Law Review, Vol. 62, Issue 5. It was published on March 30, 2015.
March 31, 2015: Web 3.0 returns control of personal information to users

Encrypted peer-to-peer networks such as the Ethereum project promise to make privacy the default setting for all online information.
Legal shorts for March 31, 2015: No 'right' to be forgotten; no protections for your mobile viewing history; and the impact of common-carrier ISPs
No such thing as a 'right to be forgotten'
Not long ago, a resident of Spain wanted Google to remove links to information related to his past financial troubles. The European court ruled that Google has to allow people to request similar removals of disparaging but accurate information. Now people are talking about extending this right to U.S. citizens.
To which I say "Phooey!"
First, Google merely removes links to the sources of information you want to erase from the Internet. The information's still there, and it could be discovered -- at least in theory -- via other methods.
But more importantly, you can't rewrite history. That was what Big Brother was doing in George Orwell's 1984, right? "If you control the past, you control the present." What gives you the right to attempt to control the past?
This sentiment was the consensus of attendees at a recent debate in New York City on whether the U.S. should follow the lead of the European Court of Justice in allowing individuals to demand negative (but accurate) information about them be removed from search results. Fortune's Jeff John Roberts reports on the event in a March 12, 2015, article.
The best defense against such disparaging information is to counter it with positive information. With time and effort, you'll reclaim your reputation. (Of course, if the disparaging information is untrue and damaging, you have a duty to seek reparations -- but not from Google. Look for your remedy from the source of the defaming information.)
------------------------------------------------------------
Web video service isn't liable for sharing customers' viewing history without permission
So this company sells a customer's 64-digit Android phone ID and video-viewing history without permission to a targeted ad network. Then the ad network ties the ID to information from another source to determine the customer's name. The customer claims this is a violation of the Video Privacy Protection Act of 1988, which was enacted in the wake of Judge Robert Bork's failed nomination to the U.S. Supreme Court. During Bork's nomination process, a newspaper acquired the nominee's rental history from a video store (remember those?)
The U.S. District Court dismissed the suit with prejudice for failure to state a claim. (Ellis v. The Cartoon Network, Inc., U.S. Dist. LEXIS 143078, at *9 (N.D. Ga. Oct. 8, 2014)). On March 2, 2015, defendant Cartoon Network filed its response brief requesting that the Eleventh Circuit Court of Appeals affirm the district court's dismissal, as Jessica Nwokacha writes in a March 25, 2015, post on the JD Supra Business Advisor site.
Mark Ellis, the plaintiff, points to the statute's interpretation of personally identifiable information as any where "the recipient of a disclosure understands to whom the information refers." Ellis points out that information such as the Android ID is actually more identifying than a name because names are often shared by several people, whereas an Android ID is unique to an individual.
Nwokacha states that our mobile viewing histories become more valuable as our use of mobile phones increases. Depending on outdated statutes such as the Video Privacy Protection Act to prevent misuse of our mobile data is tantamount to having no protections at all.
-----------------------------------------------------------
Treating ISPs as common carriers will broaden the definition of 'personal info'
Once Internet services are subject to the restrictions of common carriers under the Section 222 of the Telecommunications Act of 1996 (47 U.S.C. § 222), the Android ID at issue in Ellis v. The Cartoon Network may qualify as "customer proprietary network information" under Section 222. That would limit how services can use, disclose, and share such personal information, as Mark Brennan writes in a March 25, 2015, post on the Hogan Lovells site.
However, the FCC intends to give Internet services a pass on Section 222, claiming that the statute was intended for voice communications, so its definition of personal information doesn't apply to Internet services. The agency is expected to develop new rules applying Section 222 to information collected and stored on the Internet.
Until then, your mobile data is available to the highest bidder.
Not long ago, a resident of Spain wanted Google to remove links to information related to his past financial troubles. The European court ruled that Google has to allow people to request similar removals of disparaging but accurate information. Now people are talking about extending this right to U.S. citizens.
To which I say "Phooey!"
First, Google merely removes links to the sources of information you want to erase from the Internet. The information's still there, and it could be discovered -- at least in theory -- via other methods.
But more importantly, you can't rewrite history. That was what Big Brother was doing in George Orwell's 1984, right? "If you control the past, you control the present." What gives you the right to attempt to control the past?
This sentiment was the consensus of attendees at a recent debate in New York City on whether the U.S. should follow the lead of the European Court of Justice in allowing individuals to demand negative (but accurate) information about them be removed from search results. Fortune's Jeff John Roberts reports on the event in a March 12, 2015, article.
The best defense against such disparaging information is to counter it with positive information. With time and effort, you'll reclaim your reputation. (Of course, if the disparaging information is untrue and damaging, you have a duty to seek reparations -- but not from Google. Look for your remedy from the source of the defaming information.)
------------------------------------------------------------
Web video service isn't liable for sharing customers' viewing history without permission
So this company sells a customer's 64-digit Android phone ID and video-viewing history without permission to a targeted ad network. Then the ad network ties the ID to information from another source to determine the customer's name. The customer claims this is a violation of the Video Privacy Protection Act of 1988, which was enacted in the wake of Judge Robert Bork's failed nomination to the U.S. Supreme Court. During Bork's nomination process, a newspaper acquired the nominee's rental history from a video store (remember those?)
The U.S. District Court dismissed the suit with prejudice for failure to state a claim. (Ellis v. The Cartoon Network, Inc., U.S. Dist. LEXIS 143078, at *9 (N.D. Ga. Oct. 8, 2014)). On March 2, 2015, defendant Cartoon Network filed its response brief requesting that the Eleventh Circuit Court of Appeals affirm the district court's dismissal, as Jessica Nwokacha writes in a March 25, 2015, post on the JD Supra Business Advisor site.
Mark Ellis, the plaintiff, points to the statute's interpretation of personally identifiable information as any where "the recipient of a disclosure understands to whom the information refers." Ellis points out that information such as the Android ID is actually more identifying than a name because names are often shared by several people, whereas an Android ID is unique to an individual.
Nwokacha states that our mobile viewing histories become more valuable as our use of mobile phones increases. Depending on outdated statutes such as the Video Privacy Protection Act to prevent misuse of our mobile data is tantamount to having no protections at all.
-----------------------------------------------------------
Treating ISPs as common carriers will broaden the definition of 'personal info'
Once Internet services are subject to the restrictions of common carriers under the Section 222 of the Telecommunications Act of 1996 (47 U.S.C. § 222), the Android ID at issue in Ellis v. The Cartoon Network may qualify as "customer proprietary network information" under Section 222. That would limit how services can use, disclose, and share such personal information, as Mark Brennan writes in a March 25, 2015, post on the Hogan Lovells site.
However, the FCC intends to give Internet services a pass on Section 222, claiming that the statute was intended for voice communications, so its definition of personal information doesn't apply to Internet services. The agency is expected to develop new rules applying Section 222 to information collected and stored on the Internet.
Until then, your mobile data is available to the highest bidder.
March 24, 2015: Passwords to get much-needed assistance -- from your body

Biometric authentication is on the horizon, promising to enhance rather than replace passwords as our ID-verification method of choice.
Sundries for March 24, 2015: Workplace phone etiquette,
fighting patent trolls, Target's legal victory against consumers
Eight ways to breach cell-phone etiquette at work
If you want to get ahead in the workaday world, you have to know how not to tick off your coworkers. One of the easiest ways to get on your officemates' bad side is to misuse your cell phone in your shared space.
In a March 23, 2015, article, Forbes' Kate Ashford lists the eight most common smart phone faux pas in the workplace. Ashford cites a Kessler International survey that found "untimely and inappropriate use of cell phones" is the number one employee etiquette breach.
According to an expert on office decorum, you risk alienating your coworkers if you check your phone during client meetings, you use your phone during networking events, you have your phone in view at work or during a business meal, you talk too loudly, you take personal calls in your cubicle, or you have an obnoxious ringtone.
Not on Ashford's list of inappropriate cell-phone behavior is absenting yourself to take a personal call during work hours; quietly playing games or otherwise recreating on the device; capturing unsuspecting coworkers in photographs, videos, or audio recordings; and blasting music through the headphones so loudly they can hear it two floors up. The safest course is to hide the existence of your phone from coworkers entirely.
"She had a cell phone? Who knew? But she's going to do great as our new CEO."
----------------------------------------------------------
How to beat a patent troll: Fight back with all you've got
So-called non-practicing entities are companies that own patents solely (or principally) for the purpose of exacting payments from other companies they accuse of infringing on the patents. The standard response to receiving a demand letter from so-called patent trolls is to pay them off to make the problem go away.
As a long-term solution to misuse of patents, this approach is the equivalent of trying to get rid of cockroaches by feeding them to death. Life360 CEO Chris Hulls took a different tack when a company called AGIS accused his firm of patent infringement. As Ars Technica's Joe Mullin explains in a March 23, 2015, post, Hulls took the offensive, calling out the law firm representing the plaintiff, open-sourcing the prior art it found on AGIS's patents, and refusing to settle at all costs.
Not only did Life360 win the case, Hulls has proposed his strategy as a blueprint for other companies facing threats from patent trolls. Step one is to "go nuclear" by using any legal means to discredit the plaintiff's claims. Step two is to share your information in defense of the charges with other potential defendants. Step three is to take a hard line and stick with it to the end.
Mullin notes that while AGIS doesn't fit the textbook definition of a patent troll because it has released a legitimate product, but Hulls points out that AGIS's behavior in the case was straight out of the patent-troll playbook. In particular, AGIS never competed directly with Life360.
Was AGIS a "bully" as Hulls claims, or simply an ordinary business living up to its fiduciary duty to maximize the profitability of its assets? The fact that AGIS lost the case indicates that maybe it didn't have the strongest case to begin with. There's also no indication about the validity of the patent at issue. Still, you can't argue with the positive results of Life360's take-no-prisoners response to AGIS's patent claims.
------------------------------------------------------------
Target's class-action data-breach settlement is a boon for the defendant
When Target agreed to create a $10 million cash fund to be paid to members of the class of consumers damaged by its massive data breach in late 2013, the company executives likely threw themselves a little celebration. Kevin McGinty explains in a March 23, 2015, post on the JD Supra Business Advisor site that the typical award in a class-action data-breach case not involving medical records is $1 or less per class member.
Why? Because it's difficult for class members to prove monetary damages directly related to the data breach. Considering that there were potentially 110 million class members in the Target suit, per-member awards may fall far short of the average in such cases.
Two other figures jump out of the proposed settlement agreement: $6.7 million (the amount the plaintiffs' lawyers will collect from the settlement), and $252 million (the overall cost to Target in responding to the breach). Not included in the settlement are claims against Target by the class of credit-card issuers, who are on the hook for the bogus charges that resulted from the retailer's massive data loss.
It can be argued that Target's customers don't have a claim against the company because few suffered any direct monetary damage due to the breach. However, no one can state unequivocally that consumers won't ultimately be the ones footing the bill for the multi-million-dollar loss, if only indirectly via higher credit-card and bank charges.
The lawyers did okay, as usual, so it's not all bad news (wink, wink).
If you want to get ahead in the workaday world, you have to know how not to tick off your coworkers. One of the easiest ways to get on your officemates' bad side is to misuse your cell phone in your shared space.
In a March 23, 2015, article, Forbes' Kate Ashford lists the eight most common smart phone faux pas in the workplace. Ashford cites a Kessler International survey that found "untimely and inappropriate use of cell phones" is the number one employee etiquette breach.
According to an expert on office decorum, you risk alienating your coworkers if you check your phone during client meetings, you use your phone during networking events, you have your phone in view at work or during a business meal, you talk too loudly, you take personal calls in your cubicle, or you have an obnoxious ringtone.
Not on Ashford's list of inappropriate cell-phone behavior is absenting yourself to take a personal call during work hours; quietly playing games or otherwise recreating on the device; capturing unsuspecting coworkers in photographs, videos, or audio recordings; and blasting music through the headphones so loudly they can hear it two floors up. The safest course is to hide the existence of your phone from coworkers entirely.
"She had a cell phone? Who knew? But she's going to do great as our new CEO."
----------------------------------------------------------
How to beat a patent troll: Fight back with all you've got
So-called non-practicing entities are companies that own patents solely (or principally) for the purpose of exacting payments from other companies they accuse of infringing on the patents. The standard response to receiving a demand letter from so-called patent trolls is to pay them off to make the problem go away.
As a long-term solution to misuse of patents, this approach is the equivalent of trying to get rid of cockroaches by feeding them to death. Life360 CEO Chris Hulls took a different tack when a company called AGIS accused his firm of patent infringement. As Ars Technica's Joe Mullin explains in a March 23, 2015, post, Hulls took the offensive, calling out the law firm representing the plaintiff, open-sourcing the prior art it found on AGIS's patents, and refusing to settle at all costs.
Not only did Life360 win the case, Hulls has proposed his strategy as a blueprint for other companies facing threats from patent trolls. Step one is to "go nuclear" by using any legal means to discredit the plaintiff's claims. Step two is to share your information in defense of the charges with other potential defendants. Step three is to take a hard line and stick with it to the end.
Mullin notes that while AGIS doesn't fit the textbook definition of a patent troll because it has released a legitimate product, but Hulls points out that AGIS's behavior in the case was straight out of the patent-troll playbook. In particular, AGIS never competed directly with Life360.
Was AGIS a "bully" as Hulls claims, or simply an ordinary business living up to its fiduciary duty to maximize the profitability of its assets? The fact that AGIS lost the case indicates that maybe it didn't have the strongest case to begin with. There's also no indication about the validity of the patent at issue. Still, you can't argue with the positive results of Life360's take-no-prisoners response to AGIS's patent claims.
------------------------------------------------------------
Target's class-action data-breach settlement is a boon for the defendant
When Target agreed to create a $10 million cash fund to be paid to members of the class of consumers damaged by its massive data breach in late 2013, the company executives likely threw themselves a little celebration. Kevin McGinty explains in a March 23, 2015, post on the JD Supra Business Advisor site that the typical award in a class-action data-breach case not involving medical records is $1 or less per class member.
Why? Because it's difficult for class members to prove monetary damages directly related to the data breach. Considering that there were potentially 110 million class members in the Target suit, per-member awards may fall far short of the average in such cases.
Two other figures jump out of the proposed settlement agreement: $6.7 million (the amount the plaintiffs' lawyers will collect from the settlement), and $252 million (the overall cost to Target in responding to the breach). Not included in the settlement are claims against Target by the class of credit-card issuers, who are on the hook for the bogus charges that resulted from the retailer's massive data loss.
It can be argued that Target's customers don't have a claim against the company because few suffered any direct monetary damage due to the breach. However, no one can state unequivocally that consumers won't ultimately be the ones footing the bill for the multi-million-dollar loss, if only indirectly via higher credit-card and bank charges.
The lawyers did okay, as usual, so it's not all bad news (wink, wink).
March 17, 2015: An unexpected visit from the Karma Police

A "whatza-matter-you, hey, things are not so bad" reality check about the tendency of dire predictions about the future to rarely if ever come true. Positively!
March 10, 2015: Three views of the future that are certain to curl your hair

The Uberization of work, a know-it-all personal agent that knows more about you than you know about yourself, and a world where the masses are "useless": It's a dystopian fielder's choice.
Tech shorts for March 10, 2015: Obama's flawed privacy proposal, custom iPhone alerts, bank-account monitoring, employee Facebook guidelines, and data-focused security
The fatal flaw in the Obama Administration's Privacy Bill of Rights
Last week's Weekly pointed out that the Consumer Privacy Bill of Rights proposed by the Obama Administration has little chance of being voted on, let alone enacted. In fact, the bill was proposed as a discussion draft, and as such it has succeeded in raising several important matters relating to our privacy rights.
As Center for Digital Democracy executive director Jeffrey Chester explains in a March 5, 2015, post on AlterNet, the proposal leaves control over the collection and management of our personal data to the companies that are doing the collecting. The big industry players would take the lead role in creating self-regulatory "codes of conduct" governing data collection and privacy.
The bill would also remove Federal Trade Commission oversight of companies collecting and maintaining our personal information. Even with the lack of any kind of true regulation in the bill, the Internet Association lobbying group representing Google, Facebook, Amazon, and other data-collecting companies oppose it -- and any other attempt by the government to encumber their data-collecting operations.
------------------------------------------------------------
Customize your iPhone alerts, monitor bank accounts for fraud attempts
Nonstop phone notifications can drive you bonkers. (I described how to silence them in a November 19, 2012, article on CNET.) A free iPhone app called Hooks lets you customize your notifications based on the triggers of your choice. Tech Crunch's Steve O'Hear offers a primer on using Hooks in a March 4, 2015, article.
Hooks presents you with a directory of 100 "channels" from which you can choose to be alerted about news, sports scores, weather, stock prices, travel information, even tweets and YouTube videos posted by specific people. Note that while the app is currently free, the developers may ultimately charge users to receive business-related alerts.
Of course, there are times when you definitely want to be notified. One of those times is when your bank account, or the account of a person you care for, has been targeted by fraudsters. For $5 a month, the EverSafe service monitors the bank account of your choice to detect potential fraudulent charges. The service doesn't block the transactions it identifies as possible scams, nor can it make any changes to the accounts it monitors.
What EverSafe can do is give you a heads-up about suspicious charges in time for you to take action to block or reverse them, if necessary. Lifehacker's Dave Greenbaum describes how EverSafe works in a March 7, 2015, post.
----------------------------------------------------------
Facebook guidelines for employers
The chances are pretty good your employees are using Facebook to discuss work-related matters. Nearly every company has devised guidelines for employee use of social media. How do you know whether your company's guidelines could run afoul of the National Labor Relations Act?
As Desiree Busching and Lauren Helen Leyden of Akin Gump Strauss Hauer & Feld LLP explain in a March 6, 2015, post on JD Supra Business Advisor, the National Labor Relations Board has ruled that certain common social-media policies violate the NLRA. These include prohibitions against employees posting comments related to their employers or coworkers, and overbroad definitions of what constitutes "confidential information."
In general, employees can't be prevented from discussing their "terms and conditions of employment." Also protected are complaints about workplace policies, and comments about disagreements with supervisors. The authors recommend that a company's social-media policy include specific examples of the type of information and conduct that is not allowed, and that it avoid any language that could be construed as infringing on employees' right to "engage in concerted activity."
-----------------------------------------------------------
Forget protecting the network. Focus on protecting the data
With the rise of mobile devices and ubiquitous connectivity, it has become nearly impossible to determine where an organization's network ends. This has rendered network-based security plans futile: you simply can't completely lock down any network.
As an alternative, security is now focusing on the data rather than the pathways to the data. Encrypting sensitive data is a more effective approach to preventing loss than trying to control access to the network the data is stored on. Secure Islands cofounder Yuval Eldar highlights a secondary benefit of a data-centric approach to security: it returns control over data access to IT departments. Eldar explains the benefits of data-level security in a March 5, 2015, article on Forbes.
Eldar distinguishes four categories of data in an organization: public, internal, confidential, and secret. Rather than allowing end users to categorize the information they're sending within and without the organization, IT departments would be charged with automating the classification by assigning it when and where the data is stored -- before it has been shared.
Automatic encryption of a company's sensitive information would also address the main source of data loss: theft of laptops and mobile phones. According to a survey of IT professionals conducted by Sungard Availability Services, employees leaving laptops and mobile phones unprotected is their biggest single problem. The survey results are discussed by Forbes' Asher DeMetz in a March 5, 2015, article.
The best way to prevent data loss in such situations is to encrypt the laptop's hard drive. Other preventive measures are to enforce strong passwords, freeze the affected employee's account, and use tracking software so you can alert law enforcement as to the stolen device's whereabouts.
Last week's Weekly pointed out that the Consumer Privacy Bill of Rights proposed by the Obama Administration has little chance of being voted on, let alone enacted. In fact, the bill was proposed as a discussion draft, and as such it has succeeded in raising several important matters relating to our privacy rights.
As Center for Digital Democracy executive director Jeffrey Chester explains in a March 5, 2015, post on AlterNet, the proposal leaves control over the collection and management of our personal data to the companies that are doing the collecting. The big industry players would take the lead role in creating self-regulatory "codes of conduct" governing data collection and privacy.
The bill would also remove Federal Trade Commission oversight of companies collecting and maintaining our personal information. Even with the lack of any kind of true regulation in the bill, the Internet Association lobbying group representing Google, Facebook, Amazon, and other data-collecting companies oppose it -- and any other attempt by the government to encumber their data-collecting operations.
------------------------------------------------------------
Customize your iPhone alerts, monitor bank accounts for fraud attempts
Nonstop phone notifications can drive you bonkers. (I described how to silence them in a November 19, 2012, article on CNET.) A free iPhone app called Hooks lets you customize your notifications based on the triggers of your choice. Tech Crunch's Steve O'Hear offers a primer on using Hooks in a March 4, 2015, article.
Hooks presents you with a directory of 100 "channels" from which you can choose to be alerted about news, sports scores, weather, stock prices, travel information, even tweets and YouTube videos posted by specific people. Note that while the app is currently free, the developers may ultimately charge users to receive business-related alerts.
Of course, there are times when you definitely want to be notified. One of those times is when your bank account, or the account of a person you care for, has been targeted by fraudsters. For $5 a month, the EverSafe service monitors the bank account of your choice to detect potential fraudulent charges. The service doesn't block the transactions it identifies as possible scams, nor can it make any changes to the accounts it monitors.
What EverSafe can do is give you a heads-up about suspicious charges in time for you to take action to block or reverse them, if necessary. Lifehacker's Dave Greenbaum describes how EverSafe works in a March 7, 2015, post.
----------------------------------------------------------
Facebook guidelines for employers
The chances are pretty good your employees are using Facebook to discuss work-related matters. Nearly every company has devised guidelines for employee use of social media. How do you know whether your company's guidelines could run afoul of the National Labor Relations Act?
As Desiree Busching and Lauren Helen Leyden of Akin Gump Strauss Hauer & Feld LLP explain in a March 6, 2015, post on JD Supra Business Advisor, the National Labor Relations Board has ruled that certain common social-media policies violate the NLRA. These include prohibitions against employees posting comments related to their employers or coworkers, and overbroad definitions of what constitutes "confidential information."
In general, employees can't be prevented from discussing their "terms and conditions of employment." Also protected are complaints about workplace policies, and comments about disagreements with supervisors. The authors recommend that a company's social-media policy include specific examples of the type of information and conduct that is not allowed, and that it avoid any language that could be construed as infringing on employees' right to "engage in concerted activity."
-----------------------------------------------------------
Forget protecting the network. Focus on protecting the data
With the rise of mobile devices and ubiquitous connectivity, it has become nearly impossible to determine where an organization's network ends. This has rendered network-based security plans futile: you simply can't completely lock down any network.
As an alternative, security is now focusing on the data rather than the pathways to the data. Encrypting sensitive data is a more effective approach to preventing loss than trying to control access to the network the data is stored on. Secure Islands cofounder Yuval Eldar highlights a secondary benefit of a data-centric approach to security: it returns control over data access to IT departments. Eldar explains the benefits of data-level security in a March 5, 2015, article on Forbes.
Eldar distinguishes four categories of data in an organization: public, internal, confidential, and secret. Rather than allowing end users to categorize the information they're sending within and without the organization, IT departments would be charged with automating the classification by assigning it when and where the data is stored -- before it has been shared.
Automatic encryption of a company's sensitive information would also address the main source of data loss: theft of laptops and mobile phones. According to a survey of IT professionals conducted by Sungard Availability Services, employees leaving laptops and mobile phones unprotected is their biggest single problem. The survey results are discussed by Forbes' Asher DeMetz in a March 5, 2015, article.
The best way to prevent data loss in such situations is to encrypt the laptop's hard drive. Other preventive measures are to enforce strong passwords, freeze the affected employee's account, and use tracking software so you can alert law enforcement as to the stolen device's whereabouts.
March 3, 2015: Privacy, Inc.: Welcome to the personal-information marketplace

Consumers can retain control over their personal information by entering into contracts with government agencies and businesses that stipulate how their personal-information property will be used, and what they receive in exchange for it.
February 24, 2015: The tricks of the malware trade: Don't take the bait!

Here are five simple actions you can take to minimize the chances of becoming a computer criminal's next victim.
Legal shorts for February 24, 2015: BlackShades bandit nabbed, a rising sea of debt, and local jails become debtors' prisons
Malware purveyor pleads guilty, faces jail time
One of the criminals behind the BlackShades malware construction kit has pleaded guilty in a federal court in Manhattan to distribution of malicious software. Reuters' Nate Raymond reports in a February 19, 2015, article that 24-year-old Swedish national Alex Yucel was reportedly the mastermind behind BlackShades, which was used to infect hundreds of thousands of computers worldwide.
As part of his plea deal, Yucel has agreed to waive his right to appeal if he receives a sentence of less than seven-and-a-quarter years in prison; his sentencing is scheduled for May 22. BlackShades software was sold for $40 and was used by criminals to control their victims' computers remotely, record keystrokes, steal personal information, and lock the computers until a ransom was paid.
BlackShades reportedly generated $350,000 in revenue for its creators, who were caught by a fake website created by the FBI for buying and selling stolen credit-card numbers. Yucel was arrested in Moldova in November 2013 and extradited to the U.S. to face trial.
Cybercrimes against property are on the rise, according to researchers, but exact numbers are difficult to come by because the FBI doesn't track online propery crime, credit-card fraud, or identity theft, according to researchers at the University of New Haven and the State University of New York at Albany. Their research into cybercrime underreporting is cited in a February 20, 2015, article on the Phys.org site.
Many cybercrimes are "handled" by the private-corporation victims rather than by the police. In fact, few such crimes are ever reported to law enforcement agencies. The researchers claim that more than half of the people who are victims of online fraud and data theft are never informed of the crimes. Companies are more interested in protecting their reputations, according to the researchers, who state that the dearth of information about cybercrimes makes fighting it more difficult.
--------------------------------------------------------
Worldwide debt rising right along with sea levels
Since 2007, the amount of money owed by everyone -- government, businesses, people -- has increased by $57 trillion, according to research reported by McKinley earlier this month. That's a 40.1 percent increase. As Neil Irwin of the New York Times points out in a February 5, 2015, article, financial institutions in the U.S. are actually less leveraged now than they were in 2007, but private debt in the U.S. economy is up 16 percent since 2007 to 233 percent of gross domestic product.
Kate Aronoff writes in a February 7, 2015, article on the Common Dreams site that according to Kingston University economist Steve Keen, any country whose private debt ratio exceeds 150 percent of GDP is vulnerable to financial calamity. (Keen was one of the few economists who predicted the 2008 financial crisis.) Japan's private debt ratio stands at 400 percent, the UK's at 350 percent, and China's at 217 percent.
Aronoff points out that the government's response to the 2008 crisis was to pump more money into the financial institutions whose carelessness precipitated the crash. In recent years, funding for public services has dried up, creating what the Guardian's Ross Ashcroft calls "backdoor privatization." Privatization cuts wages, which ultimately leads to increased debt.
----------------------------------------------------------
Are county jails becoming debtors' prisons?
Speaking of debt, a report issued earlier this month by the Vera Institute of Justice found that most of the people held in local and county jails in the U.S. are there for minor offenses for which they could be released if they could afford to pay the court-imposed costs. The New York Times' Timothy Williams discusses the report's findings in a February 11, 2015, article.
The good news is that programs are underway across the U.S. intended to reduce jail time for minor offenses. CNN's Sally Kohn reports in a February 23, 2015, article on the Smart Sentencing Act that has won bipartisan support in Congress but that has been stalled by U.S. Senator Chuck Grassley, R-Ia.
In addition to emphasizing prevention through employment and education, the reform efforts address the drug, alcohol, and mental-illness problems that afflict so many of the repeat offenders whose incarceration has become such a burden. While many of these programs have focused to date on state prisons, many jail inmates could benefit from the reforms as well.
One of the criminals behind the BlackShades malware construction kit has pleaded guilty in a federal court in Manhattan to distribution of malicious software. Reuters' Nate Raymond reports in a February 19, 2015, article that 24-year-old Swedish national Alex Yucel was reportedly the mastermind behind BlackShades, which was used to infect hundreds of thousands of computers worldwide.
As part of his plea deal, Yucel has agreed to waive his right to appeal if he receives a sentence of less than seven-and-a-quarter years in prison; his sentencing is scheduled for May 22. BlackShades software was sold for $40 and was used by criminals to control their victims' computers remotely, record keystrokes, steal personal information, and lock the computers until a ransom was paid.
BlackShades reportedly generated $350,000 in revenue for its creators, who were caught by a fake website created by the FBI for buying and selling stolen credit-card numbers. Yucel was arrested in Moldova in November 2013 and extradited to the U.S. to face trial.
Cybercrimes against property are on the rise, according to researchers, but exact numbers are difficult to come by because the FBI doesn't track online propery crime, credit-card fraud, or identity theft, according to researchers at the University of New Haven and the State University of New York at Albany. Their research into cybercrime underreporting is cited in a February 20, 2015, article on the Phys.org site.
Many cybercrimes are "handled" by the private-corporation victims rather than by the police. In fact, few such crimes are ever reported to law enforcement agencies. The researchers claim that more than half of the people who are victims of online fraud and data theft are never informed of the crimes. Companies are more interested in protecting their reputations, according to the researchers, who state that the dearth of information about cybercrimes makes fighting it more difficult.
--------------------------------------------------------
Worldwide debt rising right along with sea levels
Since 2007, the amount of money owed by everyone -- government, businesses, people -- has increased by $57 trillion, according to research reported by McKinley earlier this month. That's a 40.1 percent increase. As Neil Irwin of the New York Times points out in a February 5, 2015, article, financial institutions in the U.S. are actually less leveraged now than they were in 2007, but private debt in the U.S. economy is up 16 percent since 2007 to 233 percent of gross domestic product.
Kate Aronoff writes in a February 7, 2015, article on the Common Dreams site that according to Kingston University economist Steve Keen, any country whose private debt ratio exceeds 150 percent of GDP is vulnerable to financial calamity. (Keen was one of the few economists who predicted the 2008 financial crisis.) Japan's private debt ratio stands at 400 percent, the UK's at 350 percent, and China's at 217 percent.
Aronoff points out that the government's response to the 2008 crisis was to pump more money into the financial institutions whose carelessness precipitated the crash. In recent years, funding for public services has dried up, creating what the Guardian's Ross Ashcroft calls "backdoor privatization." Privatization cuts wages, which ultimately leads to increased debt.
----------------------------------------------------------
Are county jails becoming debtors' prisons?
Speaking of debt, a report issued earlier this month by the Vera Institute of Justice found that most of the people held in local and county jails in the U.S. are there for minor offenses for which they could be released if they could afford to pay the court-imposed costs. The New York Times' Timothy Williams discusses the report's findings in a February 11, 2015, article.
The good news is that programs are underway across the U.S. intended to reduce jail time for minor offenses. CNN's Sally Kohn reports in a February 23, 2015, article on the Smart Sentencing Act that has won bipartisan support in Congress but that has been stalled by U.S. Senator Chuck Grassley, R-Ia.
In addition to emphasizing prevention through employment and education, the reform efforts address the drug, alcohol, and mental-illness problems that afflict so many of the repeat offenders whose incarceration has become such a burden. While many of these programs have focused to date on state prisons, many jail inmates could benefit from the reforms as well.
February 17, 2015: How to ruin your life in 140 characters or fewer

Follow these 10 rules for safe, sane social media use to avoid alienating friends and family, losing your job, and being the target of a public shaming.
Legal shorts for February 17, 2015
What would George Washington think of his country now?
Lobbyists thrive by building relationships with lawmakers
On the fast track to American fascism
The one Senator who's speaking truth to power
Fight terrorism by fighting its source: Corruption
Anonymous users: Your ISP may ID you on demand -- and not even tell you
Lobbyists thrive by building relationships with lawmakers
On the fast track to American fascism
The one Senator who's speaking truth to power
Fight terrorism by fighting its source: Corruption
Anonymous users: Your ISP may ID you on demand -- and not even tell you
February 10, 2015: Browse better with these three essential freebies (plus one valuable cheapie)
Your chances of encountering trouble on the web go way down when you've got these security tools working for you: ID dangerous links before you click, block dangerous ads, prevent scripts from running automatically, and browse in a safe "sandbox."
Tech shorts for February 10, 2015: Facebook malware, privacy quiz, and data-security guidelines
Facebook malware attacks on the rise. A friend asked me recently about suspicious videos appearing on her Facebook timeline. The videos were labeled as posted by one of her friends, but they were graphic and unrelated to anything her friend was likely to post.
It turns out there has been a rash of malware-infected videos crashing Facebook timelines, as CSO's Steve Ragan reports in a January 30, 2015, article. The videos tag several of your friends, but if you click the link, your system is thoroughly scanned by the bad guys. Depending on what type of device you're using, you may be redirected to a site that tries to get you to pay for a bogus security service, or if you're using Windows, you may be prompted to download a "video player" that will actually infect your machine.
The security firm that disclosed the attack, BitDefender, recommends that you avoid downloading any players you're not sure of (for example, Flash updates should come only from the Adobe site). The company also suggests you keep your anti-malware software up-to-date and adjust your Facebook privacy settings to ask permission before content you're tagged in can be displayed to your friends. Instructions for doing so are on the Facebook Privacy Settings page.
What's your privacy IQ? Turns out mine wasn't as high as I thought when I got the results of Science Magazine's digital-privacy IQ test. The 10-question test takes only a few minutes to complete, but offers lessons that will serve you well into the future.
Encryption's benefits questioned. One of the best ways for companies to protect their customers' data from theft is to encrypt it -- when it's stored and when it's transmitted. In a February 5, 2015, article on Ars Technica, Steven M. Bellovin states that encryption wouldn't have prevented the theft of Social Security numbers and other personal information in the recent hack of health insurance company Anthem.
Bellovin claims that data has to be decrypted when it is accessed by Anthem employees, so the records would be vulnerable even if they were stored in encrypted form. Of course, how often do the workers need to access the SSNs and other sensitive information of the customers? Why can't Anthem -- and other firms -- provide access only to the data the employees need to complete their work? That's like saying bank tellers need access to the entire vault and all safe-deposit boxes to handle one person's cash withdrawal.
In the wings: Government guidelines for data protection. Companies are just starting to take data security seriously, in part because of increased attention from government regulators to lax security practices. For example, the Federal Trade Commission is preparing a "roadmap for responsible data practices," as Omer Tene of the International Association of Privacy Professionals reports in a February 3, 2015, article.
Raising red flags in particular are the ethics of targeted advertising, cross-device tracking, device fingerprinting, and onboarding -- the practice of combining data collected online and offline. Another area of focus is ensuring that companies are responsible for the data-security practices of their business partners and other third parties they deal with -- so-called indirect liability.
Also, the White House recently issued its own report on the dangers posed by lax data-security practices to consumers in general and school children in particular. In a February 5, 2015, article, TechCrunch's Ron Miller writes about the Obama administration's proposals to prevent misuse of big data without impinging the benefits the technology promises for health care and other industries.
It turns out there has been a rash of malware-infected videos crashing Facebook timelines, as CSO's Steve Ragan reports in a January 30, 2015, article. The videos tag several of your friends, but if you click the link, your system is thoroughly scanned by the bad guys. Depending on what type of device you're using, you may be redirected to a site that tries to get you to pay for a bogus security service, or if you're using Windows, you may be prompted to download a "video player" that will actually infect your machine.
The security firm that disclosed the attack, BitDefender, recommends that you avoid downloading any players you're not sure of (for example, Flash updates should come only from the Adobe site). The company also suggests you keep your anti-malware software up-to-date and adjust your Facebook privacy settings to ask permission before content you're tagged in can be displayed to your friends. Instructions for doing so are on the Facebook Privacy Settings page.
What's your privacy IQ? Turns out mine wasn't as high as I thought when I got the results of Science Magazine's digital-privacy IQ test. The 10-question test takes only a few minutes to complete, but offers lessons that will serve you well into the future.
Encryption's benefits questioned. One of the best ways for companies to protect their customers' data from theft is to encrypt it -- when it's stored and when it's transmitted. In a February 5, 2015, article on Ars Technica, Steven M. Bellovin states that encryption wouldn't have prevented the theft of Social Security numbers and other personal information in the recent hack of health insurance company Anthem.
Bellovin claims that data has to be decrypted when it is accessed by Anthem employees, so the records would be vulnerable even if they were stored in encrypted form. Of course, how often do the workers need to access the SSNs and other sensitive information of the customers? Why can't Anthem -- and other firms -- provide access only to the data the employees need to complete their work? That's like saying bank tellers need access to the entire vault and all safe-deposit boxes to handle one person's cash withdrawal.
In the wings: Government guidelines for data protection. Companies are just starting to take data security seriously, in part because of increased attention from government regulators to lax security practices. For example, the Federal Trade Commission is preparing a "roadmap for responsible data practices," as Omer Tene of the International Association of Privacy Professionals reports in a February 3, 2015, article.
Raising red flags in particular are the ethics of targeted advertising, cross-device tracking, device fingerprinting, and onboarding -- the practice of combining data collected online and offline. Another area of focus is ensuring that companies are responsible for the data-security practices of their business partners and other third parties they deal with -- so-called indirect liability.
Also, the White House recently issued its own report on the dangers posed by lax data-security practices to consumers in general and school children in particular. In a February 5, 2015, article, TechCrunch's Ron Miller writes about the Obama administration's proposals to prevent misuse of big data without impinging the benefits the technology promises for health care and other industries.
Legal shorts for February 10, 2015: Legal industry 3.0, post-Alice patentability guidance, and instructing clients to remove material from social media
Welcome to Legal Industry 3.0. Things move slowly in the world of jurisprudence -- some may say glacially. But even the legal profession is being turned upside-down by Internet technologies. In a February 5, 2015, article on Stanford Lawyer, Oliver R. Goodenough cautions legal types to prepare for the next phase of the ongoing upheaval, which Goodenough labels "computational jurisprudence 3.0."
In version 1.0, "technology empowers the current human players within the current system." The process doesn't become disruptive until version 2.0, when "technology replaces an increasing number of human players within the existing system." Things really start hopping when version 3.0 arrives. That's when "the power of computational technology for communication, modeling and execution permit a radical redesign, if not a full replacement, of the current system itself."
In the not-too-distant future, the legal action will be occurring not in the courtroom or law offices but in cyberspace, and the actors will be sophisticated computer programs, not lawyers and judges. The only things that won't change are the laws (much) and the clients. As Goodenough points out, this may sound like science fiction, but so did today's smart phones not so long ago.
The post-Alice patent world begins to take shape. The U.S. Supreme Court's decision last June in Alice Corp. v. CLS Bank International led to the invalidation of many business method and software patents, and a finding of unpatentability for others. The decision left many patent holders and potential patent holders scratching their heads over what constitutes an unpatentable "abstract idea."
On January 27, 2015, the U.S. Patent and Trademark Office issued abstract idea claim examples as part of its 2014 Interim Guidance on Subject Matter Eligibility. Polsinelli attorneys John Bednarz, Gregory Durbin, and James Stipek describe the guidelines in a February 5, 2015, article on the JD Supra Business Advisor site.
The authors point out that initial reaction by Federal courts indicated a trend toward finding software and business methods unpatentable, but more recently it appears many software and computer inventions will pass the two-part "abstract idea" test formulated in Mayo v. Prometheus in 2012 and will be afforded patent protections by the courts.
Lawyers may instruct their clients to remove Facebook posts prior to discovery, but.... The January 27, 2015, Weekly pointed out that courts have ruled all your Facebook posts available for discovery prior to a lawsuit, even those you've marked as private via Facebook's settings. On January 23, 2015, the Florida Bar issued a Proposed Advisory Opinion that lets lawyers know that it's okay for them to instruct their clients to delete all information from their social media pages before filing suit, but only if the lawyers can do so without violating laws related to "preservation and/or spoliation of evidence." Cozen O'Connor lawyer Joseph Rich reports on the advisory in a February 4, 2015, article on the JD Supra site.
The advisory instructs lawyers to preserve "an appropriate record" of any material removed from social media by a client pre-litigation if the lawyer knows or should know that the material is relevant to the case. The Florida Bar's instructions cite several instances when lawyers and clients were sanctioned for deleting relevant information from the client's social media accounts. As usual, it's safest not to post the potentially incriminating material in the first place.
Someday Facebook and other social networks will come with a Miranda or Surgeon General-type warning: "Caution -- What you post may be used against you in a court of law."
In version 1.0, "technology empowers the current human players within the current system." The process doesn't become disruptive until version 2.0, when "technology replaces an increasing number of human players within the existing system." Things really start hopping when version 3.0 arrives. That's when "the power of computational technology for communication, modeling and execution permit a radical redesign, if not a full replacement, of the current system itself."
In the not-too-distant future, the legal action will be occurring not in the courtroom or law offices but in cyberspace, and the actors will be sophisticated computer programs, not lawyers and judges. The only things that won't change are the laws (much) and the clients. As Goodenough points out, this may sound like science fiction, but so did today's smart phones not so long ago.
The post-Alice patent world begins to take shape. The U.S. Supreme Court's decision last June in Alice Corp. v. CLS Bank International led to the invalidation of many business method and software patents, and a finding of unpatentability for others. The decision left many patent holders and potential patent holders scratching their heads over what constitutes an unpatentable "abstract idea."
On January 27, 2015, the U.S. Patent and Trademark Office issued abstract idea claim examples as part of its 2014 Interim Guidance on Subject Matter Eligibility. Polsinelli attorneys John Bednarz, Gregory Durbin, and James Stipek describe the guidelines in a February 5, 2015, article on the JD Supra Business Advisor site.
The authors point out that initial reaction by Federal courts indicated a trend toward finding software and business methods unpatentable, but more recently it appears many software and computer inventions will pass the two-part "abstract idea" test formulated in Mayo v. Prometheus in 2012 and will be afforded patent protections by the courts.
Lawyers may instruct their clients to remove Facebook posts prior to discovery, but.... The January 27, 2015, Weekly pointed out that courts have ruled all your Facebook posts available for discovery prior to a lawsuit, even those you've marked as private via Facebook's settings. On January 23, 2015, the Florida Bar issued a Proposed Advisory Opinion that lets lawyers know that it's okay for them to instruct their clients to delete all information from their social media pages before filing suit, but only if the lawyers can do so without violating laws related to "preservation and/or spoliation of evidence." Cozen O'Connor lawyer Joseph Rich reports on the advisory in a February 4, 2015, article on the JD Supra site.
The advisory instructs lawyers to preserve "an appropriate record" of any material removed from social media by a client pre-litigation if the lawyer knows or should know that the material is relevant to the case. The Florida Bar's instructions cite several instances when lawyers and clients were sanctioned for deleting relevant information from the client's social media accounts. As usual, it's safest not to post the potentially incriminating material in the first place.
Someday Facebook and other social networks will come with a Miranda or Surgeon General-type warning: "Caution -- What you post may be used against you in a court of law."
February 3, 2015: What's the best way to fix the broken U.S. political system?

Efforts are underway both inside and outside Congress to counteract the control corporations currently exercise over the electoral process.
February 3, 2015: No such thing as 'anonymous' data, and another attempt to update the ECPA
No such thing as 'anonymous' data'
Internet services frequently promise not to share your personal information with third parties in any identifiable form. That turns out to be an empty promise because their attempts to anonymize the data prior to sharing it are useless.
Massachusetts Institute of Technology research Yves-Alexandre de Montjoye was able to identify 90 percent of credit-card purchasers by correlating the "anonymized" metadata about the transactions with "random observations" about the purchasers that are readily available from outside sources, such as geolocated tweets and mobile phone apps that log the user's location.
Science Magazine's John Bohannon reports on the study in a January 30, 2015, article.
The team of researchers led by de Montjoye used what are called correlation attacks to pair the metadata with other sources of information about the purchasers' day-to-day life. The process is called "differential privacy," and with the rise of big data and cloud computing, the practice is likely to become more common. That's why the researchers call for implementation of gatekeeper software that would allow the data to be used without imperiling individuals' privacy.
Harvard University computer scientist Salil Vadhan is quoted as saying, "If we can provide data for research without endangering privacy, it will do a lot of good.”
-----------------------------------------------------------
Coming soon (maybe): A long-overdue update to the Electronic Communications Privacy Act
In a January 28, 2015, article on the Real Clear Policy site, U.S. Senators Patrick Leahy (D., Vt.) and Mike Lee (R., Utah) write that they will soon reintroduce legislation that extends the protections of the Electronic Communications Privacy Act of 1986 to email and other information stored in the cloud. If their proposal succeeds (no sure thing), a search warrant based on probable cause would be required for the government to access information stored online.
The Senators claim to have bipartisan support for the bill in both houses of Congress. The groups lining up to support the bill include Americans for Tax Reform, the ACLU, the Heritage Foundation, and the Center for Democracy and Technology. Not surprisingly, groups opposing the ECPA update, according to the Electronic Privacy Information Center, include the U.S. Justice Department and local law enforcement agencies.
Internet services frequently promise not to share your personal information with third parties in any identifiable form. That turns out to be an empty promise because their attempts to anonymize the data prior to sharing it are useless.
Massachusetts Institute of Technology research Yves-Alexandre de Montjoye was able to identify 90 percent of credit-card purchasers by correlating the "anonymized" metadata about the transactions with "random observations" about the purchasers that are readily available from outside sources, such as geolocated tweets and mobile phone apps that log the user's location.
Science Magazine's John Bohannon reports on the study in a January 30, 2015, article.
The team of researchers led by de Montjoye used what are called correlation attacks to pair the metadata with other sources of information about the purchasers' day-to-day life. The process is called "differential privacy," and with the rise of big data and cloud computing, the practice is likely to become more common. That's why the researchers call for implementation of gatekeeper software that would allow the data to be used without imperiling individuals' privacy.
Harvard University computer scientist Salil Vadhan is quoted as saying, "If we can provide data for research without endangering privacy, it will do a lot of good.”
-----------------------------------------------------------
Coming soon (maybe): A long-overdue update to the Electronic Communications Privacy Act
In a January 28, 2015, article on the Real Clear Policy site, U.S. Senators Patrick Leahy (D., Vt.) and Mike Lee (R., Utah) write that they will soon reintroduce legislation that extends the protections of the Electronic Communications Privacy Act of 1986 to email and other information stored in the cloud. If their proposal succeeds (no sure thing), a search warrant based on probable cause would be required for the government to access information stored online.
The Senators claim to have bipartisan support for the bill in both houses of Congress. The groups lining up to support the bill include Americans for Tax Reform, the ACLU, the Heritage Foundation, and the Center for Democracy and Technology. Not surprisingly, groups opposing the ECPA update, according to the Electronic Privacy Information Center, include the U.S. Justice Department and local law enforcement agencies.
January 27, 2015: Why you should care about your loss of privacy

Internet services and app developers consider our personal information a natural resource available for the taking. It's time to personalize the data metaphors as a first step toward reasserting control over our information.
January 27, 2015: Dark money funding judicial campaigns, and the auto industry fakes engine roar
Judges and 'dark money' campaign contributions
In an October 2014 article, Mother Jones reported on the seven-fold increase in contributions by special-interest and partisan groups to state judicial campaigns between 2000 and 2011-2012. As the magazine points out, the $288 million spent on judicial races since 2000 dwarfs the $17 billion spent since that year on Congressional campaigns. However, it's difficult to track contributions to judicial campaigns because of "weak" state disclosure laws, according to the publication.
In one instance, the CEO of an energy company in West Virginia contributed $3 million to the campaign of a state Supreme Court justice, who just happened to cast the deciding vote that overturned a $50 million judgment against the company. Not a bad investment!
The article quotes retired U.S. Supreme Court Justice Sandra Day O'Connor, who asserted that the mere perception that judicial decisions are biased is sufficient to destroy support for the courts. I'd go even further and say that all campaign contributions are a form of bribery -- directly or indirectly. I readily acknowledge that I hold a minority opinion on this matter. For now.
---------------------------------------------------------
That Mustang roar is faked? Say it ain't so, Henry!
One of the benefits of more fuel-efficient automobile engines is less engine noise. For most car models, this is a good thing. For Ford Mustangs and other muscle cars, the lack of the familiar rumble could be a deal-breaker.
Drew Harwell writes in a January 21, 2015, article in the Washington Post that Ford, BMW, Volkswagen, and other automakers are using fake engine noise to make their vehicles sound more appealing to consumers.
For example, the 2015 Ford Mustang EcoBoost features an "Active Noise Control" system that amplifies the engine noise through the car's speakers. A similar system is reportedly used in the six-cylinder model of the F-150 pickup truck, although Ford isn't talking about the noise enhancements, according to Harwell.
Other audio enhancers include Volkswagen's Soundaktor speaker in the GTI and Beetle Turbo, and Porsche's "sound symposer" noise-boosting tubes. Since electric cars run nearly silently, adding the equivalent of engine noise becomes a safety issue. Federal agencies are expected to release regulations later this year requiring hybrid and electric cars to play fake engine noise to alert pedestrians, bicyclists, and other drivers.
Several car experts state that while the audio boosts don't affect performance and may enhance the driving experience for some customers, the carmakers should simply admit to the fakery. As Kelly Blue Book's Karl Brauer is quoted as saying, the companies "should stop the lies and get real with drivers."
Imagine if dealing honestly with customers caught on with other companies. "You may say I'm a dreamer...."
In an October 2014 article, Mother Jones reported on the seven-fold increase in contributions by special-interest and partisan groups to state judicial campaigns between 2000 and 2011-2012. As the magazine points out, the $288 million spent on judicial races since 2000 dwarfs the $17 billion spent since that year on Congressional campaigns. However, it's difficult to track contributions to judicial campaigns because of "weak" state disclosure laws, according to the publication.
In one instance, the CEO of an energy company in West Virginia contributed $3 million to the campaign of a state Supreme Court justice, who just happened to cast the deciding vote that overturned a $50 million judgment against the company. Not a bad investment!
The article quotes retired U.S. Supreme Court Justice Sandra Day O'Connor, who asserted that the mere perception that judicial decisions are biased is sufficient to destroy support for the courts. I'd go even further and say that all campaign contributions are a form of bribery -- directly or indirectly. I readily acknowledge that I hold a minority opinion on this matter. For now.
---------------------------------------------------------
That Mustang roar is faked? Say it ain't so, Henry!
One of the benefits of more fuel-efficient automobile engines is less engine noise. For most car models, this is a good thing. For Ford Mustangs and other muscle cars, the lack of the familiar rumble could be a deal-breaker.
Drew Harwell writes in a January 21, 2015, article in the Washington Post that Ford, BMW, Volkswagen, and other automakers are using fake engine noise to make their vehicles sound more appealing to consumers.
For example, the 2015 Ford Mustang EcoBoost features an "Active Noise Control" system that amplifies the engine noise through the car's speakers. A similar system is reportedly used in the six-cylinder model of the F-150 pickup truck, although Ford isn't talking about the noise enhancements, according to Harwell.
Other audio enhancers include Volkswagen's Soundaktor speaker in the GTI and Beetle Turbo, and Porsche's "sound symposer" noise-boosting tubes. Since electric cars run nearly silently, adding the equivalent of engine noise becomes a safety issue. Federal agencies are expected to release regulations later this year requiring hybrid and electric cars to play fake engine noise to alert pedestrians, bicyclists, and other drivers.
Several car experts state that while the audio boosts don't affect performance and may enhance the driving experience for some customers, the carmakers should simply admit to the fakery. As Kelly Blue Book's Karl Brauer is quoted as saying, the companies "should stop the lies and get real with drivers."
Imagine if dealing honestly with customers caught on with other companies. "You may say I'm a dreamer...."
January 20, 2015: The battle against data thieves heats up

A proposed federal breach-notification law and court decisions allowing suits by data-theft victims against the companies hit by the breaches indicate a bolstering of defenses against cybercrooks.
January 20, 2015: To live longer, stand up and jump around; to stay young, exercise -- vigorously and often
Live longer by dancing through those commercial breaks
Everybody knows you shouldn't make a big change in lifestyle simply because you read about the results of some study. Still, after I heard about the dangers of prolonged sitting, as reported by Tech Times' Rhodi Lee in a January 20, 2015, article, I made a mental note to stand up and move around for a few minutes every hour. All because of research published in the Annals of Internal Medicine on January 19, 2015, which compiled and analyzed the results 47 other studies on the effects of sitting for long periods of time.
The upshot? A sedentary lifestyle increases your risks of heart disease, cancer, diabetes, and premature death -- by 15 to 20 percent in some cases, and by up to 90 percent for diabetes. More bad news: exercising regular doesn't mitigate the increased risk. "Prolonged sitting" is defined as between eight and 12 hours a day. To avoid the perils of a good, long sit, the researchers recommend that we stand up or move around for a few minutes each half hour we're sitting at a desk. And while we're watching TV, we should get up and dance to the commercials -- or maybe skip the commercials and do a few brisk laps around the living room.
Your dog will love it.
-----------------------------------------------------------
Can you have your pizza and longevity, too?
Some studies you might benefit from overreacting to -- even if they eventually turn out to be not so telling as they first appeared. In a January 7, 2015, article in the New York Times, Gretchen Reynolds reports on the findings of researchers at King's College of London and the University of Birmingham in England who studied the health of very active older folks. They concluded that regular vigorous physical activity can keep your body young.
The subjects were men and women between the ages of 55 and 79 who bicycle regularly and are able to cover 62 miles in six-and-a-half hours for the men, and 37 miles in five-and-a-half hours for the women. They were not competitive athletes but rather "serious recreational riders." When they were given various physical ability tests, the riders were found to perform much closer to young adults than to other people their own age in terms of balance, reflexes, metabolic health, and memory.
Unfortunately, a high exercise level didn't prevent age-related declines in muscle power and mass, and aerobic capacity. Still, the cyclists rated much higher than others in their age group in these categories as well. As usual, the researchers warn against coming to conclusions based on the results of a single study, but they point out that staying active has benefits beyond possibly delaying the physical effects of aging. It makes you feel good, too, and you don't need a study to tell you that.
Excuse me, but it's time for me to hop on the old two-wheeler and ride -- all the way to the taqueria across town.
Everybody knows you shouldn't make a big change in lifestyle simply because you read about the results of some study. Still, after I heard about the dangers of prolonged sitting, as reported by Tech Times' Rhodi Lee in a January 20, 2015, article, I made a mental note to stand up and move around for a few minutes every hour. All because of research published in the Annals of Internal Medicine on January 19, 2015, which compiled and analyzed the results 47 other studies on the effects of sitting for long periods of time.
The upshot? A sedentary lifestyle increases your risks of heart disease, cancer, diabetes, and premature death -- by 15 to 20 percent in some cases, and by up to 90 percent for diabetes. More bad news: exercising regular doesn't mitigate the increased risk. "Prolonged sitting" is defined as between eight and 12 hours a day. To avoid the perils of a good, long sit, the researchers recommend that we stand up or move around for a few minutes each half hour we're sitting at a desk. And while we're watching TV, we should get up and dance to the commercials -- or maybe skip the commercials and do a few brisk laps around the living room.
Your dog will love it.
-----------------------------------------------------------
Can you have your pizza and longevity, too?
Some studies you might benefit from overreacting to -- even if they eventually turn out to be not so telling as they first appeared. In a January 7, 2015, article in the New York Times, Gretchen Reynolds reports on the findings of researchers at King's College of London and the University of Birmingham in England who studied the health of very active older folks. They concluded that regular vigorous physical activity can keep your body young.
The subjects were men and women between the ages of 55 and 79 who bicycle regularly and are able to cover 62 miles in six-and-a-half hours for the men, and 37 miles in five-and-a-half hours for the women. They were not competitive athletes but rather "serious recreational riders." When they were given various physical ability tests, the riders were found to perform much closer to young adults than to other people their own age in terms of balance, reflexes, metabolic health, and memory.
Unfortunately, a high exercise level didn't prevent age-related declines in muscle power and mass, and aerobic capacity. Still, the cyclists rated much higher than others in their age group in these categories as well. As usual, the researchers warn against coming to conclusions based on the results of a single study, but they point out that staying active has benefits beyond possibly delaying the physical effects of aging. It makes you feel good, too, and you don't need a study to tell you that.
Excuse me, but it's time for me to hop on the old two-wheeler and ride -- all the way to the taqueria across town.
January 13, 2015: How to combat hate and harassment on the Internet
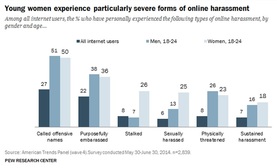
When ignoring the "trolls" doesn't work, use counter-speech to turn the tables on the haters and harassers.
January 13, 2015: FCC proposes faster 'broadband' standards; plus, journalist deaths in the line of duty
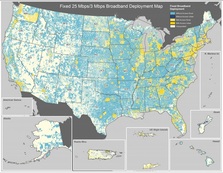
FCC chairman proposes redefining 'broadband' as at least 25Mbps downstream, 3Mbps upstream
Each year, the U.S. Federal Communications Commission issues the Annual Broadband Progress Report, as mandated by Congress. In the draft of the most recent report, FCC Chairman Tom Wheeler proposes changing the definition of "broadband" from the current 4Mbps downstream and 1Mbps upstream to 25Mbps downstream and 3Mbps upstream.
Ars Technica's Jon Brodkin reports in a January 7, 2015, article that Wheeler believes the higher speeds are required to meet the mandate in the Telecommunications Act of 1996 for "advanced telecommunications capabilities" sufficient to "enable users to originate and receive high-quality voice, data, graphics, and video telecommunications using any technology."
ISPs would not be required to satisfy the 25/3 standard for government-funded projects, but an FCC official indicated that several dozen "rural broadband experiments" being funded by the agency would offer speeds at that level or greater. The FCC believes ISPs are not moving fast enough to expand their broadband offerings. Data released by the agency indicate that while 92 percent of people in urban areas of the country have access to 25/3 Internet service, only 47 percent of people in rural areas have access available at those speeds. The distribution is shown on the map above (click to enlarge).
In a related move, Wheeler is ready to reclassify ISPs as "common carriers" subject to government regulation under Title II of the Communications Act of 1934. Ars Technica's Megan Geuss explains in another January 7, 2015, article that Title II will be the basis for the FCC's net neutrality rules for the broadband industry. ISPs complain that such regulation would stifle innovation, but Wheeler is confident the Title II rules can be applied in a way that will not deter investment in new Internet infrastructure and services.
------------------------------------------------------------
A tribute to journalists killed in the line of duty
At least 60 journalists were killed in the course of doing their job worldwide in 2014, according to a report by the Committee to Protect Journalists. That number is actually fewer than the 70 journalist deaths recorded by the group in 2013, and the 74 deaths confirmed in 2012 and 2009.
The first two weeks of 2015 show that threats to journalists continue. On the day after the murder of 12 staff members of the French satirical magazine Charlie Hebdo, Nerlita "Nerlie" Ledesma, a reporter for a newspaper in the Bataan province of the Luzon in the Philippines, was gunned down. According to a January 8, 2015, article by Human Rights Watch's Phelim Kine, Ledesma's death is under investigation and has not yet been confirmed as the result of her work for the newspaper she worked for in the city of Balanga.
The Philippines has been a particularly dangerous place for journalists to ply their trade. The murderers of at least 34 journalists on November 23, 2009, in what is called the Maguindanao massacre, have yet to face justice. The Wikipedia entry describing the massacre indicates that as of August 2014, no one has been convicted of the murders, although trials of several dozen suspects are ongoing.
According to Wikipedia, the last journalist killed in the line of duty in the U.S. was Chauncey Bailey of the Oakland Post on August 2, 2007. Just last month, American photojournalist Luke Somers was killed during a failed rescue attempt in Yemen, as USA Today's Kim Hjelmgaard reported in a December 6, 2014, article.
To the family, friends, and colleagues of all journalists killed in action -- and all victims of hatemongers and their misguided minions -- my heartfelt condolences. May they rest in peace.
Each year, the U.S. Federal Communications Commission issues the Annual Broadband Progress Report, as mandated by Congress. In the draft of the most recent report, FCC Chairman Tom Wheeler proposes changing the definition of "broadband" from the current 4Mbps downstream and 1Mbps upstream to 25Mbps downstream and 3Mbps upstream.
Ars Technica's Jon Brodkin reports in a January 7, 2015, article that Wheeler believes the higher speeds are required to meet the mandate in the Telecommunications Act of 1996 for "advanced telecommunications capabilities" sufficient to "enable users to originate and receive high-quality voice, data, graphics, and video telecommunications using any technology."
ISPs would not be required to satisfy the 25/3 standard for government-funded projects, but an FCC official indicated that several dozen "rural broadband experiments" being funded by the agency would offer speeds at that level or greater. The FCC believes ISPs are not moving fast enough to expand their broadband offerings. Data released by the agency indicate that while 92 percent of people in urban areas of the country have access to 25/3 Internet service, only 47 percent of people in rural areas have access available at those speeds. The distribution is shown on the map above (click to enlarge).
In a related move, Wheeler is ready to reclassify ISPs as "common carriers" subject to government regulation under Title II of the Communications Act of 1934. Ars Technica's Megan Geuss explains in another January 7, 2015, article that Title II will be the basis for the FCC's net neutrality rules for the broadband industry. ISPs complain that such regulation would stifle innovation, but Wheeler is confident the Title II rules can be applied in a way that will not deter investment in new Internet infrastructure and services.
------------------------------------------------------------
A tribute to journalists killed in the line of duty
At least 60 journalists were killed in the course of doing their job worldwide in 2014, according to a report by the Committee to Protect Journalists. That number is actually fewer than the 70 journalist deaths recorded by the group in 2013, and the 74 deaths confirmed in 2012 and 2009.
The first two weeks of 2015 show that threats to journalists continue. On the day after the murder of 12 staff members of the French satirical magazine Charlie Hebdo, Nerlita "Nerlie" Ledesma, a reporter for a newspaper in the Bataan province of the Luzon in the Philippines, was gunned down. According to a January 8, 2015, article by Human Rights Watch's Phelim Kine, Ledesma's death is under investigation and has not yet been confirmed as the result of her work for the newspaper she worked for in the city of Balanga.
The Philippines has been a particularly dangerous place for journalists to ply their trade. The murderers of at least 34 journalists on November 23, 2009, in what is called the Maguindanao massacre, have yet to face justice. The Wikipedia entry describing the massacre indicates that as of August 2014, no one has been convicted of the murders, although trials of several dozen suspects are ongoing.
According to Wikipedia, the last journalist killed in the line of duty in the U.S. was Chauncey Bailey of the Oakland Post on August 2, 2007. Just last month, American photojournalist Luke Somers was killed during a failed rescue attempt in Yemen, as USA Today's Kim Hjelmgaard reported in a December 6, 2014, article.
To the family, friends, and colleagues of all journalists killed in action -- and all victims of hatemongers and their misguided minions -- my heartfelt condolences. May they rest in peace.
January 6, 2015: Beat ransomware by saving your files to the cloud
Turn standard backup on its head by designating one or several free cloud-storage services as your primary file repository and "backing up" your files to your local hard drive.
January 6, 2015: The hazards of distracted walking, and password-creation hell
One of the most dangerous of human activities is... walking?
I once read that human bipedalism is one of the marvels of nature. With every step, we come perilously close to falling flat on our faces. Walking while engaged in one (or both) of two other very common human activities can be extremely dangerous to your health.
AJ Vicens reports in a December 29, 2014, article in Mother Jones magazine that injuries incurred from texting while walking are skyrocketing. A study conducted in 2012 by researchers at Stony Brook University found that texting walkers were 61 percent more likely than their non-texting counterparts to wander off course. Emergency-room visits resulting from accidents to people distracted while walking and using their cell phone increased nearly 500 percent between 2005 and 2010, according to Ohio State University researchers.
Toss a couple of adult beverages into the mix and you've got a disaster just waiting to happen. Another December 29, 2014, Mother Jones article written by Maddie Oatman warns that on a per-mile basis, a drunk walker is eight times more likely to get killed than a drunk driver. That's according to Steven Levitt in his 2011 book, SuperFreakonomics.
Numbers collected by the National Highway Traffic Safety Administration in 2012 found that in almost half of the accidents that year in which a pedestrian was killed by a car, either the driver or the walker, or both, had blood alcohol levels above the legal limit. In these fatal accidents, 34 percent of the walkers were impaired, compared to 14 percent of the drivers.
It's no surprise that New Year's Day and Halloween are the two days you're most likely to be killed by a car while walking. What may raise an eyebrow is the day the researchers claim you're least likely to be the victim of such an accident: April 20th, or the infamous 4-20.
-------------------------------------------------------------------
I once read that human bipedalism is one of the marvels of nature. With every step, we come perilously close to falling flat on our faces. Walking while engaged in one (or both) of two other very common human activities can be extremely dangerous to your health.
AJ Vicens reports in a December 29, 2014, article in Mother Jones magazine that injuries incurred from texting while walking are skyrocketing. A study conducted in 2012 by researchers at Stony Brook University found that texting walkers were 61 percent more likely than their non-texting counterparts to wander off course. Emergency-room visits resulting from accidents to people distracted while walking and using their cell phone increased nearly 500 percent between 2005 and 2010, according to Ohio State University researchers.
Toss a couple of adult beverages into the mix and you've got a disaster just waiting to happen. Another December 29, 2014, Mother Jones article written by Maddie Oatman warns that on a per-mile basis, a drunk walker is eight times more likely to get killed than a drunk driver. That's according to Steven Levitt in his 2011 book, SuperFreakonomics.
Numbers collected by the National Highway Traffic Safety Administration in 2012 found that in almost half of the accidents that year in which a pedestrian was killed by a car, either the driver or the walker, or both, had blood alcohol levels above the legal limit. In these fatal accidents, 34 percent of the walkers were impaired, compared to 14 percent of the drivers.
It's no surprise that New Year's Day and Halloween are the two days you're most likely to be killed by a car while walking. What may raise an eyebrow is the day the researchers claim you're least likely to be the victim of such an accident: April 20th, or the infamous 4-20.
-------------------------------------------------------------------
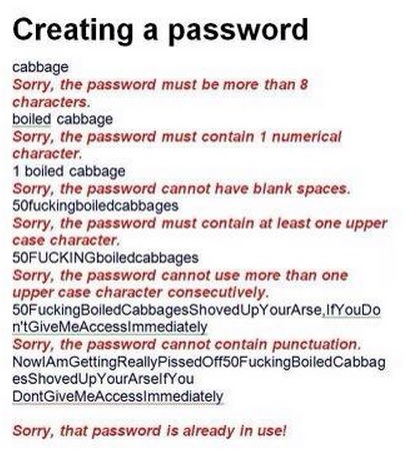
You have now entered password-creation hell
My antipathy for passwords is no secret, as evident by April 29, 2014's "I hate passwords," August 18, 2014's "Most data breaches are the result of weak or stolen credentials," and August 25, 2014's "Baby steps closer to authentication that doesn't rely on passwords."
Users' frustration with the rules organizations apply to the creation of passwords is summed up beautifully in this Twitter post by YouHadOneJob. (Caution: very adult language is expressed.)
In my experience, Apple's password policies are absolutely the most user-hostile. It often gets to the point where I simply request a password reset automatically when signing into an Apple service I haven't accessed in awhile rather than do battle with the company's convoluted, irrational password rules. I pray a reliable non-password authentication method arrives soon and ends our dependence on IT managers' sadistic password-creation rules.
My antipathy for passwords is no secret, as evident by April 29, 2014's "I hate passwords," August 18, 2014's "Most data breaches are the result of weak or stolen credentials," and August 25, 2014's "Baby steps closer to authentication that doesn't rely on passwords."
Users' frustration with the rules organizations apply to the creation of passwords is summed up beautifully in this Twitter post by YouHadOneJob. (Caution: very adult language is expressed.)
In my experience, Apple's password policies are absolutely the most user-hostile. It often gets to the point where I simply request a password reset automatically when signing into an Apple service I haven't accessed in awhile rather than do battle with the company's convoluted, irrational password rules. I pray a reliable non-password authentication method arrives soon and ends our dependence on IT managers' sadistic password-creation rules.
