Menu
Cloud governance: The key to effectively scaling your cloud |
|
“Cloud speed” has taken the IT world by storm. When it comes to getting applications and data systems relocated to cloud services, the quicker the better, right? In most cases, such hasty implementations do indeed make waste – of time, resources, and ultimately efficiency.
In a classic example of “ready, fire, aim,” companies find themselves attempting to retrofit governance into the systems they have migrated to the cloud in a rush. Part of the problem is that IT often finds itself reacting to cloud-migration projects that are driven by business departments. A typical example is the “accidental hybrid,” which arises when one of the organization’s apps, such as for HR or CRM, has been moved to the cloud, and subsequently a cloud database is glommed onto the app, followed by a data warehouse, and then some analytical tools for good measure. The job of integrating and securing the complex system that results falls to IT. Here’s the challenge: Get a comprehensive, cohesive, and singular infrastructure in place for data security and data governance without slowing the pace of cloud adoption in the company. Step one is to create a central point of operational management for all data systems. Like Big Brother, but in a good way Start by giving IT a central point that provides a view into everything that’s happening related to your applications:
Cloud identity and access management (AIM) is projected to boom in 2017 and beyond. According to a Garner report cited by Allied Market Research, the cloud security market will grow at a compound annual rate of 23.5 percent through 2020, to a total value of $8.9 billion by that year. Driving the market are increased use on handheld devices (BYOD and CYOD, or “choose your own device”), growing reliance on cloud services by midsize and large enterprises, and the surge in demand for managed security services. 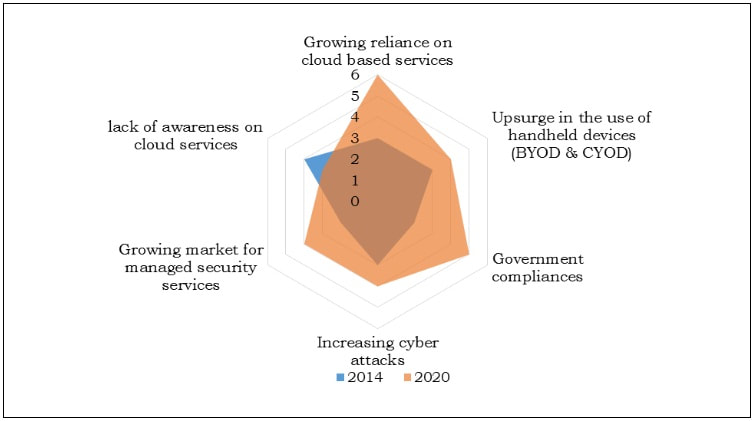 As companies come to rely on the cloud more heavily, the emphasis shifts from awareness to managed security and government compliance. Source: Allied Market Research As companies come to rely on the cloud more heavily, the emphasis shifts from awareness to managed security and government compliance. Source: Allied Market Research
CloudTech’s Nitin Chitmalwar lays out the basic framework for cloud AIM: automate the initiation, capture, recording, and management of user identities for each process in the business network. Grant access privileges only after timely and comprehensive application of organizational policies. The analysis covers all individuals and services comprising the cloud AIM system and includes authorization, authentication, and auditing.
The role of cloud AIM software Your cloud IAM system models the entire organization:
Regulatory and compliance policies are applied automatically via IAM processes. Careful assignment of access permissions combined with multi-factor authentication identify and block malware, malicious acts of insiders, hackers, spoofing, and fake ID holders. Security is enforced via two parallel streams: one passive stream monitors all traffic into, out of, and within the organization’s data systems; and the other active stream that enforces the company’s comprehensive security policy.  A three-step approach to implementing identity and access management begins by assessing your current IAM systems, identifying the IAM approach that best fits the organization, and finally defining your implementation strategy. Source: Chip Epps, via Sand Hill A three-step approach to implementing identity and access management begins by assessing your current IAM systems, identifying the IAM approach that best fits the organization, and finally defining your implementation strategy. Source: Chip Epps, via Sand Hill
Cloud IAM software helps reduce overall IT spending by consolidating all data security – keeping data safe and controlling access to data and network resources – in a centralized security hub that operates on multiple levels. The success of any cloud IAM project depends on ensuring visibility into your applications. Not just “Do you know where your app is?” visibility. We’re talking deep-dive visibility, like IT has never had before.
Governance requires an ‘x-ray vision’ view of your apps Dean Wiech of security vendor Tools4Ever explains in a CSO article why cloud governance requires greater insight into data operation than is available from traditional auditing products. There are many more potential access points in modern networks, and many more potential users of the company’s data. More “layers” of operational data are needed to model the “what ifs”: every possible outcome, and its impact on the organization’s information infrastructure. System administrators need to have a complete history of every employee’s activity that they can organize and manage from a single vantage point. In an instant, admins can determine who has accounts on what system, when were those accounts used, what permissions are associated with the accounts, and who has authority to grant the account permissions. The permissions auditing must apply to all of the organization’s data assets: databases, shared file systems, data centers, access control, backups, passwords, network devices and printers. Privilege creep is addressed by ensuring permissions are revoked when an employee no longer needs them following a change in responsibilities. Centralized control simplifies elimination of stale and orphan accounts, and identifies shared accounts for which no single individual is responsible. A to Z governance in a single cloud portal The deep-dive visibility and wide-angle view of all your apps and databases that is the core of cloud governance is delivered the intuitive control dashboard at the heart of the Morpheus cloud application management service. Morpheus ensures that all of your organization’s most important data can be monitored and controlled from a single intuitive interface that provides at a glance an overall indication of system health, as well as the status of individual apps, databases, and components. In addition to the web UI, Morpheus lets you manage apps, databases, and app stack components via a command-line interface or through API calls. There is no faster way to provision these resources and to add new nodes; databases and app clusters are reconfigured automatically to accommodate the added nodes. Morpheus’s automatic logging supports immediate introspection, troubleshooting, and uptime monitoring. That immediacy extends to defining roles and access for individuals and groups using Morpheus’s clear dashboard to set responsibilities and access limits for teams and individuals based on geographic zone, server groups, application, or database. It’s time for your governance operations to benefit from the same efficiency and scalability of your other cloud apps. |
