Menu
How zero-trust security makes VMs more efficient |
|
In the old data-security model, a layer of protection was applied to information systems after the fact, like a coat of lacquer on finely crafted Chippendale cabinet. Security happened outside the data itself, at the perimeter of the physical network (so-called north-south traffic). What happened inside the perimeter (east-west) was presumed safe.
Not anymore. In the cloud era, security is baked into every system component at the network, compute, and storage layers. The zero-trust model presumes that every bit of data traffic is potentially hazardous. It is related to the security practice of microsegmentation, which controls east-west data traffic by segmenting it at the switch port level from server to server. CTOVision.com's Nathaniel Crocker describes microsegmentation as a way to "slow down attackers, like pouring molasses on the floor." Microsegmentation plays a central role in zero-trust security for three reasons, according to Crocker:
Microsegmentation's persistence offers three benefits in particular: you don't need to create all access control lists manually; you can create policies that affect workloads; and your policies follow applications, databases, and web servers. 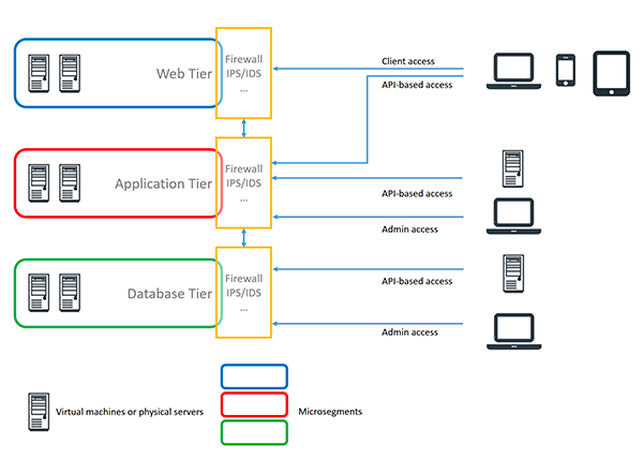 Microsegmentation splits workloads into segments based on virtual networks, where a specific workload may be in multiple segments at the web, app, or database tier. Source: KuppingerCole Microsegmentation splits workloads into segments based on virtual networks, where a specific workload may be in multiple segments at the web, app, or database tier. Source: KuppingerCole
Zero-trust model applied to protect cloud data
Cloud workloads are like vagabonds: Their itch to roam means they rarely stay in one place. TechTarget's Dave Shackleford writes that cloud security services offer views into data that don't extend beyond a single cloud app, but a workload uploaded to AWS, for example, is almost certain to be accessed by or moved to another cloud service. Zero trust is the only cloud-security model capable of ensuring the safety of cloud assets, according to Shackleford. To implement zero trust in cloud environments, security must be baked into the cloud workloads themselves so it travels with apps and data as they move between environments. Of equal importance is the need to implement the monitoring and security controls provided by each distinct cloud service. The first step in any cloud security strategy is inventory discovery and management. A service such as the Morpheus cloud application management platform gets your security plan started on the right foot. Morpheus allows your organization to store and maintain all its most important data and apps in a single place, whether they're implemented on public, private, or hybrid clouds. There's no faster way to provision databases, apps, or app stack components than with Morpheus's clear and complete dashboard interface. System, application, and database logs are collected automatically for each provisioned IT system for lightning-quick analysis and troubleshooting. Uptime monitoring, backup, and recovery are equally automatic. Security is bolstered by Morpheus's ability to set roles and access controls for individuals and groups by geographic zone, or at the app and database level. Overcoming the challenges of zero-trust VMs Zero-trust security can't be implemented in a large data center using security appliances, according to CloudTech's Abhijeet Prabhune. It's nearly impossible to keep security appliances up-to-date and running smoothly. Also, security appliances don't scale well, so expenses rise and appliances become a performance chokepoint. Lastly, the appliances create silos at a time when you're trying to flatten and distribute your data resources. Managing zero trust becomes trickier in virtual environments because instances can be shut down and then brought back up on a different server in a far-flung location. The policies associated with each VM have to travel with it. Prabhune proposes a different approach to applying zero-trust security in virtual environments that places a virtual appliance alongside each VM. Security is implemented at the host/hypervisor level via Linux iptables, or alternatively at the vSwitch level using Open vSwitch (OVS) and Connection Tracking Rules. 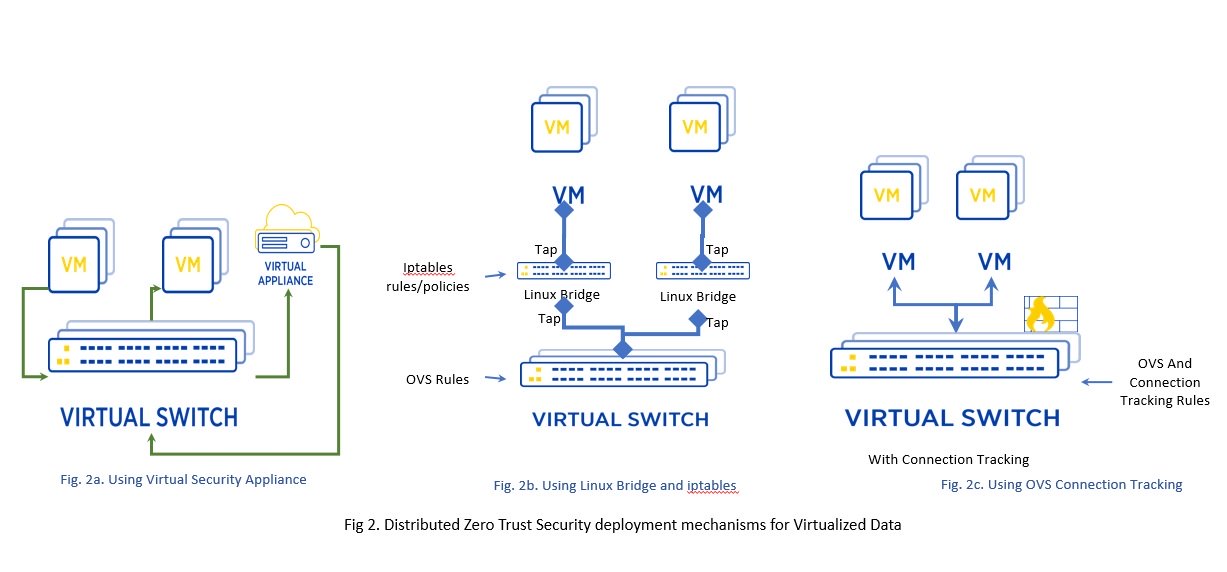 Two approaches to zero-trust security in virtual environments use Linux iptables (2b) and OVS Conntrack (2c). Source: Cloud Computing News Two approaches to zero-trust security in virtual environments use Linux iptables (2b) and OVS Conntrack (2c). Source: Cloud Computing News
The OVS Conntrack method is more practical than using Linux iptables, but performance and scale remain problems. You can offload OVS and Conntrack processing from the CPU cores to a SmartNIC and associated software. This approach makes it more feasible to implement security on a per-VM or per-container basis, according to Prabhune.
A four-step approach to implementing zero-trust model in IT It makes sense that security has to tag along wherever your data may travel to. Along with network segmentation and virtualization, your best tool for keeping cloud data secure is a solid trust model government all access rights. SecurityIntelligence's Srini Tummalapenta lays out a four-step process for implementing the zero-trust model:
|
