Menu
Telephone tech-support scams are on the rise

For the third time in as many years, the U.S. Federal Trade Commission has shut down scam telephone tech-support services that stole an estimated $120 million from consumers by tricking them into thinking there was something wrong with their computers. In a November 19, 2014, article, Ars Technica's Jon Brodkin reports on the latest round of arrests.
The scam begins when the victim downloads a "free" program that promises to scan their computer for viruses and performance problems. Of course, the malware always finds problems that can only be fixed by paying $30 to $50 for the full version of the program. When the victim runs the full version, they are instructed to call a toll-free number to "activate" the software. The person who answers uses "deceptive scare tactics," according to the FTC, to coerce the unwary downloader into buying support services they don't need.
Even worse, the company representatives may talk the poor soul into installing remote-control software on their system that gives the crooks unfettered access to the machine's contents. Then they open utilities on the computer such as the Windows Event Viewer in an attempt to fool the PC's owner into thinking there's something seriously wrong with the system. The "fixes" they claim are required cost as much as $500.
(Event Viewer nearly always includes some harmless cautions and warnings, designated with yellow exclamation marks and red "x"s.)
Don't share personal information with any strangers who call you
You know the rule about giving out personal information over the telephone: If you called the party, if you're confident the company is legitimate, and if you've dealt with the firm in the past, then you can probably share your street address (if necessary), telephone number, partial or full account number, and the last four digits of your Social Security number.
However, if the party called you, don't share even your name with them. In fact, you should be the one asking the questions: What is your name? What is your company's name? How did you get my telephone number? Where are you located? Who can I contact to verify your identity?
Even if your number is on the Federal Communication Commission's National Do Not Call Registry, you may receive unsolicited offers over the phone. The standard response is to politely interrupt the spiel and explain that you don't want to receive these calls, so please remove your number from their database. The telemarketers' scripts usually instruct them to tell you that it may take as long as 36 hours for the number to be removed.
Don't download or install any 'free' program you never heard of
Every modern Windows PC, Mac, and Chromebook ships with all the software required to operate it safely, although you may need to enable manually some security features that are off by default. In a September 19, 2014, post entitled "How to prevent malware and adware downloads," I explained how to ensure your Windows PC is protected. The information in the article refers to Windows 7, but it applies to Windows 8 as well.
The only other software you need is a browser such as Firefox, Google Chrome, or Opera; a free PDF reader such as Foxit Reader; and a free MS-Word-compatible word processor such as Jarte. You may also use iTunes and Quicktime, and a spreadsheet such as the ones built into the free LibreOffice and Kingsoft Office Free suites.
In recent years the Mac has become a target of more malware authors. In a March 21, 2014, post on the Sophos Naked Security blog, John Zorabedian describes five security tips for Mac users. One of the tips is to install a free antivirus program, such as Sophos's own Anti-Virus for Mac Home Edition.
Back in April 2012 I reviewed that program along with the donationware ClamXav.
In a November 14, 2014, post on his Krebs on Security blog, Brian Krebs explains that some telephone tech-support scammers claim to be Microsoft Certified Partners. Workers for one such company were recorded attempting to install a master password on a would-be victim's PC so they could exact a ransom from the owner to gain access to the machine.
Pull the plug on anyone claiming that you need them to fix your broken PC. Nine times out of 10, a software update, virus scan, and/or restart will correct any problem you encounter. If you can't repair the glitch yourself, ask a tech-knowledgeable friend or family member to take a look, or bring the computer to a reputable PC repair shop.
Generally speaking, telephone tech support is for the birds -- even the so-called legit phone-support services. You're better off doing it yourself, or having someone you know and/or trust do it for you.
-------------------------------------------------------
Safari offers all K-12 students free tech ebooks
Safari Books Online provides a catalog of thousands of tech titles whose topics are a glossary of cutting-edge technology. Now, as part of the White House's ConnectED program, O'Reilly Media is making all the Safari material available for free to every K-12 student in the country.
The rollout of Safari for Schools was scheduled to begin in January 2015, but last week Safari CEO Andrew Savikas announced that the first schools have already signed up for the program through the Edmodo service. The ultimate goal of the program is to make the entire Safari catalog of books and videos available for free to any K-12 student in the U.S.
My hat is off to Tim O'Reilly and everyone at O'Reilly Media. Their generosity will benefit all of us for years to come.
--------------------------------------------------------
Find out which apps are using up your iPhone's battery power
The September 15, 2014, Weekly described how a change in the default settings of Facebook's iPhone app caused videos to play automatically. This caused many people to reach and exceed the cell-data transmission limits of their accounts. The fix: Press Settings > Facebook > Settings > Auto-play > Wi-fi only (or Off). Alternatively, you can toggle the Use Cellular Data setting to disabled (gray).
A new feature of iOS 8.1 gives you the low-down on which iPhone apps are soaking up all the device's juice. The battery-usage tracker is one of the 11 tips in an October 31, 2014, article by Forbes' Jay McGregor. To open the battery tracker, press Settings > General > Usage > Battery Usage. After a few seconds, the apps are listed that use the most battery when the device isn't charging.
The scam begins when the victim downloads a "free" program that promises to scan their computer for viruses and performance problems. Of course, the malware always finds problems that can only be fixed by paying $30 to $50 for the full version of the program. When the victim runs the full version, they are instructed to call a toll-free number to "activate" the software. The person who answers uses "deceptive scare tactics," according to the FTC, to coerce the unwary downloader into buying support services they don't need.
Even worse, the company representatives may talk the poor soul into installing remote-control software on their system that gives the crooks unfettered access to the machine's contents. Then they open utilities on the computer such as the Windows Event Viewer in an attempt to fool the PC's owner into thinking there's something seriously wrong with the system. The "fixes" they claim are required cost as much as $500.
(Event Viewer nearly always includes some harmless cautions and warnings, designated with yellow exclamation marks and red "x"s.)
Don't share personal information with any strangers who call you
You know the rule about giving out personal information over the telephone: If you called the party, if you're confident the company is legitimate, and if you've dealt with the firm in the past, then you can probably share your street address (if necessary), telephone number, partial or full account number, and the last four digits of your Social Security number.
However, if the party called you, don't share even your name with them. In fact, you should be the one asking the questions: What is your name? What is your company's name? How did you get my telephone number? Where are you located? Who can I contact to verify your identity?
Even if your number is on the Federal Communication Commission's National Do Not Call Registry, you may receive unsolicited offers over the phone. The standard response is to politely interrupt the spiel and explain that you don't want to receive these calls, so please remove your number from their database. The telemarketers' scripts usually instruct them to tell you that it may take as long as 36 hours for the number to be removed.
Don't download or install any 'free' program you never heard of
Every modern Windows PC, Mac, and Chromebook ships with all the software required to operate it safely, although you may need to enable manually some security features that are off by default. In a September 19, 2014, post entitled "How to prevent malware and adware downloads," I explained how to ensure your Windows PC is protected. The information in the article refers to Windows 7, but it applies to Windows 8 as well.
The only other software you need is a browser such as Firefox, Google Chrome, or Opera; a free PDF reader such as Foxit Reader; and a free MS-Word-compatible word processor such as Jarte. You may also use iTunes and Quicktime, and a spreadsheet such as the ones built into the free LibreOffice and Kingsoft Office Free suites.
In recent years the Mac has become a target of more malware authors. In a March 21, 2014, post on the Sophos Naked Security blog, John Zorabedian describes five security tips for Mac users. One of the tips is to install a free antivirus program, such as Sophos's own Anti-Virus for Mac Home Edition.
Back in April 2012 I reviewed that program along with the donationware ClamXav.
In a November 14, 2014, post on his Krebs on Security blog, Brian Krebs explains that some telephone tech-support scammers claim to be Microsoft Certified Partners. Workers for one such company were recorded attempting to install a master password on a would-be victim's PC so they could exact a ransom from the owner to gain access to the machine.
Pull the plug on anyone claiming that you need them to fix your broken PC. Nine times out of 10, a software update, virus scan, and/or restart will correct any problem you encounter. If you can't repair the glitch yourself, ask a tech-knowledgeable friend or family member to take a look, or bring the computer to a reputable PC repair shop.
Generally speaking, telephone tech support is for the birds -- even the so-called legit phone-support services. You're better off doing it yourself, or having someone you know and/or trust do it for you.
-------------------------------------------------------
Safari offers all K-12 students free tech ebooks
Safari Books Online provides a catalog of thousands of tech titles whose topics are a glossary of cutting-edge technology. Now, as part of the White House's ConnectED program, O'Reilly Media is making all the Safari material available for free to every K-12 student in the country.
The rollout of Safari for Schools was scheduled to begin in January 2015, but last week Safari CEO Andrew Savikas announced that the first schools have already signed up for the program through the Edmodo service. The ultimate goal of the program is to make the entire Safari catalog of books and videos available for free to any K-12 student in the U.S.
My hat is off to Tim O'Reilly and everyone at O'Reilly Media. Their generosity will benefit all of us for years to come.
--------------------------------------------------------
Find out which apps are using up your iPhone's battery power
The September 15, 2014, Weekly described how a change in the default settings of Facebook's iPhone app caused videos to play automatically. This caused many people to reach and exceed the cell-data transmission limits of their accounts. The fix: Press Settings > Facebook > Settings > Auto-play > Wi-fi only (or Off). Alternatively, you can toggle the Use Cellular Data setting to disabled (gray).
A new feature of iOS 8.1 gives you the low-down on which iPhone apps are soaking up all the device's juice. The battery-usage tracker is one of the 11 tips in an October 31, 2014, article by Forbes' Jay McGregor. To open the battery tracker, press Settings > General > Usage > Battery Usage. After a few seconds, the apps are listed that use the most battery when the device isn't charging.
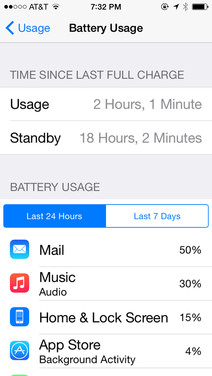
On my phone, the mail app was eating half the battery power. Since I open my phone's mail app about once a month and get an average of about zero important emails a day, I can nearly double my phone's battery life by disabling the mail app's push feature: Press Settings > Mail, Contacts, Calendars > Fetch New Data, and then toggle the Push setting to off.
With Push disabled, the account's Fetch setting is enabled, so your phone will apply its default Fetch setting. What's the difference between Push and Fetch? Pushes happen right away, and fetches are done on the schedule you set. The four Fetch options are Every 15 Minutes, Every 30 Minutes, Hourly, and Manually.
The only two options I need for most of my email are "Pitch" (as in "Delete") and "Retch" (as in "Delete with extreme prejudice").
With Push disabled, the account's Fetch setting is enabled, so your phone will apply its default Fetch setting. What's the difference between Push and Fetch? Pushes happen right away, and fetches are done on the schedule you set. The four Fetch options are Every 15 Minutes, Every 30 Minutes, Hourly, and Manually.
The only two options I need for most of my email are "Pitch" (as in "Delete") and "Retch" (as in "Delete with extreme prejudice").
