Menu
Internet companies' transparency reports indicate trademark abuse is on the rise
|
|
Trademark holders are overreaching in their takedown requests and using them to censor opinions and speakers they disagree with. Electronic Frontier Foundation's Parker Higgins explains in a September 17, 2014, article. They may also be trying to get an edge in the market by discouraging competition. A baked-goods company targeted people using the term "derby pie," which is a common dessert in the South. Denied by WordPress. Safe-harbor provisions of the Digital Millennium Copyright Act (DMCA) cause some Web services to comply with nearly all takedown requests automatically.
Good on the services that stand up for their customers despite the safe-harbor option! Twitter refuses almost one in four of the takedown requests it receives, Wikimedia less than one-half, and WordPress fewer than two-thirds. Not many services receive counter-notices from people accused of violating a trademark: the counter-notice process is complex, but mainly infringement penalties are stiff, and legal costs are high in any regard. It's cheaper just to comply with the takedown request. |
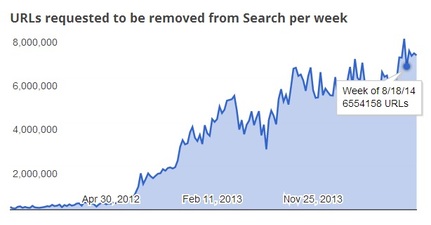
In its most recent transparency report, Google indicated that it now receives more than 7 million copyright takedown requests each week. That's nearly twice the number it fielded each week in mid-2013, and 10 times the number it recorded per week in 2012. Non-infringing use of another's trademark includes comparative advertising, criticism, comment, parody, news reporting, and fair use.
What's not fair use? "People Eating Tasty Animals" registered for the domain "PETA.org" and others related to PETA. (People for the Ethical Treatment of Animals v. Doughney) That's bad faith and attempt to profit -- the requirement under the Anti-cybersquatting Consumer Protection Act of 1999 (ACPA). What's not bad faith and attempt to profit:Lamparello v. Falwell Ministries. Owner of "Falwell.com" used it to counter the Reverend Jerry Falwell's preaching against homosexuality. He was awarded the domain name. Among the factors considered by the court were that the owner didn't misrepresent himself to the domain-name registrar, he included a link to the Reverend's site, and he placed a prominent disclaimer on the site. Throwing out one FRCP Rule 84 form could take a big bite out of patent abuse The Judicial Conference of the United States was expected to vote at its meeting last week on whether to recommend that Congress and the Supreme Court repeal Rule 84 of the Federal Rules of Civil Procedure. Forbes' Daniel Fisher explains in a September 12, 2014, article. The rule dates back to 1938 and allows a set of forms to be used to file a patent-infringement suit in federal courts. Patent trolls (a.k.a. "non-practicing entities") can thus assert patent claims against dozens, hundreds, even thousands of people by listing only the name of the patent holder, the date of the patent, and the name of the party accused of infringement. That's about all the trolly entities need to survive a motion to dismiss. If the form in question, Form 18, is abolished, the courts may use the stricter guidelines for suit as determined by the Supreme Court in the Ashcroft v. Iqbal (2009) and Bell Atlantic v. Twombly (2007) decisions (referred to as "Twiqbal"). A federal court in Virginia has already dismissed parts of a patent-infringement claim for lack of notice to the defendant about how the patent was infringed. If the change is enacted as expected, plaintiffs' complaints alleging patent infringement will need to identify the defendants' infringing products, state the specific patents being infringed, and explain how the products infringe. Currently patent holders often file suit in hopes of collecting money from defendants who simply want to avoid the higher costs of an ongoing legal battle. Now they'll have to spend more money up front and will have a lower chance of a quick payday. Add this change to the tighter restrictions of the AIA, and you got a good start on patent reform. (Bonus #1: Filing a motion to amend a patent claim in AIA trials: How to improve your slim chances of winning the right to amend your claim. National Law Review, September 25, 2014) Campaign finance disclosure laws can backfire In a September 19, 2014, post on the Global Anticorruption Blog, Professor Michael Gilbert of the University of Virginia Law School explains how campaign contribution disclosure laws can backfire. A congresswoman used the disclosure information to solicit campaign contributions from a corporation that had contributed to other Congress members on one of her subcommittees. That subcommittee was working on legislation that directly affected the company from which she was soliciting "campaign contributions." Ugh! Damage a reputation in a blog comment, get sued for defamation A Canadian court ruled that a comment to a blog post can damage a person's reputation sufficiently to qualify for defamation. The case in question is Baglow v. Smith. Mark A.B. Donald and Grant Buckler report in an April 9, 2013, article on Canadian Journalists for Free Expression. The case is also examined by Jameel Mahdany and Brian Radnoff in aSeptember 17, 2014, article on JDSupra Business Advisor. For a statement to be defamatory, 1) it has to be published; 2) the person posting has to know it's untrue, should know it's untrue, or have blatant disregard for the truth; and 3) the statement has to damage the target's reputation. The comment in question accused the writer of being "one of the Taliban's more vocal supporters." The trial court ruled the comment qualified as "published" but granted defendant's summary judgment because there was no damage to the writer's reputation. Appellate overruled and said whether there was reputation damage was up to the trier of fact. (Bonus #2: Global data residency rules: A vote for Binding Corporate Rules, which make it simpler to comply with data protection laws such as the European Union's Data Protection Directive. There are now 125 countries that restrict movement of data outside their boundaries. Phil Lee, FieldFisher Privacy and Information Law Blog, September 13, 2014.) |
