Menu
|
The end is near for passwords (not really)
|
The weak link in nearly every data-security plan is us. We rely on passwords to prove we are who we say we are and merit access to whatever system or service we’re signing into. Stolen passwords remain the most popular way for criminal hackers to gain unauthorized access to the many networks and systems we’ve come to rely on in our work and leisure lives.
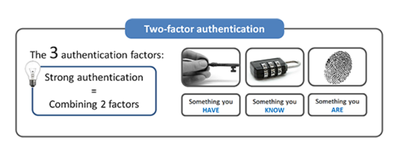
To combat this trend, two-factor authentication continues to pick up steam. It combines a user ID/password combination with another form of validation, usually a mobile phone or a USB key, to confirm our identity. In a February 3, 2016, article on Secure ID News, Dovell Bonnett points out that what some people call two-factor is actually “double single factor.” For example, if you present a photo ID such as a driver’s license, plus a credit card with your name, you’re using two things you have, or “have-have” authentication. Bonnett calls this “multiple single-factor authentication,” which is safer than single-factor but not as safe as two-factor. What distinguishes true two-factor authentication is combining something you have with something you are (biometrics) and/or something you know, such as a password or passcode. Increasingly, mobile phones are the key to providing the “have,” “are,” and “know” components of two-factor authentication. The usual methods are to send a code to the device via text message, scan your fingerprint, analyze a picture you take of your face, or apply some other biometric measure. Meanwhile, the World Wide Web Consortium (W3C) is working on a password-free authentication system based on public and private cryptographic keys. Rawlson King reports on the project in a February 18, 2016, article on Biometric Update. When you attempt to access a service, it sends a public-key “challenge” to your device, and your response has to be “signed” by your private key. As long as access to your device is secured – either by a password/passcode or a biometric reader – then access to the services and networks you sign into is secured. Other organizations working on a building a better authentication mousetrap include the Los Alamos National Laboratory, the Lawrence Livermore National Laboratory, and the Oak Ridge National Laboratory, all of which have licensed their authentication technologies to private security vendors for use in future products. Laboratory Equipment’s Joe Dysart reports on these efforts and similar projects underway at Yahoo, Google, Microsoft, Intel, and other vendors in a February 22, 2016, article. You can bet your favorite pair of hiking boots that your great-grandchildren will be using some variation of password to prove their identity. Fortunately, the password won’t be the only thing they’ll use to authenticate themselves to their robot overlords (just kidding… I think). |
