Menu
Tech shorts: A language-translation browser extension, two new ways to protect data, and a documentary that helps you track the trackers
Learn a new language while you browse
Sometimes I think I'm engaged in the world's most-protracted language-learning program. I studied Spanish in high school, then moved on to other languages in college as I earned my undergrad degree in Linguistics. But off and on through the years I have returned to learning Spanish, primarily through a CD-based language-instruction program. (Secondarily through regular visits to our wonderful taquerias here in Santa Rosa.)
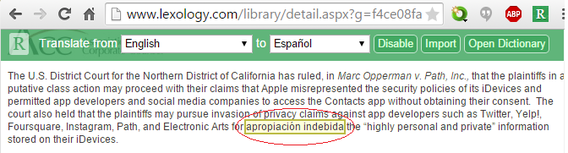
Now I can brush up on my dusty, rusty Spanish while I browse. The Readlang extension for Google's Chrome browser and its accompanying website translate words and phrases in dozens of languages. I'm using the Chrome extension, which places a green "R" icon in the top-right corner of the window. Click it to open a translation bar across the top of the screen.
Once the translation bar is enabled, words on the page are highlighted as you mouse over them. Choose a word or phrase to see the translation. (Note that translating phrases requires signing into a Google account or creating an email account on the Readlang site.)
The free version offers unlimited translations of single words and translations of up to 10 phrases each day. Unlimited phrase translations cost $24 per year.
-------------------------------------------------------------------------------
Two new methods for protecting data: One hides it, the other tracks breaches in near-real-time
Encryption: It's the wave of the future, the wave of the future, the wave of the future, the wave of the future....
With apologies to Martin Scorsese's fictionalized version of Howard Hughes in "The Aviator," allow me to repeat myself over and over by reiteratingly saying the same thing I just said time and again. Last week's Weekly looked at the prospect of end-to-end encryption being offered on the web. A company called Ionic Security has developed software that encrypts all of an organization's data, all the time, except when the specific file is opened by an authorized user on an authorized computer or device. MIT Technology Review's Tom Simonite describes the technology in an April 14, 2015, article.
The company claims its product allows you to decrypt only some portions of a document or file, leaving other parts that the user isn't privy to encrypted. Simonite points to some of the technology's downsides: It requires an Internet connection, so you can't view files offline; the connection has to be authorized beforehand, so no ad-hoc network access is possible; and the encryption system itself could be hacked.
That's where another recent security innovation comes into play. A company called Tanium has created software that can show the status of every Internet connection on a network almost instantaneously. Forbes' Brian Solomon writes about the company in an April 15, 2015, article.
Tanium is based on what Solomon calls a new type of peer-to-peer network in which each computer/node communicates with its neighbor to pass information along a chain that leads to the central monitoring server. Network status reports that previously took hours or days to complete can now be generated in a few seconds, according Solomon. The goal is for network managers to be notified within seconds of any potential data breach. The quicker they can respond, the less damage an attacker can inflict on their networks.
The company is working to scale up to support the largest enterprise networks. Its current customer list includes Visa, Amazon, Best Buy, Nasdaq, and the U.S. Department of Defense. It also benefits from some very deep-pocket investors, including Marc Andreessen and Ben Horowitz.
It appears companies of all types and sizes are getting serious about security -- and not a moment too soon.
--------------------------------------------------------------------------
An interactive look at the web's many trackers
You know your web activities are tracked and recorded, and for the most part, you don't care. But do you really know what's being tracked, who's doing the tracking, and what they're doing with the information they collect about you?
An "online interactive documentary" entitled Do Not Track debuted recently at the Tribeca Film Festival New York, as Forbes' Joseph Steinberg describes in an April 16, 2015, article. Creator and director Brett Gaylor, who previously worked for the Mozilla Foundation, intends the series to educate web users about the dangers of being tracked, and about how they can limit the tracking.
The problem is, most anti-tracking techniques are difficult to implement and ultimately ineffective. For example, the "do not track" option in popular browsers is voluntary: sites can ignore the setting if they wish and track you all they want. Also, methods such as device fingerprinting render other tracker-blocking approaches all but useless.
The best way to protect your privacy online, along with blocking ads and third-party cookies, is simply to refrain from sharing personal information via social networks and other web services. You'll still be tracked, but at least you can limit what the trackers know about you.
Sometimes I think I'm engaged in the world's most-protracted language-learning program. I studied Spanish in high school, then moved on to other languages in college as I earned my undergrad degree in Linguistics. But off and on through the years I have returned to learning Spanish, primarily through a CD-based language-instruction program. (Secondarily through regular visits to our wonderful taquerias here in Santa Rosa.)
Now I can brush up on my dusty, rusty Spanish while I browse. The Readlang extension for Google's Chrome browser and its accompanying website translate words and phrases in dozens of languages. I'm using the Chrome extension, which places a green "R" icon in the top-right corner of the window. Click it to open a translation bar across the top of the screen.
Once the translation bar is enabled, words on the page are highlighted as you mouse over them. Choose a word or phrase to see the translation. (Note that translating phrases requires signing into a Google account or creating an email account on the Readlang site.)
The free version offers unlimited translations of single words and translations of up to 10 phrases each day. Unlimited phrase translations cost $24 per year.
-------------------------------------------------------------------------------
Two new methods for protecting data: One hides it, the other tracks breaches in near-real-time
Encryption: It's the wave of the future, the wave of the future, the wave of the future, the wave of the future....
With apologies to Martin Scorsese's fictionalized version of Howard Hughes in "The Aviator," allow me to repeat myself over and over by reiteratingly saying the same thing I just said time and again. Last week's Weekly looked at the prospect of end-to-end encryption being offered on the web. A company called Ionic Security has developed software that encrypts all of an organization's data, all the time, except when the specific file is opened by an authorized user on an authorized computer or device. MIT Technology Review's Tom Simonite describes the technology in an April 14, 2015, article.
The company claims its product allows you to decrypt only some portions of a document or file, leaving other parts that the user isn't privy to encrypted. Simonite points to some of the technology's downsides: It requires an Internet connection, so you can't view files offline; the connection has to be authorized beforehand, so no ad-hoc network access is possible; and the encryption system itself could be hacked.
That's where another recent security innovation comes into play. A company called Tanium has created software that can show the status of every Internet connection on a network almost instantaneously. Forbes' Brian Solomon writes about the company in an April 15, 2015, article.
Tanium is based on what Solomon calls a new type of peer-to-peer network in which each computer/node communicates with its neighbor to pass information along a chain that leads to the central monitoring server. Network status reports that previously took hours or days to complete can now be generated in a few seconds, according Solomon. The goal is for network managers to be notified within seconds of any potential data breach. The quicker they can respond, the less damage an attacker can inflict on their networks.
The company is working to scale up to support the largest enterprise networks. Its current customer list includes Visa, Amazon, Best Buy, Nasdaq, and the U.S. Department of Defense. It also benefits from some very deep-pocket investors, including Marc Andreessen and Ben Horowitz.
It appears companies of all types and sizes are getting serious about security -- and not a moment too soon.
--------------------------------------------------------------------------
An interactive look at the web's many trackers
You know your web activities are tracked and recorded, and for the most part, you don't care. But do you really know what's being tracked, who's doing the tracking, and what they're doing with the information they collect about you?
An "online interactive documentary" entitled Do Not Track debuted recently at the Tribeca Film Festival New York, as Forbes' Joseph Steinberg describes in an April 16, 2015, article. Creator and director Brett Gaylor, who previously worked for the Mozilla Foundation, intends the series to educate web users about the dangers of being tracked, and about how they can limit the tracking.
The problem is, most anti-tracking techniques are difficult to implement and ultimately ineffective. For example, the "do not track" option in popular browsers is voluntary: sites can ignore the setting if they wish and track you all they want. Also, methods such as device fingerprinting render other tracker-blocking approaches all but useless.
The best way to protect your privacy online, along with blocking ads and third-party cookies, is simply to refrain from sharing personal information via social networks and other web services. You'll still be tracked, but at least you can limit what the trackers know about you.
