Menu
How to deter 'fingerprint' trackers from identifying your computers and devices |
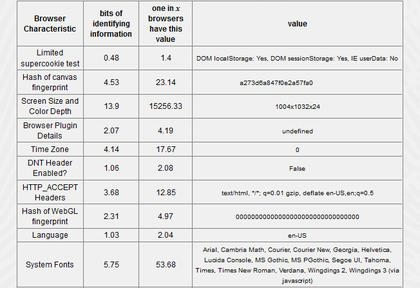 Source: no-sec.org - https://no-sec.net/fingerprinting-of-web-browsers-and-the-consequences-for-privacy/ Source: no-sec.org - https://no-sec.net/fingerprinting-of-web-browsers-and-the-consequences-for-privacy/
Your real fingerprint can be scanned to identify you to your phone or other device. That fingerprint you know about.
There's another kind of "fingerprint" left by your system or device as you traipse around the internet. This one identifies you to the sites, ad networks, and other parties that track, record, and profit from your online activities. When it comes to real fingerprints, there's good news for privacy fans. Apple announced recently that the next version of iOS will let users disable temporarily an iOS device's fingerprint reader so the only way to access the device is by entering a passcode or passphrase. (Tom Warren describes this and other new iOS security features in an August 17, 2017, article on the Verge.) The courts have ruled that government officials can order you to place your finger on the device's scan button to provide the government with access to the device's applications and data. However, the government can't demand that you disclose your passcode or passphrase. This ruling is similar to previous court decisions that found Fifth Amendment protections against self-incrimination apply only to oral statements. You could be required to speak solely to allow a witness to confirm that the voice they heard was yours. You may also be required to supply a blood sample or fingerprints, or to walk or perform other acts that could help a witness identify you. Michael Izzi explains the limits of compelled self-incrimination in an article on LegalMatch. You can block some trackers, but not all of them A new form of digital "fingerprinting" poses a different kind of threat to our privacy. Last week's Weekly referred to a recent paper written by Princeton University researchers Steven Englehardt and Arvind Narayanan on the dangers of system fingerprinting by web services and ad networks (pdf). The researchers recommend the free tracker-blocking browser extensions Ghostery and uBlock Origin as a way to stymie the trackers. Canvas fingerprinting is particularly popular with trackers because it makes it easier to identify an individual out of the millions of system profiles a tracker may collect. As explained in a post on the Multiloginapp blog, canvas fingerprinting relies on the Canvas element in HTML 5 that your browser uses to "draw" an image on a web page. If you block this element, you stand out in a crowd as "tech-savvy." In these cases, other less-certain fingerprinting methods can be applied to identify you. Another way to prevent canvas fingerprinting is to generate random canvas fingerprints during your browser session. Unfortunately, a changing fingerprint also sets you apart from the millions of visitors whose fingerprints never change. Multiloginapp recommends the Canvas Defender extension that's available for Firefox and for Chrome. I haven't tested the plug-in, and commenters to the Multiloginapp post highlight several shortcomings with the technique the program uses to block tracking by canvas fingerprinting. According to Christopher Harper in an April 6, 2016, article on MakeTechEasier, the best way to prevent fingerprint tracking is by using the anonymizing Tor browser. My concern about Tor is that it gives people a false sense of security because the browser has been hacked in the past -- most notably by the FBI -- and will be again. In an August 7, 2017, post on the Merkle, JP Buntinx reports on "major changes" to Tor software expected soon. The 'good enough' tracker-blocking tool Two other fingerprint-blocking techniques recommended by Harper are much easier to implement, although they won't prevent all such tracking. The Electronic Frontier Foundation's free Privacy Badger is available for Firefox and Chrome. (Note that Harper claims the program requires some "additional configuration." I have used Privacy Badger for a long time, and very rarely do I find it necessary to disable the program for a page to load correctly.) The free Disconnect tool helps hide you from fingerprint trackers and also provides an ad blocker. The program is available for free, and also in $25 Pro and $50-per-year Premium versions (Premium protects up to three devices.) There is a relatively simple way to prevent tracking via fingerprinting: Block Javascript. I used to recommend the NoScript browser extension that lets you decide when to allow Javascript to run on a site, but blocking Javascript renders the web unusable, even when you enable Javascript on a site-by-site basis. In this case, I choose to rely on the good-enough protection against fingerprint tracking that the EFF's Privacy Badger offers. Spread the tracking around by using multiple browsers A simple way to minimize the amount of information trackers collect about you is to use different browsers for different services. For example, I use the Opera browser whenever I need to sign into a Google account, Safari to access my web hosting service, and Firefox for signing into my Outlook.com email account, which is linked to my Gmail address. This way, I can access my Gmail messages without having to stay logged into a Google account. An ancient CNET post of mine describes how to forward Gmail messages to other mail services. Does Google still track me? Oh, you betcha! But the dossier Google keeps on me is much less detailed than it would be otherwise. To find out what Google knows about you, follow Michael Andronico's instructions in a June 29, 2016, article on Tom's Guide for using Google's My Activity dashboard. The dashboard can be used to delete some or all of your Google profile. Bonus tip #1: A great way to limit web tracking is to log out of Google, Facebook, and other services when you're not using them. Bonus tip #2: When you're ready to get really, really serious about protecting your privacy, check out the Privacy Kit, which offers 52 different activities for keeping the details of your personal life away from snoops. Each activity is said to take no longer than a half hour to complete, though the advice to "get a shredder" seems to me like an invitation to a massive time-sink. The site also offers a great list of recommended reading on various privacy topics. ----------------------------------------------- 'Corporate tyranny and the death of democracy' Chris Hedges is at it again. In a very long August 21, 2017, post on Common Dreams (originally published on August 20, 2017, on TruthDig), Hedges places the blame for the collapse of democracy in the U.S. squarely on the legal profession, which has abdicated its duty to "protect the public from the tyranny of corporate elites." It's not as if we weren't warned that a corporate takeover of our country would happen. Hedges profiles Harlan Fiske Stone, U.S. Supreme Court justice from 1925 to 1946 and chief justice from 1941 to 1946. Hedges describes Stone's brand of conservatism as believing "the law is designed to protect the weak from the powerful." This is 180 degrees from the tenets of the Federalist Society, which currently controls appointments to the federal judiciary. According to numbers from the Alliance for Justice, corporate attorneys and government prosecutors represent 85 percent of President Barack Obama's judicial nominees. In contrast, only 4 percent of the nominees have public interest backgrounds, and another 4 percent have represented workers in labor disputes. Don't expect the percentages to turn around during a Republican hegemony. Hedges blows out of the water the myth of "liberal" and "conservative" justices, describing it as "a naked tool of corporate oppression." "The self-identified 'liberals' in the judiciary, while progressive on social issues such as abortion and affirmative action, serve corporate power as assiduously as the right-wing ideologues of the Federalist Society.... "The most basic constitutional rights—privacy, fair trials and elections, habeas corpus, probable-cause requirements, due process and freedom from exploitation—have been erased for many, especially the 2.3 million people in our prisons, most having been put there without ever going to trial. Constitutionally protected statements, beliefs and associations are criminalized. Our judicial system, as Ralph Nader has pointed out, has legalized secret law, secret courts, secret evidence, secret budgets and secret prisons in the name of national security. "Our constitutional rights have steadily been stripped from us by judicial fiat.... [O]ur telephone calls and texts, emails and financial, judicial and medical records, along with every website we visit and our physical travels, can be and commonly are tracked, recorded, photographed and stored in government computer banks." The people behind the Federalist Society are conservative law professors, corporate attorneys, and conservative judges, as Eric Lipton of the New York Times stated in a Democracy Now broadcast on March 21, 2017. According to Hedges, the group "has close ties with the American Legislative Exchange Council (ALEC), whose lobbyists draft and push corporate-sponsored bills through state legislatures and Congress." The Federalist Society wants to see the "fossilization" of the law to the pre-industrial times of the late 18th century, according to Hedges. By contrast, Stone believed that if the Constitution is used solely to protect "individualism" as it was in the "agrarian, white male, slave-holding society" in which it was written, there would be "no legal mechanisms" to thwart the "abuse of corporate power." Hedges concludes that Stone's "worst fears are our nightmare." ----------------------------------------------- Speaking of nightmares (or maybe bad science fiction), it's almost as if nature, in its infinite wisdom, has determined that humans pose a threat to life on earth. To eliminate the threat, nature has found a way to turn us against ourselves. We are acting in ways that are guaranteed to bring about our annihilation. Once we wipe ourselves out, life will once again thrive on the planet. Great movie. Too bad nobody will be around to make it. (Or watch it. Or violate its copyright. Or parody it. Or turn into a Netflix series.) Somebody wake me up! |
