Menu
Quick, simple fixes for everyday tech glitches -- plus three preventive measures
Stuff doesn't always work the way it's supposed to. When one of your tech gadgets starts acting up, here's a three-step troubleshooting protocol:
1) Whenever a computer or device hiccups, turn it all the way off, wait a few seconds, and then turn it back on.
2) If a restart doesn't fix the problem, update your software -- apps and OS -- if any updates are available. (Your software should be set to update automatically, but every now and then an update doesn't get applied, for some reason.) After applying the update, try another restart.
3) If all the software is up-to-date and the problem persists, scan for malware with the free Malwarebytes program for PCs, or the free version of the Lookout security program for iPhones, Android phones, and Windows phones. (Make sure you update the security program's virus definition and other features before you run the scan.)
As hardware and software have become more reliable over the years, the chances increase that a tech problem is related to a security breach. The recent Poodle virus is an example of malware persistence: the bug takes advantage of a vulnerability in an outdated version of the Secure Sockets Layer (SSL) protocol. In an October 17, 2014, article, Readwrite's David Hamilton explains how to defend against Poodle.
Here are the three best ways to prevent a security breach:
1) Don't use public Wi-Fi hotspots -- ever. Okay, sometimes you have to use a public access point, but when you do, assume you're being surveilled and don't sign into your bank, Amazon, or other commerce site. Also be cautious about signing into an email account unless the connection is encrypted using a service such as the free Security KISS virtual private network software.
2) Back up all your files to a cloud storage service or external media. You know ransomware has gone mainstream when it becomes a subplot in a TV drama series. The October 19, 2014, episode of CBS's The Good Wife had the heroine attorney's law offices paying a $50,000 ransom to some Russian malware purveyor to unlock their office computers. (The same day, a local newspaper columnist wrote about having lost his files to ransomware.)
If you keep up-to-date copies of your files on a cloud storage service or an external drive, you can thumb your nose at the extortionists (which always brings to mind a circus performer tied in knots -- or maybe the person who unties them). Or skip the middleman and store your files in the cloud or to an external medium.
Make sure to encrypt both the network connection and your cloud account. The best option are services such as SpiderOak that encrypt the data on your local machine, which theoretically prevents any SpiderOak employees from gaining access to it. (SpiderOak offers 2GB of free cloud storage and up to 100GB of storage for $10 a month.)
Then if you ever become a ransomware victim, you may still have to reinstall your OS and applications to rid yourself of the infection, but at least you haven't lost your files.
3) Think twice before you click. And think three times before you click an email link. Social engineering remains the primary method used by bad guys to get into your system. That means they trick you -- usually getting you to click a link you think is safe but actually downloads and installs malware. It is the oldest and most successful trick in the cyber-criminal's book.
1) Whenever a computer or device hiccups, turn it all the way off, wait a few seconds, and then turn it back on.
2) If a restart doesn't fix the problem, update your software -- apps and OS -- if any updates are available. (Your software should be set to update automatically, but every now and then an update doesn't get applied, for some reason.) After applying the update, try another restart.
3) If all the software is up-to-date and the problem persists, scan for malware with the free Malwarebytes program for PCs, or the free version of the Lookout security program for iPhones, Android phones, and Windows phones. (Make sure you update the security program's virus definition and other features before you run the scan.)
As hardware and software have become more reliable over the years, the chances increase that a tech problem is related to a security breach. The recent Poodle virus is an example of malware persistence: the bug takes advantage of a vulnerability in an outdated version of the Secure Sockets Layer (SSL) protocol. In an October 17, 2014, article, Readwrite's David Hamilton explains how to defend against Poodle.
Here are the three best ways to prevent a security breach:
1) Don't use public Wi-Fi hotspots -- ever. Okay, sometimes you have to use a public access point, but when you do, assume you're being surveilled and don't sign into your bank, Amazon, or other commerce site. Also be cautious about signing into an email account unless the connection is encrypted using a service such as the free Security KISS virtual private network software.
2) Back up all your files to a cloud storage service or external media. You know ransomware has gone mainstream when it becomes a subplot in a TV drama series. The October 19, 2014, episode of CBS's The Good Wife had the heroine attorney's law offices paying a $50,000 ransom to some Russian malware purveyor to unlock their office computers. (The same day, a local newspaper columnist wrote about having lost his files to ransomware.)
If you keep up-to-date copies of your files on a cloud storage service or an external drive, you can thumb your nose at the extortionists (which always brings to mind a circus performer tied in knots -- or maybe the person who unties them). Or skip the middleman and store your files in the cloud or to an external medium.
Make sure to encrypt both the network connection and your cloud account. The best option are services such as SpiderOak that encrypt the data on your local machine, which theoretically prevents any SpiderOak employees from gaining access to it. (SpiderOak offers 2GB of free cloud storage and up to 100GB of storage for $10 a month.)
Then if you ever become a ransomware victim, you may still have to reinstall your OS and applications to rid yourself of the infection, but at least you haven't lost your files.
3) Think twice before you click. And think three times before you click an email link. Social engineering remains the primary method used by bad guys to get into your system. That means they trick you -- usually getting you to click a link you think is safe but actually downloads and installs malware. It is the oldest and most successful trick in the cyber-criminal's book.
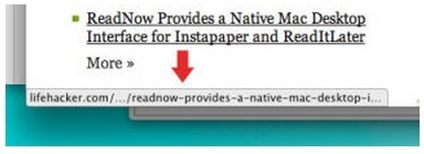
As Lifehacker's Adam Dachis explains in an October 17, 2014, article, hover over a link before you click it to see its real URL in the status bar at the bottom of the browser window. Rather than clicking the link, enter the URL in the browser address bar manually, or go to the company's home page and search for whichever page the email purports to link to.
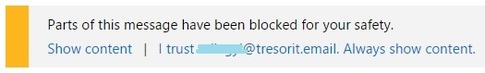
Most browsers disable active elements in email by default -- at least until you've indicated the sender is trustworthy. Also make sure your browser's built-in phishing-detection features and other security options are enabled via Settings > Security (or some variation of those menu options).
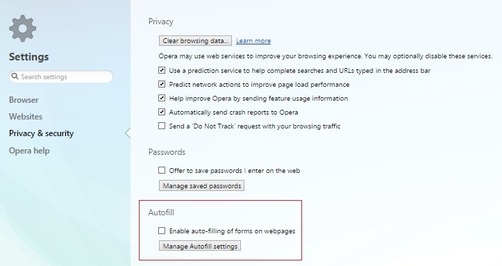
While you're in your browser's settings, be sure to disable the save-passwords option and auto-fill feature for forms. Crooks are able to collect the personal information stored in auto-fill fields.
Last but not least, get the free Web of Trust plug-in, which is available for all popular browsers. WoT puts an icon next to links in search results and elsewhere to indicate whether they're safe (green), dangerous (red), or something in between (yellow or question mark). WoT was one of the security add-ons I covered in the September 9, 2014, article "Three free browser add-ons protect against cyber-crime."
Last but not least, get the free Web of Trust plug-in, which is available for all popular browsers. WoT puts an icon next to links in search results and elsewhere to indicate whether they're safe (green), dangerous (red), or something in between (yellow or question mark). WoT was one of the security add-ons I covered in the September 9, 2014, article "Three free browser add-ons protect against cyber-crime."
